A brand new variant of malware known as XLoader is focusing on macOS customers. XLoader’s execution, functionalities and distribution are detailed.

A brand new report from cybersecurity firm SentinelOne exhibits how the XLoader malware developed. This data stealer malware has focused macOS since 2015, but it surely was not too long ago up to date. It now pretends to be an Workplace utility, so it will probably infect customers’ machines and steal data from their clipboards and browsers.
Bounce to:
What’s XLoader, and the way did it replace?
XLoader is an data stealer and keylogger malware-as-a-service first reported by SentinelOne in 2021. Nonetheless, the malware was developed from the supply code of Formbook, an data stealer malware and keylogger that was energetic between 2015 and 2021. Whereas Formbook solely focused Microsoft Home windows working programs, XLoader began focusing on Home windows and macOS.
The primary variations of XLoader wanted the Java Runtime Atmosphere to be executed efficiently. Since Apple stopped transport JRE on macOS years in the past, it has been much less efficient than different malware, though many customers on macOS nonetheless want JRE for various functions and have it put in on their programs.
SentinelOne’s researchers Dinesh Devadoss and Phil Stokes report that XLoader has returned in a brand new type and with out these Java dependencies. The brand new code is written in C and Goal C programming languages and signed with an Apple developer signature from “Mait Jakhu” (Determine A).
Determine A
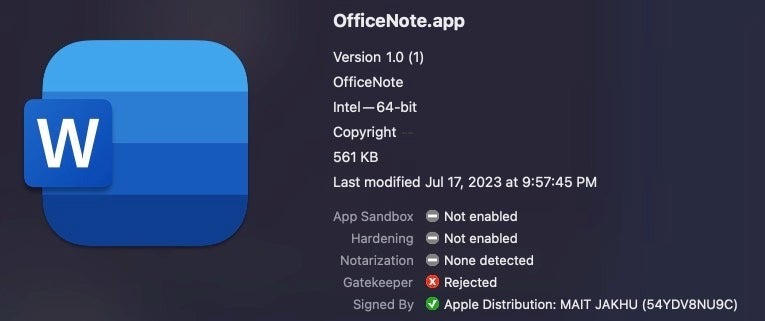
The signature date is July 17, 2023, but it surely has since been revoked by Apple. Which means if a consumer tries to execute the file on a Mac, the working system will present a warning about it (Determine B) and won’t execute it.
Determine B
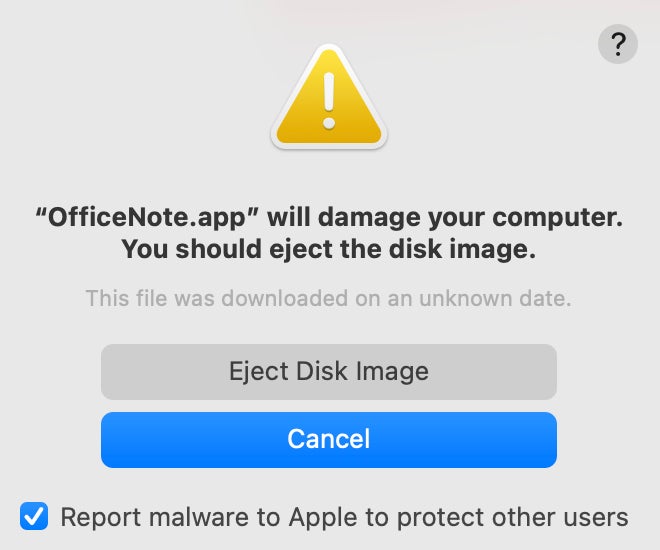
XLoader’s execution and functionalities
The XLoader malware has the flexibility to steal passwords from many browsers on Home windows and Mac, but its Mac model is restricted to stealing passwords from Google Chrome and Mozilla Firefox and stealing content material from the pc’s clipboard. It has anti-debug capabilities and makes use of sleep instructions to attempt to forestall it from being analyzed by automated safety options.
As soon as XLoader is launched, it exhibits an error indicating the software program doesn’t work, whereas silently dropping its payload and putting in persistence within the background.
The malware creates a hidden folder within the consumer’s dwelling listing and builds an executable inside that folder, utilizing randomized names for each the folder title and the applying. A LaunchAgent can also be dropped in the identical folder and used for persistence.
XLoader then tries to disguise its actual command-and-control server by sending dummy community calls to roughly 200 servers unrelated to the malware.
How is XLoader distributed?
The malware samples found by SentinelOne are named OfficeNote.app and faux to be Workplace purposes by exhibiting an icon impersonating Microsoft Phrase. XLoader is delivered as a regular Apple disk picture named OfficeNote.dmg.
The researchers famous that a number of submissions of the brand new XLoader malware pattern appeared all through July 2023 on the VirusTotal platform, which is a system devoted to operating a number of antivirus engines on submitted recordsdata. This can be a signal that the malware has been extensively distributed within the wild.
The brand new XLoader is being marketed in cybercriminals’ underground boards for $199 USD monthly or $299 USD per quarter for its Mac model, whereas the Home windows model is cheaper at $59 USD monthly or $129 USD per quarter.
The dashboard accessible to XLoader clients is proven as a screenshot in underground boards to present cybercriminals perception into its functionalities and ease of use.
How are you going to shield your online business from this XLoader malware risk?
The best way the Apple disk picture is delivered to customers is unknown; the most typical strategies for such file supply are through e-mail campaigns, direct downloads from untrusted areas or through social media platforms or instantaneous messaging. In an effort to shield your online business from this XLoader malware risk, it’s strongly suggested to:
- Monitor e-mail utilizing safety options that analyze all of the hooked up recordsdata and hyperlinks to obtain recordsdata.
- Monitor community logs for any endpoint or server that abruptly sends lots of DNS decision requests and initiates communications with many alternative hosts or IP addresses inside seconds.
- Run safety software program on all endpoints and servers to stop and detect malware equivalent to XLoader.
- Prohibit customers from downloading and operating purposes originating from untrusted utility shops or servers.
- Maintain all working programs — on this case, notably macOS — up to date to the most recent model and patched to keep away from being compromised by frequent vulnerabilities.
Disclosure: I work for Development Micro, however the views expressed on this article are mine.










