Ransomware assaults from the 8Base group claimed the second largest variety of victims over the previous 30 days, says VMware.

A ransomware group that likes to disgrace organizations into paying the ransom has proven a surge in exercise, in response to a Wednesday weblog publish from VMware. Generally known as 8Base, the group has been lively since March 2022 however has lately captured the second-highest variety of victims amongst recognized ransomware gangs.
Leap to:
Latest exercise from the 8Base ransomware group
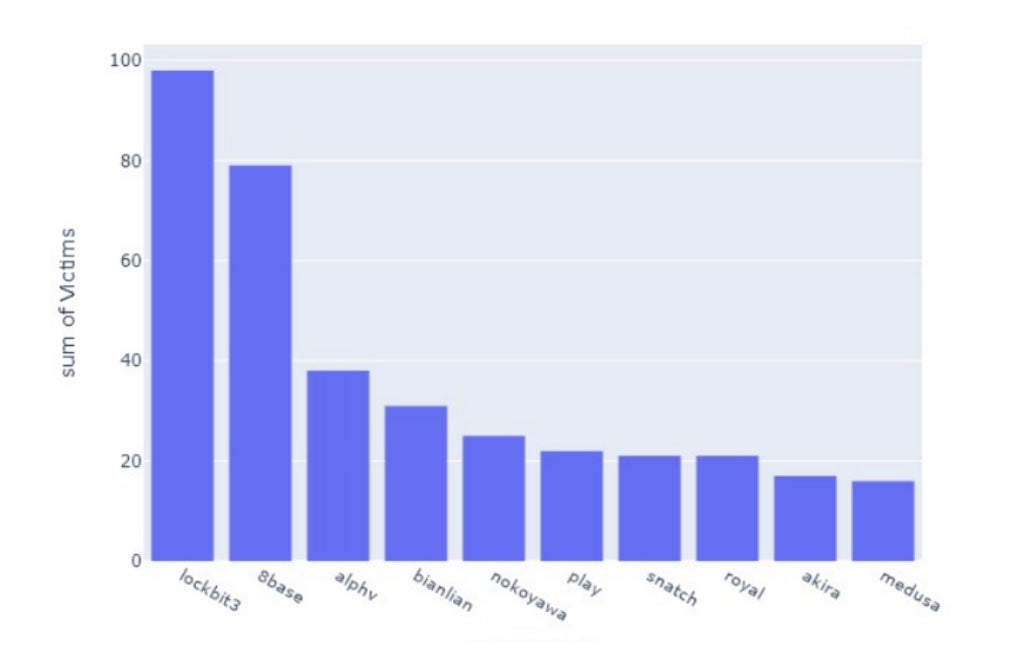
Analyzing ransomware assaults in June 2023, VMware discovered 8Base hit virtually 80 victims over the previous 30 days (Determine A), second solely to the LockBit 3 gang, which compromised virtually 100 organizations. Different ransomware teams with heavy exercise over this era included ALPHV (BlackCat) with virtually 40 victims, BianLian with greater than 30 victims and Nokoyawa with greater than 25 victims.
Determine A
Focusing on sectors like enterprise providers, finance, manufacturing and IT, 8Base is understood for utilizing “name-and-shame” double-extortion ways during which the group threatens to publish the encrypted recordsdata except the ransom is paid. The thought is to embarrass the sufferer by exposing personal or confidential info that might harm their model or fame.
Who’s the 8Base ransomware group?
Regardless of the surge in ransomware assaults staged by 8Base, particulars in regards to the group’s id, strategies and motivations largely stay a thriller, in response to VMware. Nevertheless, primarily based on its leak website and public accounts, together with the group’s communications, its verbal model is sort of much like that of RansomHouse, a bunch that usually purchases already compromised information or works with information leak websites to extort victims.
Analyzing ransom notes from each 8Base and RansomHouse, VMware found a 99% match within the verbiage. 8Base’s welcome web page, Phrases of Service web page and FAQ web page are all immediately copied phrase for phrase from RansomHouse. One distinction within the communications is that RansomHouse brazenly seeks out different felony teams for partnerships, whereas 8Base doesn’t.
One other frequent thread between the 2 teams lies within the selection of ransomware. Each 8Base and RansomHouse use a wide range of completely different ransomware strains, together with a variant generally known as Phobos. In the end, the similarities set off questions on whether or not 8Base is solely an offshoot of RansomHouse.
“Given the character of the beast that’s 8Base, we will solely speculate presently that they’re utilizing a number of several types of ransomware both as earlier variants or as a part of their regular working procedures,” VMware stated in its weblog publish. “What we do know is that this group is extremely lively and targets smaller companies.”
8Base’s leak website and public accounts
On its leak website, 8Base describes itself as “easy pen testers.” The positioning affords directions to victims with sections for Often Requested Questions and Guidelines, together with a number of methods to contact the group. 8Base additionally has an official channel on the messaging service Telegram and an account on Twitter (Determine B).
Determine B
How you can shield your group towards 8Base and different ransomware
“From a ransomware detection perspective, the purpose is to assist organizations detect ransomware early, reduce the harm attributable to an assault and get well from the assault as rapidly as attainable,” in response to VMware’s Risk Evaluation Unit.
Towards that finish, an efficient ransomware detection and restoration technique consists of the next three elements:
- Prevention: That is the primary line of protection towards ransomware assaults. Stopping an assault requires that you simply hold your crucial techniques and software program up to date, apply safety finest practices and practice your workers on the way to spot and evade phishing assaults.
- Detection: Figuring out ransomware assaults requires superior detection instruments. A key side right here is endpoint safety, which makes use of behavioral evaluation and machine studying to search for any uncommon exercise or conduct in your community.
- Response: After detecting ransomware, you could reply rapidly to attenuate the harm. Such a response entails isolating contaminated techniques, quarantining affected recordsdata and stopping the unfold of the harm to different techniques.