
Risk actors are consolidating their use of encrypted messaging platforms, preliminary entry brokers and generative AI fashions, in keeping with safety agency Cybersixgill’s new report, The State of the Cybercrime Underground 2023. This report notes that is reducing the limitations to entry into cybercrime and “streamlining the weaponization and execution of ransomware assaults.”
The examine is constructed upon 10 million posts on encrypted platforms and different kinds of knowledge dredged up from the deep, darkish and clear internet. Brad Liggett, director of risk intel, North America, at Cybersixgill, outlined these phrases:
- Clear internet: Any web site that’s accessible by way of a daily browser and never needing particular encryption to entry (e.g., CNN.com, ESPN.com, WhiteHouse.gov).
- Deep internet: Websites which might be unindexed by search engines like google and yahoo, or websites which might be gated and have restricted entry.
- Darkish internet: Websites which might be solely accessible utilizing encrypted tunneling protocols resembling Tor (the onion router browser), ZeroNet and I2P.
“What we’re gathering within the channels throughout these platforms are messages,” he mentioned. “Very similar to in case you are in a bunch textual content with buddies/household, these channels are reside discussion groups.”
Tor is standard amongst malefactors for a similar purpose: It provides folks trapped in repressive regimes a strategy to get info to the skin world, mentioned Daniel Thanos, vice chairman and head of Arctic Wolf Labs.
“As a result of it’s a federated, peer-to-peer routing system, absolutely encrypted, you possibly can have hidden web sites, and until you recognize the tackle, you’re not going to get entry,” he mentioned. “And the way in which it’s routed, it’s nearly unattainable to trace somebody.”
Bounce to:
After large enhance in messaging by cybercriminals, slight drop final 12 months
Cybercriminals use encrypted messaging platforms to collaborate, talk and commerce instruments, stolen knowledge and companies partly as a result of they provide automated functionalities that make them a perfect launchpad for cyberattacks. Nonetheless, the Cybersixgill examine suggests the variety of risk actors is reducing and concentrating on a handful of platforms.
Between 2019 and 2020, knowledge that Cybersixgill collected mirrored a large surge in use of encrypted messaging platforms, with the overall variety of collected objects growing by 730%. Within the agency’s 2020-2021 evaluation, this quantity elevated by 338%, after which simply 23% in 2022 to some 1.9 billion objects collected from messaging platforms (Determine A).
Determine A
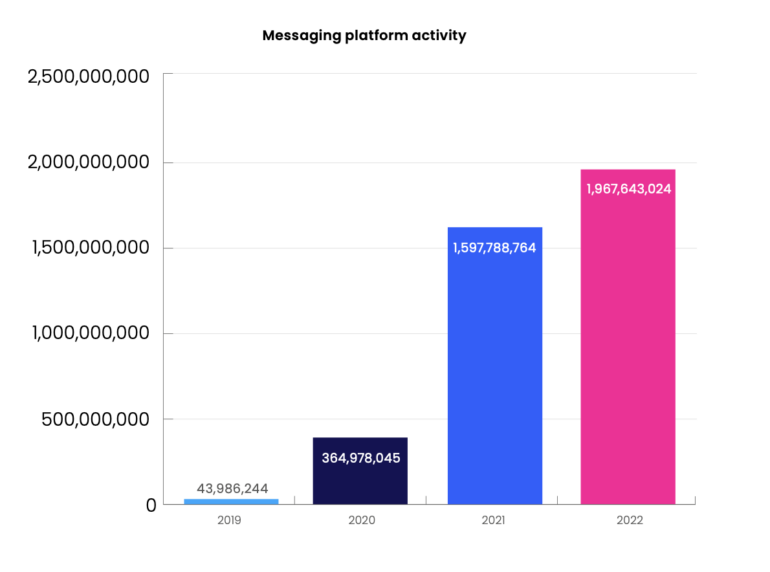
“When contemplating workflow exercise, it’s faster and simpler to flick through channels on the messaging platforms moderately than needing to log in to numerous boards, and skim via posts, and so forth.,” mentioned Liggett.
From the darkish to deep internet: Fewer onions, extra apps
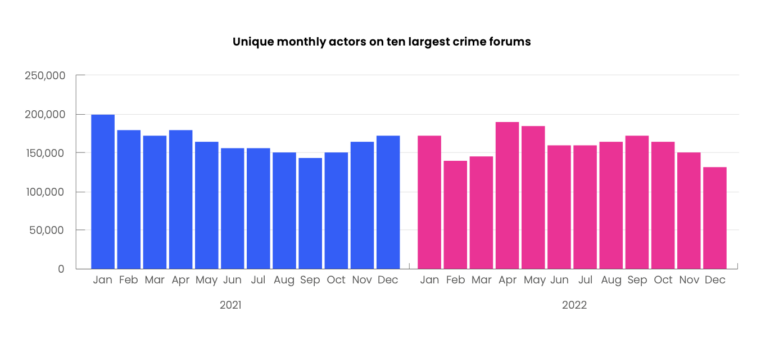
Throughout the darkish internet onion websites, the overall variety of discussion board posts and replies decreased by 13% between 2021 and 2022, dropping from over 91.7 million to round 79.1 million. The variety of risk actors actively taking part in prime boards additionally declined barely, in keeping with the report.
The ten largest cybercrime boards averaged 165,390 month-to-month customers in 2021, which dropped by 4% to 158,813 in 2022. Nonetheless, posts on these 10 websites grew by practically 28%, which means the boards’ individuals turned extra energetic.
The examine mentioned that, prior to now, most risk actors performed their operations on the darkish internet alone, whereas lately there’s been migration to deep-web encrypted messaging platforms.
Ease of use favors deep internet platforms
Cybercriminals favor deep internet platforms due to their relative ease of use versus Tor, which requires extra technical abilities. “Throughout easily-accessible platforms, chats and channels, risk actors collaborate and talk, buying and selling instruments, stolen knowledge and companies in a bootleg community that operates in parallel to its darkish internet equal,” mentioned the examine.
“Individuals have a tendency to speak in real-time throughout these platforms,” mentioned Liggett. “Boards and marketplaces at nighttime internet are infamous for not at all times having a excessive stage of uptime. They generally find yourself going offline after a time frame, or as we’ve seen just lately have been seized by legislation enforcement and authorities companies,” he mentioned, noting that one such platform, RaidForums, was taken down in 2022, and BreachedForums only a couple weeks in the past (Determine B).
Determine B
Cybercriminals congregate at these deep internet channels
Liggett mentioned Telegram is the most well-liked messaging platform for risk actors. Others, he mentioned, embody:
- Discord is a messaging platform favored by avid gamers.
- ICQ was first launched within the Nineteen Nineties and bought by a Russian firm in 2010.
- QQ is a well-liked communication platform in China.
- Wickr is a New York-based unit of Amazon Internet Companies.
- Sign is a free and open supply, encrypted service.
- Tox can be a FOSS, peer-to-peer system.
Preliminary entry brokers are booming enterprise
The ecosystem of preliminary entry brokers has grown, together with darkish markets like Genesis Market, which was seized and shut down by the FBI in a multinational sting operation. These hubs facilitate transactions between IABs and risk actors searching for credentials, tokens, compromised endpoints, company logins, internet shells, cPanels or different filched entry factors to enterprise networks.
The examine pointed to 2 broad market classes of access-for-sale on the cybercriminal underground:
- IABs auctioning entry to enterprise networks for tons of to hundreds of {dollars}.
- Wholesale entry markets promoting entry to compromised endpoints for round $10.
Over 4.5 million entry vectors had been bought in 2021, adopted by 10.3 million in a single market in 2022, the examine revealed.
Thanos mentioned IABs discern which credentials will work in a sure setting, after which they promote them in blocks.
“They are saying to the ransomware operators, ‘Look, we have now entry to group X, Y and Z, and we expect they are going to pay between X and Y {dollars}.’ And so they know this as a result of in addition they do reconnaissance, in order that they know the enterprise – they know the anticipated payout for a ransomware assault,” he defined. “And all they do is present the credentials and take a minimize.”
What they supply may very well be passwords, API keys, tokens, Thanos mentioned, “Or something that’s going to grant you the entry. Typically it’s simply that they know that there’s a sure vulnerability within the setting, they usually promote that.”
Poor digital hygiene provides risk actors entry to bigger payouts
Thanos identified that plenty of credentials bought on the darkish internet, whereas from particular person shopper accounts, can represent entry factors to organizations because of poor digital hygiene: Individuals utilizing the identical login info for enterprises as they do for private accounts, permitting entry and lateral motion via organizations.
“They’re typically utilizing the identical passwords for his or her company entry, so sadly, the private and the enterprise worlds are intertwined. Dangerous guys then exit to social media – Linkedin, for instance – to get names, after which apply automation to match names to IDs after which strive the stolen password.”
Typically that is finished by credential stuffing the place combolists, that are mixed textual content information of leaked usernames and passwords, obtained from earlier breaches are used to take over accounts on different internet or cellular purposes via brute pressure assaults.





