On Tuesday Microsoft launched 59 CVEs, together with 41 for Home windows. A outstanding 20 different product teams or instruments are additionally affected. Of the CVEs addressed, simply two are thought-about Crucial in severity by Microsoft, each in Home windows (particularly, in Hyper-V).
At patch time, not one of the points has been publicly disclosed, or is understood to be underneath lively exploit within the wild. Six of the important-severity vulnerabilities in Home windows are by the corporate’s estimation extra more likely to be exploited within the subsequent 30 days. 5 of the problems addressed are amenable to detection by Sophos protections, and we embrace info on these in a desk under.
Along with these patches the discharge included advisory info on 4 patches associated to the Edge browser; three of these CVEs had been assigned by the Chrome workforce, not Microsoft. (Extra on Microsoft’s Edge patch, CVE-2024-26167, in a minute.) There’s additionally one Vital-severity situation, CVE-2023-28746, for which advisory info is given this month.
We don’t embrace advisories within the CVE counts and graphics under, however we offer info on all of them in an appendix on the finish of the article. We’re as ordinary together with on the finish of this submit three different appendices itemizing all Microsoft’s patches, sorted by severity, by predicted exploitability, and by product household.
By the Numbers
- Whole Microsoft CVEs (excluding Edge): 59
- Whole Edge / Chrome points coated in replace: 4
- Whole non-Microsoft CVEs coated in replace: 1
- Publicly disclosed: 0
- Exploited: 0
- Severity
- Crucial: 2
- Vital: 57
-
- Elevation of Privilege: 25
- Distant Code Execution: 18
- Denial of Service: 6
- Info Disclosure: 5
- Safety Function Bypass: 2
- Spoofing: 2
- Tampering: 1
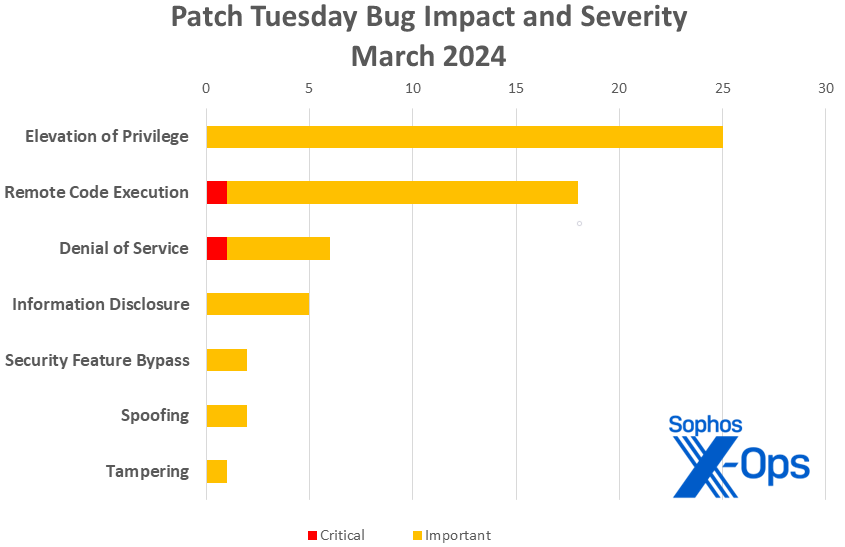
Determine 1: And identical to that, 2024 ties 2023’s whole output of tampering CVEs… at one. Extra on CVE-2024-26185 in a minute
Merchandise
- Home windows: 41 (together with one shared with .NET and Visible Studio)
- Azure: 4 (together with one shared with Log Analytics Agent, OMI, OMS, and SCOM)
- Visible Studio: 3 (together with one shared with .NET and one shared with .NET and Home windows)
- .NET: 2 (together with one shared with Visible Studio and one shared with Visible Studio and Home windows)
- OMI (Open Administration Infrastructure): 2 (together with one shared with Azure, Log Analytics Agent, OMS, and SCOM; and one shared with SCOM)
- SCOM (System Heart Operations Supervisor): 2 (together with one shared with Azure, Log Analytics Agent, OMI, and OMS; and one shared with OMI
- Authenticator: 1
- Defender: 1
- Dynamics 365: 1
- Alternate: 1
- Intune: 1
- Log Analytics Agent: 1 (shared with Azure, OMI, OMS, and SCOM)
- Workplace (365 on-premises): 1
- OMS (Operations Administration Suite Agent for Linux): 1 (shared with Azure, OMI, and SCOM)
- Outlook: 1
- SharePoint: 1
- Skype: 1
- SONiC (Software program for Open Networking within the Cloud): 1
- SQL: 1
- Groups: 1
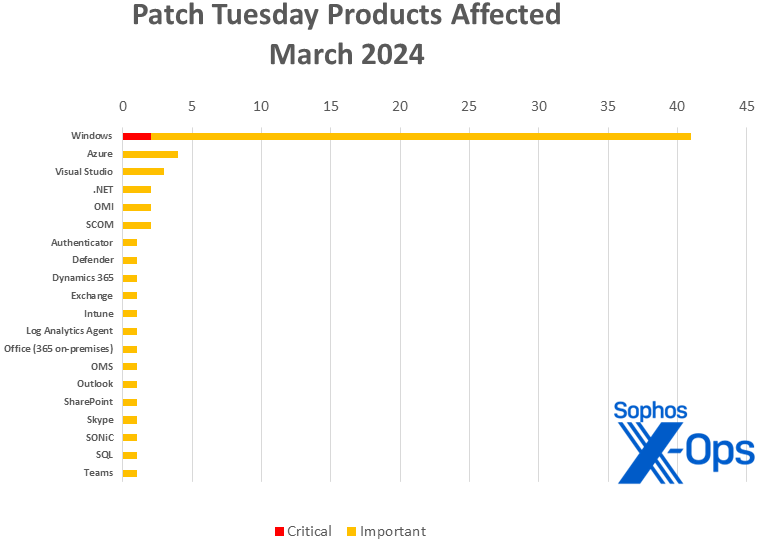
Determine 2: There’s one thing for everybody, as twenty instruments or product teams are touched by the March Patch Tuesday angel
Notable March updates
Along with the problems mentioned above, a number of particular gadgets advantage consideration.
CVE-2024-26185
Home windows Compressed Folder Tampering Vulnerability
One of many six points Microsoft believes extra more likely to be exploited within the subsequent 30 days, this vulnerability impacts the ever present 7zip. Minimal consumer interplay is required, almost definitely by way of e mail (wherein the attacker sends a specifically crafted file and convinces the consumer to open it) or by way of the net. This patch applies solely to Win11 22H2 and Win11 23H2.
CVE-2024-21334
Open Administration Infrastructure (OMI) Distant Code Execution Vulnerability
Sporting the month’s highest CVSS rating (9.8 base) and but not more likely to be exploited within the subsequent 30 days as judged by Microsoft, this RCE applies to not simply OMI however to SCOM (System Heart Operations Supervisor) 2019 and 2022 as nicely. If exploited, a unauthenticated distant attacker might entry the OMI occasion by way of the web and ship specifically crafted requests to set off a use-after-free vulnerability. (If patching’s not a direct possibility, Linux machines that don’t want community listening can disable their incoming OMI ports by the use of mitigation.)
CVE-2024-21421
Azure SDK Spoofing Vulnerability
Examine the date of your final deployment: Was it previous to October 19, 2023? If that’s the case, you’ll must manually replace to Azure Core Construct 1.29.5 or increased. (For comfort, Azure SDK’s GitHub is on the market right here.) These with deployments after that date already obtained the repair mechanically.
CVE-2024-21448
Microsoft Groups for Android Info Disclosure
There are a variety of Android-related patches this month – Intune, Outlook, the Edge patch we’ll talk about under – however solely this one, an important-severity Groups situation, would require a visit to the Play Retailer. Exploitation would permit the attacker to learn information from the personal listing of the applying.
CVE-2024-26167
Microsoft Edge for Android Spoofing Vulnerability
As an Edge vulnerability, this one arrives with scant info from Microsoft, which within the post-IE period primarily takes its browser updates exterior the Patch Tuesday cycle. As an Android vulnerability, it could be that Android customers will take this replace from different sources. What’s clear from Microsoft is that no matter it’s and whoever’s patching it, the patch isn’t but obtainable, and that these involved ought to keep watch over the publicly posted CVE info for updates. Thankfully, with a 4.3 CVSS base rating, this thriller could be a tempest in a teapot.
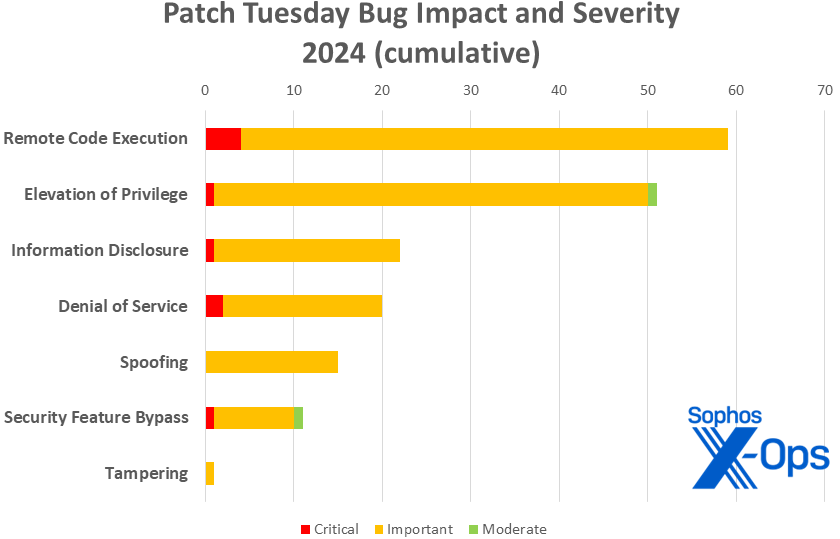
Determine 3: March continues the pattern thus far in 2024 of lighter-than-usual patch hundreds. Thus far in 2024 there have been 179 patches launched within the regular second-Tuesday cadence, in contrast with 246 in 2023, 225 in 2022, 228 in 2021, and 266 in 2020
Sophos protections
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2024-21433 | Exp/2421433-A | Exp/2421433-A |
| CVE-2024-21437 | Exp/2421437-A | Exp/2421437-A |
| CVE-2024-26160 | Exp/2426160-A | Exp/2426160-A |
| CVE-2024-26170 | Exp/2426170-A | Exp/2426170-A |
| CVE-2024-26182 | Exp/2426182-A | Exp/2426182-A |
As you’ll be able to each month, in the event you don’t wish to wait on your system to drag down Microsoft’s updates itself, you’ll be able to obtain them manually from the Home windows Replace Catalog web site. Run the winver.exe software to find out which construct of Home windows 10 or 11 you’re working, then obtain the Cumulative Replace package deal on your particular system’s structure and construct quantity.
Appendix A: Vulnerability Influence and Severity
This can be a checklist of March patches sorted by affect, then sub-sorted by severity. Every checklist is additional organized by CVE.
Elevation of Privilege (25 CVEs)
| Vital severity | |
| CVE-2024-21330 | Open Administration Infrastructure (OMI) Elevation of Privilege Vulnerability |
| CVE-2024-21390 | Microsoft Authenticator Elevation of Privilege Vulnerability |
| CVE-2024-21400 | Microsoft Azure Kubernetes Service Confidential Container Elevation of Privilege Vulnerability |
| CVE-2024-21418 | Software program for Open Networking within the Cloud (SONiC) Elevation of Privilege Vulnerability |
| CVE-2024-21431 | Hypervisor-Protected Code Integrity (HVCI) Safety Function Bypass Vulnerability |
| CVE-2024-21432 | Home windows Replace Stack Elevation of Privilege Vulnerability |
| CVE-2024-21433 | Home windows Print Spooler Elevation of Privilege Vulnerability |
| CVE-2024-21434 | Microsoft Home windows SCSI Class System File Elevation of Privilege Vulnerability |
| CVE-2024-21436 | Home windows Installer Elevation of Privilege Vulnerability |
| CVE-2024-21437 | Home windows Graphics Element Elevation of Privilege Vulnerability |
| CVE-2024-21439 | Home windows Telephony Server Elevation of Privilege Vulnerability |
| CVE-2024-21442 | Home windows USB Print Driver Elevation of Privilege Vulnerability |
| CVE-2024-21443 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-21445 | Home windows USB Print Driver Elevation of Privilege Vulnerability |
| CVE-2024-21446 | NTFS Elevation of Privilege Vulnerability |
| CVE-2024-26165 | Visible Studio Code Elevation of Privilege Vulnerability |
| CVE-2024-26169 | Home windows Error Reporting Service Elevation of Privilege Vulnerability |
| CVE-2024-26170 | Home windows Composite Picture File System (CimFS) Elevation of Privilege Vulnerability |
| CVE-2024-26173 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-26176 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-26178 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-26182 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-26199 | Microsoft Workplace Elevation of Privilege Vulnerability |
| CVE-2024-26201 | Microsoft Intune Linux Agent Elevation of Privilege Vulnerability |
| CVE-2024-26203 | Azure Information Studio Elevation of Privilege Vulnerability |
Distant Code Execution (18 CVEs)
| Crucial severity | |
| CVE-2024-21407 | Home windows Hyper-V Distant Code Execution Vulnerability |
| Vital severity | |
| CVE-2024-21334 | Open Administration Infrastructure (OMI) Distant Code Execution Vulnerability |
| CVE-2024-21411 | Skype for Shopper Distant Code Execution Vulnerability |
| CVE-2024-21426 | Microsoft SharePoint Server Distant Code Execution Vulnerability |
| CVE-2024-21429 | Home windows USB Hub Driver Distant Code Execution Vulnerability |
| CVE-2024-21430 | Home windows USB Connected SCSI (UAS) Protocol Distant Code Execution Vulnerability |
| CVE-2024-21435 | Home windows OLE Distant Code Execution Vulnerability |
| CVE-2024-21440 | Microsoft ODBC Driver Distant Code Execution Vulnerability |
| CVE-2024-21441 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21444 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21450 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21451 | Microsoft ODBC Driver Distant Code Execution Vulnerability |
| CVE-2024-26159 | Microsoft ODBC Driver Distant Code Execution Vulnerability |
| CVE-2024-26161 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-26162 | Microsoft ODBC Driver Distant Code Execution Vulnerability |
| CVE-2024-26164 | Microsoft Django Backend for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-26166 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-26198 | Microsoft Alternate Server Distant Code Execution Vulnerability |
Denial of Service (6 CVEs)
| Crucial severity | |
| CVE-2024-21408 | Home windows Hyper-V Denial of Service Vulnerability |
| Vital severity | |
| CVE-2024-21392 | .NET and Visible Studio Denial of Service Vulnerability |
| CVE-2024-21438 | Microsoft AllJoyn API Denial of Service Vulnerability |
| CVE-2024-26181 | Home windows Kernel Denial of Service Vulnerability |
| CVE-2024-26190 | Microsoft QUIC Denial of Service Vulnerability |
| CVE-2024-26197 | Home windows Requirements-Based mostly Storage Administration Service Denial of Service Vulnerability |
info Disclosure (5 CVEs)
| Vital severity | |
| CVE-2024-21448 | Microsoft Groups for Android Info Disclosure |
| CVE-2024-26160 | Home windows Cloud Information Mini Filter Driver Info Disclosure Vulnerability |
| CVE-2024-26174 | Home windows Kernel Info Disclosure Vulnerability |
| CVE-2024-26177 | Home windows Kernel Info Disclosure Vulnerability |
| CVE-2024-26204 | Outlook for Android Info Disclosure Vulnerability |
Safety Function Bypass (2 CVEs)
| Vital severity | |
| CVE-2024-20671 | Microsoft Defender Safety Function Bypass Vulnerability |
| CVE-2024-21427 | Home windows Kerberos Safety Function Bypass Vulnerability |
Spoofing (2 CVEs)
| Vital severity | |
| CVE-2024-21419 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability |
| CVE-2024-21421 | Azure SDK Spoofing Vulnerability |
Tampering (1 CVE)
| Vital severity | |
| CVE-2024-26185 | Home windows Compressed Folder Tampering Vulnerability |
Appendix B: Exploitability
This can be a checklist of the March CVEs judged by Microsoft to be extra more likely to be exploited within the wild inside the first 30 days post-release. The checklist is organized by CVE.
| Exploitation extra possible inside the subsequent 30 days | |
| CVE-2024-21433 | Home windows Print Spooler Elevation of Privilege Vulnerability |
| CVE-2024-21437 | Home windows Graphics Element Elevation of Privilege Vulnerability |
| CVE-2024-26160 | Home windows Cloud Information Mini Filter Driver Info Disclosure Vulnerability |
| CVE-2024-26170 | Home windows Composite Picture File System (CimFS) Elevation of Privilege Vulnerability |
| CVE-2024-26182 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-26185 | Home windows Compressed Folder Tampering Vulnerability |
Appendix C: Merchandise Affected
This can be a checklist of March’s patches sorted by product household, then sub-sorted by severity. Every checklist is additional organized by CVE. Patches which can be shared amongst a number of product households are listed a number of occasions, as soon as for every product household.
Home windows (41 CVEs)
| Crucial severity | |
| CVE-2024-21407 | Home windows Hyper-V Distant Code Execution Vulnerability |
| CVE-2024-21408 | Home windows Hyper-V Denial of Service Vulnerability |
| Vital severity | |
| CVE-2024-21427 | Home windows Kerberos Safety Function Bypass Vulnerability |
| CVE-2024-21429 | Home windows USB Hub Driver Distant Code Execution Vulnerability |
| CVE-2024-21430 | Home windows USB Connected SCSI (UAS) Protocol Distant Code Execution Vulnerability |
| CVE-2024-21431 | Hypervisor-Protected Code Integrity (HVCI) Safety Function Bypass Vulnerability |
| CVE-2024-21432 | Home windows Replace Stack Elevation of Privilege Vulnerability |
| CVE-2024-21433 | Home windows Print Spooler Elevation of Privilege Vulnerability |
| CVE-2024-21434 | Microsoft Home windows SCSI Class System File Elevation of Privilege Vulnerability |
| CVE-2024-21435 | Home windows OLE Distant Code Execution Vulnerability |
| CVE-2024-21436 | Home windows Installer Elevation of Privilege Vulnerability |
| CVE-2024-21437 | Home windows Graphics Element Elevation of Privilege Vulnerability |
| CVE-2024-21438 | Microsoft AllJoyn API Denial of Service Vulnerability |
| CVE-2024-21439 | Home windows Telephony Server Elevation of Privilege Vulnerability |
| CVE-2024-21440 | Microsoft ODBC Driver Distant Code Execution Vulnerability |
| CVE-2024-21441 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21442 | Home windows USB Print Driver Elevation of Privilege Vulnerability |
| CVE-2024-21443 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-21444 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21445 | Home windows USB Print Driver Elevation of Privilege Vulnerability |
| CVE-2024-21446 | NTFS Elevation of Privilege Vulnerability |
| CVE-2024-21450 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21451 | Microsoft ODBC Driver Distant Code Execution Vulnerability |
| CVE-2024-26159 | Microsoft ODBC Driver Distant Code Execution Vulnerability |
| CVE-2024-26160 | Home windows Cloud Information Mini Filter Driver Info Disclosure Vulnerability |
| CVE-2024-26161 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-26162 | Microsoft ODBC Driver Distant Code Execution Vulnerability |
| CVE-2024-26166 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-26169 | Home windows Error Reporting Service Elevation of Privilege Vulnerability |
| CVE-2024-26170 | Home windows Composite Picture File System (CimFS) Elevation of Privilege Vulnerability |
| CVE-2024-26173 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-26174 | Home windows Kernel Info Disclosure Vulnerability |
| CVE-2024-26176 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-26177 | Home windows Kernel Info Disclosure Vulnerability |
| CVE-2024-26178 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-26181 | Home windows Kernel Denial of Service Vulnerability |
| CVE-2024-26182 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-26185 | Home windows Compressed Folder Tampering Vulnerability |
| CVE-2024-26190 | Microsoft QUIC Denial of Service Vulnerability |
| CVE-2024-26197 | Home windows Requirements-Based mostly Storage Administration Service Denial of Service Vulnerability |
Azure (4 CVEs)
| Vital severity | |
| CVE-2024-21330 | Open Administration Infrastructure (OMI) Elevation of Privilege Vulnerability |
| CVE-2024-21400 | Microsoft Azure Kubernetes Service Confidential Container Elevation of Privilege Vulnerability |
| CVE-2024-21421 | Azure SDK Spoofing Vulnerability |
| CVE-2024-26203 | Azure Information Studio Elevation of Privilege Vulnerability |
Visible Studio (3 CVEs)
| Vital severity | |
| CVE-2024-21392 | .NET and Visible Studio Denial of Service Vulnerability |
| CVE-2024-26165 | Visible Studio Code Elevation of Privilege Vulnerability |
| CVE-2024-26190 | Microsoft QUIC Denial of Service Vulnerability |
.NET (2 CVEs)
| Vital severity | |
| CVE-2024-21392 | .NET and Visible Studio Denial of Service Vulnerability |
| CVE-2024-26190 | Microsoft QUIC Denial of Service Vulnerability |
OMI (2 CVEs)
| Vital severity | |
| CVE-2024-21330 | Open Administration Infrastructure (OMI) Elevation of Privilege Vulnerability |
| CVE-2024-21334 | Open Administration Infrastructure (OMI) Distant Code Execution Vulnerability |
SCOM (2 CVEs)
| Vital severity | |
| CVE-2024-21330 | Open Administration Infrastructure (OMI) Elevation of Privilege Vulnerability |
| CVE-2024-21334 | Open Administration Infrastructure (OMI) Distant Code Execution Vulnerability |
Authenticator (1 CVE)
| Vital severity | |
| CVE-2024-21390 | Microsoft Authenticator Elevation of Privilege Vulnerability |
Defender (1 CVE)
| Vital severity | |
| CVE-2024-20671 | Microsoft Defender Safety Function Bypass Vulnerability |
Dynamics 365 (1 CVE)
| Vital severity | |
| CVE-2024-21419 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability |
Alternate (1 CVE)
| Vital severity | |
| CVE-2024-26198 | Microsoft Alternate Server Distant Code Execution Vulnerability |
Intune (1 CVE)
| Vital severity | |
| CVE-2024-26201 | Microsoft Intune Linux Agent Elevation of Privilege Vulnerability |
Regulation Analytics Agent (1 CVE)
| Vital severity | |
| CVE-2024-21330 | Open Administration Infrastructure (OMI) Elevation of Privilege Vulnerability |
Workplace (1 CVE)
| Vital severity | |
| CVE-2024-26199 | Microsoft Workplace Elevation of Privilege Vulnerability |
OMS (1 CVE)
| Vital severity | |
| CVE-2024-21330 | Open Administration Infrastructure (OMI) Elevation of Privilege Vulnerability |
Outlook (1 CVE)
| Vital severity | |
| CVE-2024-26204 | Outlook for Android Info Disclosure Vulnerability |
SharePoint (1 CVE)
| Vital severity | |
| CVE-2024-21426 | Microsoft SharePoint Server Distant Code Execution Vulnerability |
Skype (1 CVE)
| Vital severity | |
| CVE-2024-21411 | Skype for Shopper Distant Code Execution Vulnerability |
SONiC (1 CVE)
| Vital severity | |
| CVE-2024-21418 | Software program for Open Networking within the Cloud (SONiC) Elevation of Privilege Vulnerability |
SQL (1 CVE)
| Vital severity | |
| CVE-2024-26164 | Microsoft Django Backend for SQL Server Distant Code Execution Vulnerability |
Groups for Android (1 CVE)
| Vital severity | |
| CVE-2024-21448 | Microsoft Groups for Android Info Disclosure |
Appendix D: Advisories and Different Merchandise
This can be a checklist of advisories and data on different related CVEs within the March Microsoft launch, sorted by product.
Related to Edge / Chromium (4 CVEs)
| CVE-2024-2173 | Chromium: CVE-2024-2173 Out of bounds reminiscence entry in V8 |
| CVE-2024-2174 | Chromium: CVE-2024-2174 Inappropriate implementation in V8 |
| CVE-2024-2176 | Chromium: CVE-2024-2176 Use after free in FedCM |
| CVE-2024-26167 | Microsoft Edge for Android Spoofing Vulnerability |
Related to Home windows (non-Microsoft launch) (one CVE)
| CVE-2023-28746 | Intel: CVE-2023-28746 Register File Information Sampling (RFDS) |










