Safety info and occasion administration (SIEM) is a tool and environmental evaluation technique supposed to assist safe and defend firm operations, information and personnel. By offering a complete evaluation of security-related particulars and associated suggestions, SIEM instruments help by way of making certain compliance and remediating potential or energetic threats.
SEE: Brute Drive and Dictionary Assaults: A Information for IT Leaders (TechRepublic Premium)
A current report revealed by the IMARC Group discovered that the worldwide SIEM market reached nearly $5.8 billion in 2023. The identical report says the market is anticipated to climb to round $14 billion, particularly with extra corporations investing extra assets in defending towards potential threats and resolving vulnerabilities.
With that in thoughts, we check out one of the best SIEM instruments and SIEM software program options obtainable right now.
Graylog
Workers per Firm Dimension
Micro (0-49), Small (50-249), Medium (250-999), Giant (1,000-4,999), Enterprise (5,000+)
Medium (250-999 Workers), Giant (1,000-4,999 Workers), Enterprise (5,000+ Workers)
Medium, Giant, Enterprise
Options
Anomaly Detection, Audit Logs, Compliance Reporting, and extra
ManageEngine Log360
Workers per Firm Dimension
Micro (0-49), Small (50-249), Medium (250-999), Giant (1,000-4,999), Enterprise (5,000+)
Micro (0-49 Workers), Small (50-249 Workers), Medium (250-999 Workers), Giant (1,000-4,999 Workers), Enterprise (5,000+ Workers)
Micro, Small, Medium, Giant, Enterprise
Options
Exercise Dashboard, Superior Risk Analytics, Analytics/Reporting, and extra
High SIEM software program comparability
These wishing to undertake SIEM or planning to improve a legacy SIEM software to a contemporary platform ought to rigorously consider the obtainable instruments. Options corresponding to cloud and on-prem performance, remediation capabilities and the platforms supported needs to be among the many high areas to be thought-about.
| Cloud | Hosted on-prem | Remediation | Platforms | Pricing | |
|---|---|---|---|---|---|
| SolarWinds SEM | Sure | Sure | Consists of some automated remediation options. | Home windows, Linux and Mac. | Begins at $2,992 |
| CrowdStrike Falcon LogScale | Sure | No | Full vary of remediation capabilities. | Home windows, Linux, Mac and Chrome. | Contact for quote |
| Splunk Enterprise Safety | Sure | No | Some remediation capabilities. | Home windows, Linux and Mac. | Reportedly $173 per 30 days as much as $1,800 per GB |
| Datadog Safety Monitoring | Sure | No | Restricted remediation capabilities. | Home windows, Linux and Mac. | Begins at $15 per host, per 30 days |
| LogRhythm SIEM | Sure | Sure | Restricted remediation capabilities. | Home windows, Linux and Mac. | Contact for quote |
| RSA NetWitness SIEM | Sure | Sure | Restricted remediation capabilities. | Home windows, Linux and Mac. | Contact for quote |
| ManageEngine Log360 | Sure | Sure | Restricted remediation capabilities | Home windows, Linux and Mac. | Customized quote by way of on-line type |
| IBM Safety QRadar SIEM | Sure | Sure | Full remediation capabilities. | Home windows, Linux and Mac. | Customized quote by way of on-line value estimator |
| Trellix Enterprise Safety Supervisor | Sure | Sure | Remediation capabilities solely obtainable with buy of further Trellix modules. | Home windows, Linux and Mac. | Contact for quote |
| AT&T USM Anyplace | Sure | No | Remediation included | Home windows, Linux and Mac. | Begins at $1,075 per 30 days |
SolarWinds: Greatest for log aggregation

SolarWinds Safety Occasion Supervisor (SEM) is concentrated on log aggregation and risk detection. It will possibly simply course of and ahead uncooked occasion log information to exterior functions for additional evaluation utilizing syslog protocols, which is an space the place it stands out from the competitors.
Why I picked SolarWinds
I picked SolarWinds for its intensive log aggregation and log evaluation performance. This enables companies to know the precise state of their units, discover the root-cause of every log and consequently implement methods to enhance the identical. SolarWinds’ means to share huge quantities of log information to different functions is a major plus as effectively.
Pricing
- SolarWinds annual SEM subscriptions begin at $2,992.
- Perpetual licensing is obtainable for round $6,168.
Options
- Automation to remediate some incidents.
- Export log information and share with different groups or distributors.
- Dashboards point out the state of safety, and reviews handle compliance necessities.
- Pre-built connectors pull information from quite a few sources.
- A file integrity checker tracks entry and adjustments made to information and folders to detect unauthorized or malicious exercise.
Determine A
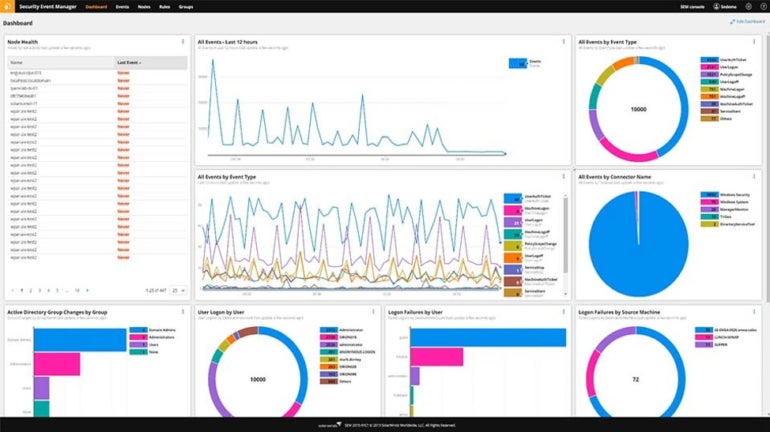
Integrations
- Amazon Net Companies.
- Azure.
- Heroku.
- Apache.
- Oracle.
Professionals
- Good for network-related occasions and analyzing per-host actions, corresponding to logons, privilege utilization and registry alterations.
- Safety features embody information encryption, single sign-on and good card authorization.
- Potential to limit entry from IPs, block functions and deny entry to detachable media.
Cons
- Dashboards can turn into cluttered and exhausting to grasp when processing giant quantities of knowledge.
- Can wrestle with the complexity of very giant enterprise environments.
- Automated doesn’t present a full vary of remediation capabilities.
Splunk Enterprise Safety: Greatest for cloud native environments

Splunk Enterprise Safety affords cloud-based security-related occasion notifications and log monitoring. It will possibly establish useful resource bottlenecks, failing {hardware}, capability points and different potential points. Because it advanced within the period of the cloud, it’s significantly effectively suited to cloud-native environments.
Why I picked Splunk Enterprise Safety
Splunk Enterprise Safety obtained on this record for being specifically outfitted with defending cloud environments. It allows cloud-native organizations to simply set up safety monitoring and unified visibility within the cloud. Its complete visibility capabilities are coupled with 1,500+ detections, hundreds of integrations and risk-based alerting. Splunk’s unified risk detection, investigation and response service is a safety software that many cloud-native corporations ought to take into account.
Pricing
- Splunk’s complicated pricing construction is break up into entity, exercise, workload and ingest classes.
- Splunk doesn’t publish precise costs, however person reviews place them anyplace from $173 per 30 days as much as $1,800 per GB.
Options
- Risk detection with machine studying, together with 1,400 detections for frameworks corresponding to MITRE and others.
- Ingest and monitor tens of terabytes of knowledge per day from any supply, structured or unstructured.
- Attribute threat to customers and techniques, map alerts to cybersecurity frameworks and set off alerts when threat exceeds thresholds.
- Examine safety occasions or suspicious exercise quickly.
Determine B
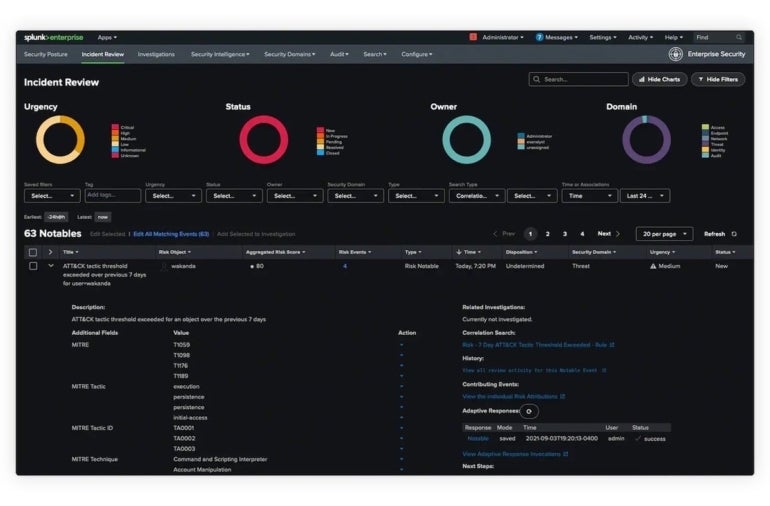
Integrations
- AWS.
- Azure.
- Google Cloud Platform.
- Kubernetes.
- OpenShift.
- Kafka.
Professionals
- Triggers that reply to logged conditions with personalized response patterns.
- Analytics capabilities are in-built, which might produce long-term graphs.
- View a variety of logs and drill down into particular occasions or information sources.
- Potential to resolve issues throughout a number of platforms.
Cons
- Some customers take into account Splunk to be costly when monitoring giant quantities of knowledge in main enterprise environments.
- The corporate’s not too long ago introduced acquisition by Cisco could result in lengthy integration delays and lack of progress on its innovation roadmap.
Datadog Safety Monitoring: Greatest for personalization

Datadog has designed its platform to be extremely customizable to person wants. Datadog Safety Monitoring makes it comparatively straightforward to see at a look what’s taking place with all sources being analyzed. It affords safety monitoring for dynamic environments, real-time safety monitoring instruments and root trigger evaluation performance. There’s additionally a free trial that lets group’s take a look at drive Datadog to see if it matches their wants and necessities.
Why I picked Datadog Safety Monitoring
I selected Datadog Safety Monitoring for its robust emphasis on user-configuration and customizability. Specifically, organizations can make the most of Datadog’s configurable guidelines to trace down widespread attacker conduct and methods. It’s also possible to customise which logs you wish to index as you proceed to ingest and course of information. That is on high of getting a customizable dashboard and person interface.
Pricing
- The professional model prices $15 per host per 30 days, and the enterprise model is $23 per host per 30 days.
Options
- Over 350 detection guidelines and greater than 500 integrations with log sources present full visibility into safety operations.
- Potential to see inside any stack or software at any scale and anyplace.
- Infrastructure monitoring, APM, log administration, machine monitoring, cloud workload monitoring, server monitoring and database monitoring, all included.
- Assemble information from logs and different metrics to supply context and decrease incident response time.
Determine C
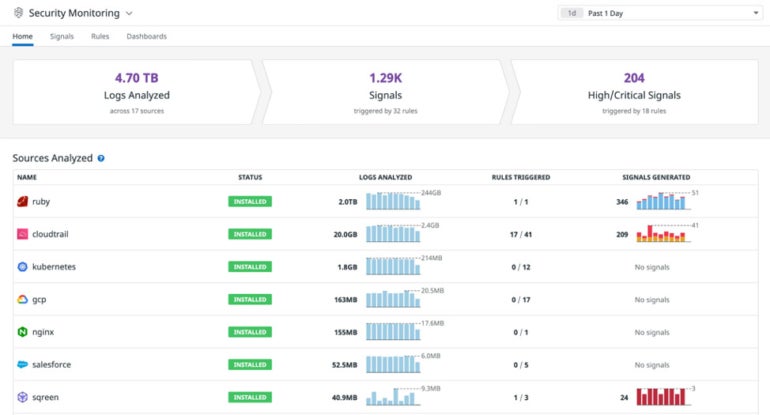
Integrations
- Slack.
- SSH.
- AWS.
- Google Cloud Platform.
- Oracle.
- IBM Cloud.
Professionals
- Datadog takes a monitoring strategy geared towards analytics and is favored by DevOps and IT to handle cloud and infrastructure efficiency.
- Datadog set up is simple, courtesy of agent deployment.
- Dashboards and interfaces are straightforward to customise.
Cons
- Datadog stops wanting calling itself a whole SIEM platform, as it’s extra centered on cloud monitoring and safety however has been increasing its cloud SIEM capabilities.
- Datadog lacks a few of the log monitoring capabilities of full-featured SIEM platforms.
LogRhythm SIEM: Greatest for on-premises

LogRhythm’s SIEM software program is designed to be hosted on-premises. It has constructed AI and automation options into its platform. Reporting primarily based on queries is straightforward to configure. The system integrates effectively with an array of safety and technological options.
SEE: 8 Greatest Penetration Testing Instruments and Software program Decisions (TechRepublic)
Why I picked LogRhythm SIEM
For group’s requiring an on-prem resolution, I like to recommend LogRhythm. You get a holistic safety strategy, getting options corresponding to embedded modules, risk monitoring and automatic detection and response. It additionally supplies streamlined incident investigation and evaluation capabilities for organizations in search of a chook’s-eye-view of their IT infrastructure. For on-premises deployments, LogRhythm additionally places emphasis in offering highly-usable content material for compliance and regulatory necessities.
Pricing
- Contact for curated pricing.
- Quite a lot of pricing choices can be found, corresponding to perpetual or subscription software program licenses, a limiteless information plan and a high-performance plan.
Options
- Heightens the detection of safety and potential threats.
- LogRhythm supplies an built-in person expertise.
- Combines enterprise log administration, safety analytics, person entity and behavioral analytics (UEBA), community visitors and behavioral analytics (NTBA) and safety automation and orchestration.
- In addition to an on-prem model, it additionally affords a cloud-based SIEM.
Determine D
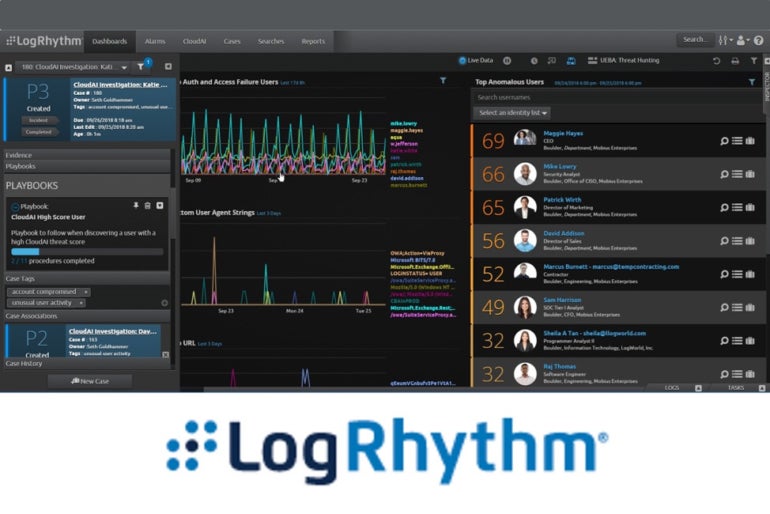
Professionals
- Constructed on a machine analytics/information lake expertise basis that’s designed to scale simply.
- Open platform permits for integration with enterprise safety and IT infrastructure.
- Embedded modules, dashboards and guidelines ship risk monitoring, risk searching, risk investigation and incident response.
- Integration with many third-party platforms.
- Consumer feedback are favorable concerning the velocity and responsiveness of the help workforce.
Cons
- Giant upfront funding usually wanted for the on-prem model.
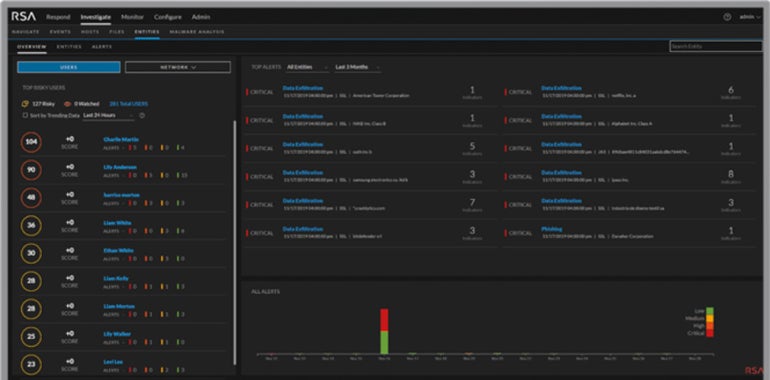
RSA NetWitness: Greatest for big enterprises

RSA, well-known for its multifactor gentle and exhausting token authentication merchandise, has a powerful footprint within the general safety group. Its NetWitness SIEM is geared extra towards giant companies, with variations that work each on-premises and by way of cloud.
SEE: High 8 Superior Risk Safety Instruments and Software program Choices for 2024 (TechRepublic)
Why I picked RSA NetWitness
RSA NetWitness carved its identify on this record for being an all-around safety resolution constructed for larger organizations. It supplies visibility throughout a variety of seize factors, in addition to having good analytics and automation capabilities for each recognized and unknown assaults. I discover that giant companies particularly will profit from NetWitness’ fast-performing risk detection — which is ready to reveal the complete assault scope in a well timed method.
Pricing
- Contact for curated pricing.
Options
- NetWitness screens for actionable occasions.
- Conduct analytics observe hacker exercise and recreate full classes to look at the exact anatomy of an assault.
- Intelligence feeds primarily based on customizable info monitor and stay key operations.
- Visibility into log information unfold throughout the IT setting.
Determine E
Integrations
- Azure.
- AWS.
- Cisco.
- Google Cloud Platform.
- Symantec Endpoint Safety.
- Kaspersky CyberTrace.
Professionals
- Simplifies risk detection, reduces dwell time and helps compliance.
- Centralized log administration and log monitoring for logs generated by public clouds and SaaS functions.
- Identification of suspicious exercise that evades signature-based safety instruments.
Cons
- The training curve and implementation efforts might be steep.
- Some customers require a considerable amount of rack house.
ManageEngine Log360: Greatest for small companies

ManageEngine Log360 is a SIEM that serves companies of all sizes however is very suited to small enterprise (SMBs) deployments. It additionally integrates effectively with a sequence of different safety and monitoring merchandise that the corporate affords.
Why I picked ManageEngine Log360
ManageEngine Log 360 is on this record for being particularly helpful to SMBs. It has all of the SIEM options SMBs will profit from, corresponding to occasion log evaluation and cloud infrastructure monitoring, in addition to risk detection and automatic responses. I significantly like how ManageEngine makes it very accessible for companies to strive Log360’s premium options without spending a dime — by way of a beneficiant 30-day free trial.
Pricing
- Reply ManageEngine’s on-line type to get a customized quote.
Options
- Detect inside threats, corresponding to information exfiltration and person account compromise, by recognizing refined adjustments in person exercise.
- Determine suspicious or blacklisted IPs, URLs and domains intruding into your community by correlating your log information with reputed risk feeds.
- Automate responses to occasions with configurable workflows.
- Monitor energetic VPN connections and obtain alerts on uncommon VPN actions and VPN entry from malicious sources.
Integrations
- AWS.
- Azure.
- Salesforce.
- Google Cloud.
- ESET Antivirus.
- Cisco.
Professionals
- Migrate SharePoint environments to Microsoft 365 by choosing the required SharePoint website customers, teams and permission ranges.
- Audit adjustments in Energetic Listing infrastructure and Azure AD in actual time.
- Uncover and classify delicate information, audit customers’ file actions and analyze file permissions.
- Detect, disrupt and forestall delicate information leaks by way of endpoints, like USBs and printers, electronic mail and internet functions with real-time safety monitoring.
Cons
- Some customers complain of poor help.
- Might wrestle to scale effectively sufficient in giant, complicated environments.
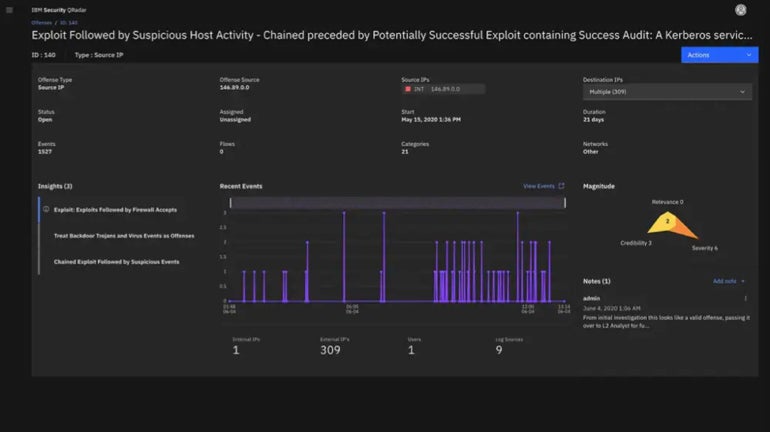
IBM Safety QRadar SIEM: Greatest for IBM retailers

IBM QRadar is a risk detection and response resolution that features an SIEM module. As such, IBM Safety QRadar SIEM is very suited to enterprises which might be closely invested in IBM instruments and techniques, in addition to giant enterprise deployments.
Why I picked IBM Safety QRadar SIEM
I picked IBM’s QRadar SIEM as a sensible alternative for corporations which have already closely built-in IBM merchandise and instruments into their workflow. Happily, Safety QRadar additionally affords a great variety of integrations with different third-party providers — making it a viable SIEM possibility even for corporations that don’t have an IBM ecosystem.
Pricing
- Go to IBM’s official on-line value estimator to get a customized quote.
Options
- Accelerated risk response by dashboards that spotlight alerts that matter.
- Makes use of close to real-time analytics to intelligently examine and prioritize high-fidelity alerts primarily based on severity of threat.
- Identifies insider threats and dangerous person conduct.
- A part of IBM Cloud Pak for Safety which makes use of AI to supply threat assessments in addition to analytics.
Determine F
Integrations
- AWS.
- Verify Level.
- Google Cloud.
- Palo Alto Networks.
- Pattern Micro.
- Carbon Black (VMware).
Professionals
- Machine learning-based analytics to establish anomalies as potential risk actors.
- QRadar SIEM augments conventional log information by monitoring key community movement information.
Cons
- Lack of integration with different SIEM instruments.
- These not utilizing IBM platforms could discover it troublesome to deploy.
Trellix Safety Operations and Analytics: Greatest for Home windows retailers

Trellix Safety Operations and Analytics accommodates the bones of the outdated McAfee Enterprise Safety Supervisor SIEM platform and is now a module often known as Trellix Enterprise Safety Supervisor. That SIEM providing was Energetic Listing-based and effectively suited to Home windows environments. However Trellix has expanded it to supply robust cloud help.
Why we selected Trellix Safety Operations and Analytics
Pricing
- Contact Trellix for curated pricing.
Options
- The Trellix Helix SecOps platform is a part of a set that features SIEM to assist IT take management from incident to detection to response.
- Trellix Insights supplies risk intelligence to foretell and prioritize threats and prescribe countermeasures.
- Trellix ePO safety administration platform helps IT management and administer all endpoints from a single console.
Integrations
- Trellix Endpoint Detection and Response.
- Trelix Helix.
- Trelix Insights.
- Cisco.
Professionals
- A central view of potential threats with built-in workflows removes complexity.
- Get larger transparency monitoring customers, functions, networks and units.
- Actual-time risk identification and response reduces lead time to guard towards threats.
- Can combine merchandise from 650+ third-party distributors.
Cons
- The complete Trellix suite is required to supply full remediation capabilities.
- Some customers complain that it may be gradual to reply.
AT&T USM Anyplace: Greatest for asset discovery
AlienVault Unified Safety Administration platform (USM) is now AT&T USM Anyplace. It discovers property and gathers information about operating providers, customers, working techniques and {hardware} info. This asset focus means it may decide up any units within the setting that it protects.
Why I picked AT&T USM Anyplace
USM Anyplace obtained its place on this record as a stable software for companies that prioritize risk detection and asset discovery above all else. It will possibly detect vulnerabilities and threats on the cloud, the community or on-prem — making it a digital detection resolution for every type of IT infrastructures.
Pricing
- Necessities – $1,075 per 30 days; tailor-made for small IT groups as a safety and compliance software.
- Commonplace – $1,695 per 30 days; catered in the direction of IT safety groups which require automation and deep safety evaluation.
- Premium – $2,595 per 30 days; geared in the direction of IT safety groups whose purpose is to fulfill PCI DSS audit necessities.
- You might also reply USM Anyplace’s on-line type to get a customized citation.
Options
- Mechanically collects and analyzes information throughout the assault floor.
- Risk intelligence supplied by AT&T Alien Labs.
- Helps an ecosystem of AlienApps to orchestrate and automate actions in the direction of different safety applied sciences and reply to incidents.
Integrations
Professionals
- Good for many who need their cybersecurity and SIEM providers managed by another person.
Cons
- Not appropriate for organizations that want to take care of tight management over their very own property for sensitivity or compliance causes.
Key options of SIEM software program
All SIEM software program instruments maintain log monitoring and administration. Additional essential options embody whether or not the software is cloud-based, whether or not it may be hosted on-prem, whether or not it contains remediation capabilities and what platforms it runs on.
Cloud
As of late, most SIEM software program relies within the cloud. Cloud-based merchandise are simpler to deploy, simpler to handle and easier to run. And with so many enterprises working in a number of clouds, SIEM instruments within the cloud are a must have. Some distributors present SIEM on a Software program-as-a-Service (SaaS) foundation, and others supply it as a totally managed service.
Hosted On-prem
Some enterprises are averse to working within the cloud as a consequence of privateness, safety or compliance causes. They should load SIEM on their very own inside servers. Some distributors supply this feature, whereas others don’t.
Remediation
SIEM originated as a solution to simplify the compilation and evaluation of safety logs. It supplied enterprises with a solution to consider big numbers of log entries and alerts and detect potential points or intrusions. Extra not too long ago, nonetheless, SIEM platforms have begun so as to add remediation capabilities. Some supply methods to automate a restricted variety of remediation actions. However just a few instruments present entry to a variety of safety remediations, both throughout the SIEM itself or by way of built-in or related instruments supplied by the identical vendor.
Platforms
The SIEM market is very aggressive. Most distributors have to supply instruments that function on all main working techniques and cloud environments. However there is usually a few holes. These with an in depth Google Chrome presence, for instance, could discover their SIEM choices restricted. It’s important, due to this fact, to confirm that your potential vendor of alternative is absolutely set as much as run their techniques in your setting.
How do I select one of the best SIEM software program for my enterprise?
Each one of many merchandise outlined right here affords high quality safety safety and can be of worth to any group — and each group wants some degree of log-based real-time safety evaluation to assist stop and detect threats.
Making the best alternative when choosing SIEM software program goes to rely on firm priorities, necessities, funds, degree of IT experience and degree of IT availability to evaluate and deal with threats. If cash isn’t any object and tech workers isn’t ready or prepared to roll up its sleeves and deal with safety dangers, a managed SIEM like USM Anyplace could be the solution to go. If firm budgets are much less sturdy and in-house expertise and time are copious, SolarWinds SEM, Datadog or AlienVault can be among the many candidates. In any other case, choices corresponding to LogRhythm, CrowdSrike, Splunk, RSA, IBM QRadar and ManageEngine needs to be excessive on the record of these to contemplate.
Methodology
The SIEM instruments coated right here had been chosen primarily based on an in depth analysis of official safety characteristic inclusions, prominence in evaluation reviews and real-world person evaluations. Every SIEM resolution was analyzed primarily based on its execs and cons, safety features and value choices.
As well as, a heavy emphasis was positioned on how every SIEM software might be of use to sure use instances and companies. This takes into consideration specializations per product and what forms of organizations can greatest maximize their characteristic set.
Lastly, the range and variety of integrations with third-party safety providers had been additionally thought-about for this shortlist. That is to make sure the sleek adoption of the SIEM resolution inside a enterprise’ present structure and the seamless monitoring of knowledge factors throughout the group’s IT infrastructure for the SIEM itself.










