Motive #1: Restoring belief in DAST
Dynamic software safety testing (DAST) has come a really good distance from the straightforward net software testing instruments of the early 2000s. The primary scanners had been easy scripts and utilities to help in guide testing throughout principally static net pages. As net applied sciences superior by leaps and bounds, legacy DAST merchandise developed from the early scanners merely couldn’t sustain, proving restricted in scope, accuracy, and usefulness. This gave rise to the stereotype of DAST as a second-rate citizen on this planet of software safety testing – a nice-to-have quite than must-have.
Regardless that at present’s superior options symbolize a very new era of DAST, customers nonetheless have low expectations of automated dynamic testing and are usually skeptical of any new claims of effectiveness. In spite of everything, each vendor claims to have greater accuracy and fewer false positives than the competitors. To counter this, Invicti was constructed on the deceptively easy concept that to persuade customers a vulnerability is actual, you want to ship stable proof – and that is how proof-based scanning was born.
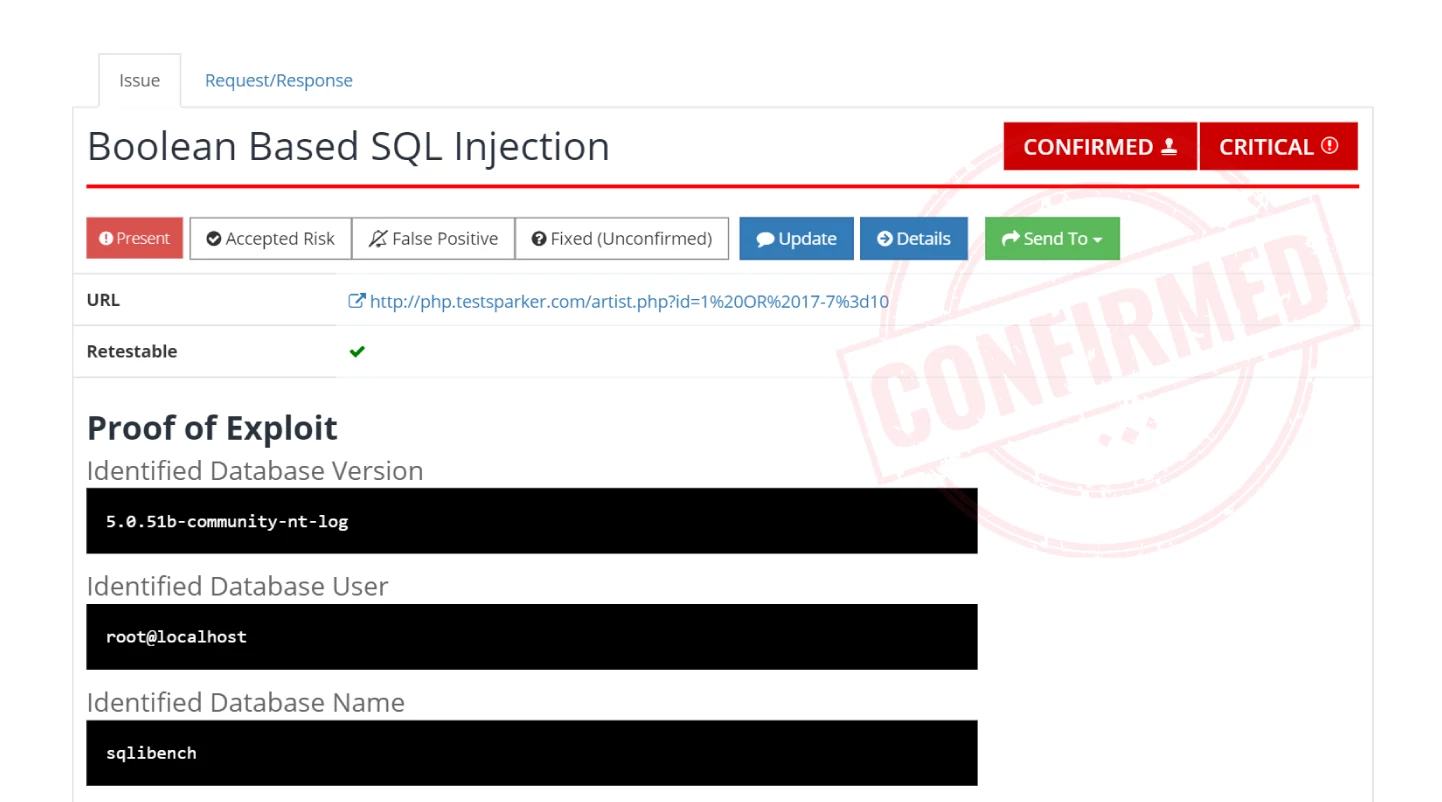
The actual innovation is that an automatic device can determine many vulnerabilities with the identical degree of certainty as a penetration tester or bounty hunter. The Confirmed stamp that you simply see in Invicti stories for verified vulnerabilities is extra than simply an icon – it implies that the difficulty is actual and you may transfer to deal with it with out guide verification by the safety staff. Fairly merely, in the event you see Confirmed, you’ve a vulnerability that you want to repair. Interval.
Vulnerability confirmations offered by proof-based scanning are at the very least 99.98% correct. Learn the way we calculated this share primarily based on real-life vulnerability testing knowledge and the way correct vulnerability scanning can translate into main financial savings.
Motive #2: The shift to fact-based net software safety
Proof-based scanning works by safely exploiting an recognized vulnerability and extracting pattern knowledge to show that an assault is feasible. It isn’t a gimmick or an additional function to tick off on the checklist however a elementary change within the method to vulnerability scanning. With legacy scanners, the outcomes had been at all times a listing of suspicious pages that somebody ought to most likely check out. With evidence-based automated affirmation, there’s nothing unsure about your DAST outcomes – they’re vulnerabilities that actually exist, are exploitable, and might get you hacked proper now. You’re now working with safety info.
With out proof, each outcome from even the very best DAST may very well be a false alarm till anyone checks it manually. In a big net surroundings, you possibly can have 1000’s of points being reported – however till they’re verified, you merely don’t know your present safety standing or workload. Proof-based scanning cuts by this uncertainty by mechanically and conclusively displaying which points are actual and exploitable and can’t be false positives. This eliminates guesswork and permits the transfer to fact-based net software safety at any scale.
Motive #3: Correct prioritization and planning
In any net software surroundings, you’ll get quite a lot of points that differ in sort, significance, and potential affect. To get measurable safety enhancements from day one, you want to focus your assets the place they may make the most important distinction at a given time, beginning with vulnerabilities which are straight exploitable and would have the best affect if focused by attackers.
That is the place proof-based scanning actually shines. Each confirmed vulnerability that’s accompanied by proof has already been safely exploited by the scanner, so you realize for a indisputable fact that attackers may exploit it as properly. Mixed with severity scores and technical info offered in every vulnerability report, this provides you correct knowledge to plan and prioritize decision efforts for speedy time-to-value.
Proof-based scanning mechanically confirms over 94% of direct-impact vulnerabilities – points reminiscent of injections and cross-site scripting that may be remotely exploited with no further stipulations. See our technical white paper to find out how that is potential.
Motive #4: True automation and scalability
Trendy net software improvement depends on automation and cloud-based scalability. Construct environments, steady integration pipelines, containerized deployments – every part is closely automated as a result of that’s the one strategy to construct and function extraordinarily advanced and dynamic environments with restricted human assets. But once you attempt to add automated safety testing to this combine, issues don’t at all times mesh easily.
Automation is all about eliminating as a lot guide work as potential. So what do you do if all the outcomes out of your legacy DAST have to be verified manually earlier than you possibly can create developer tickets? That is the place most DAST merchandise stumble, resulting in the misperception that you would be able to’t use DAST in CI/CD pipelines. After all you possibly can – however provided that you utilize evidence-based scanning to make sure that solely actual and exploitable safety points are assigned mechanically and also you’re not injecting false-positive outcomes into your improvement and testing workflow.
To take safety automation and scalability even additional, Invicti integrates with widespread difficulty trackers out-of-the-box so mechanically confirmed vulnerability stories can go on to builders with out clunky further steps burdening the safety staff. You too can arrange automated repair retesting to go from safety bug report back to an efficient repair with none guide steps by safety employees. Confirmed and totally trusted vulnerability scan outcomes pave the way in which to assured automation and true scalability.
Motive #5: Improved workflows and dealing relations
Final however actually not least, proof-based scanning fully adjustments the developer-security staff dynamic by minimizing miscommunication and back-and-forth. When a developer will get a confirmed safety difficulty report from the Invicti resolution, they will instantly see proof that the vulnerability actually exists and is exploitable. Additionally they get detailed details about the difficulty and its potential affect, together with full remediation steerage. It is a big time-saver for safety engineers, who can now give attention to managing vulnerabilities and offering safety recommendation quite than manually confirming, documenting, and monitoring points.
Transferring from prolonged exchanges triggered by “this code is insecure, repair it” to detailed bug stories accompanied by precise proof eliminates pointless communication, streamlines workflows, and tremendously improves working relations. No extra finger-pointing and throwing points over the wall – now everybody works with stable knowledge to grasp root causes, eradicate vulnerabilities, and enhance safety in the long term. Builders get actionable tickets to allow them to shortly repair safety bugs and give attention to constructing higher software program, whereas safety testers can think about extra advanced vulnerabilities that actually want human experience and instinct.
At all times demand proof
There are many vulnerability scanners on the DAST market and distributors are all making comparable claims about accuracy, low false positives, nice protection… It could possibly get fairly complicated on the market. At Invicti, we worth straight speaking. After we say a vulnerability is confirmed and confirmed, the difficulty is unquestionably actual – and we all know as a result of we’ve got already safely exploited it. Right here is your bug, right here is your proof, go repair it. Net software safety doesn’t get any less complicated.
To see how Invicti eliminates uncertainty with 99.98% accuracy and study the interior workings of proof-based scanning, get the complete Invicti technical white paper: How Invicti Generates Proof to Keep away from False Positives.










