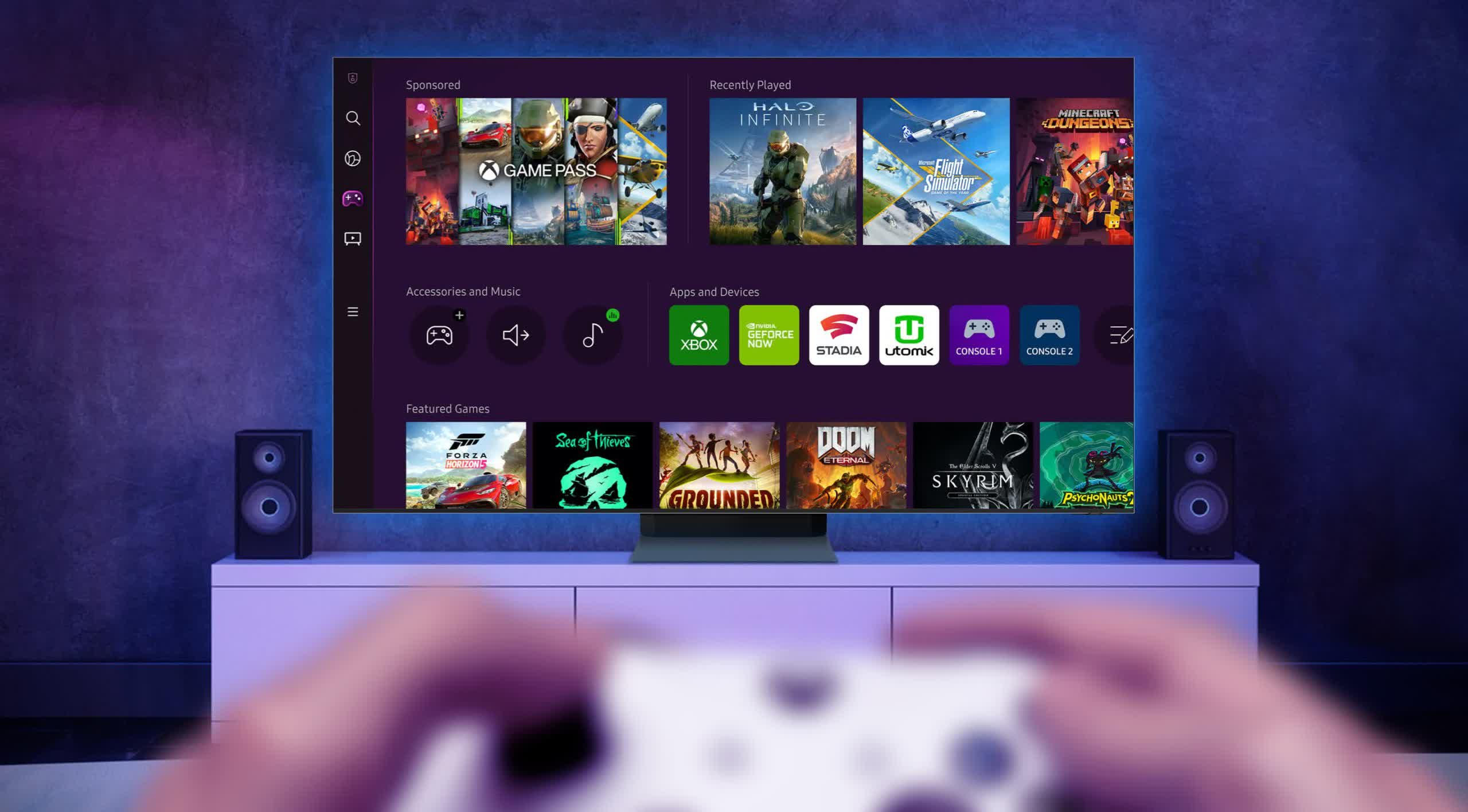
Most organizations surveyed by Titaniam have current safety prevention and backup instruments, however virtually 40% have nonetheless been hit by ransomware assaults within the final yr.

Conventional cybersecurity merchandise had been as soon as sufficient to guard organizations towards viruses and hacking makes an attempt. However at this time’s cyber threats are extra prevalent, extra refined and extra harmful, requiring extra sturdy safety defenses. A report launched Thursday by cybersecurity agency Titaniam seems on the incapability of conventional safety merchandise to guard towards ransomware particularly.
SEE: Learn how to turn into a cybersecurity professional: A cheat sheet (TechRepublic)
For its State of Knowledge Exfiltration & Extortion Report, Titaniam commissioned CensusWide to survey 107 IT safety professionals within the U.S. about their experiences with cybersecurity and ransomware. Among the many respondents, greater than 75% stated that they had instruments in place for knowledge safety, prevention and detection, and knowledge backup and restoration. To guard their knowledge, the professionals surveyed pointed to such applied sciences as encryption, together with encryption at relaxation and encryption in transit; knowledge masking; and tokenization.
Knowledge exfiltration thwarts conventional safety efforts
Nonetheless, the defenses in place didn’t shield the organizations towards ransomware assaults. Virtually 40% of them have been hit by ransomware assaults within the final yr, whereas greater than 70% have seen such an assault towards them over the previous 5 years.
One tactic more and more favored by many ransomware gangs is double extortion. In any such incident, the compromised knowledge isn’t just encrypted however exfiltrated by the attacker. Until the ransom is paid, the criminals vow to not solely hold the hacked knowledge encrypted however to launch it publicly. Which means an information backup alone isn’t ample to thwart the ransom demand.
With knowledge exfiltration makes an attempt up greater than 100% from 5 years in the past, 65% of the respondents who had been hit by a ransomware assault additionally skilled knowledge theft or exfiltration. Amongst these victims, 60% stated the attackers used the stolen recordsdata to extort them additional by threatening to leak the info. Because of this, 59% of them felt that they had no alternative however to pay the ransom.
Understanding the completely different levels of ransomware assaults
With knowledge exfiltration and double extortion ways in play, how can organizations higher shield themselves from ransomware assaults? Titaniam CEO and founder Arti Raman gives a number of items of recommendation.
“You can’t safe your self towards one thing you don’t correctly perceive, so the very first thing organizations must do is to interrupt down the how and why of ransomware assaults and look at these in gentle of their very own group,” Raman stated. “Particularly, ransomware assaults contain three distinct levels: infiltration, knowledge exfiltration, and system lockup through encryption.
“Success on any of those levels ends in a win for attackers, as they now have extra leverage to extort the sufferer.”
The completely different levels work as follows:
- Infiltration: As soon as they’ve infiltrated a community, attackers can monitor victims’ behaviors and set up backdoors. This sort of exploitation will be bought as info or as entry to different criminals.
- Knowledge Exfiltration: This can be probably the most worthwhile stage, as attackers can use the stolen info to demand ransom from victims, their prospects, their companions, their board members and even their staff.
- System Lockup: Attackers can stop the sufferer from accessing their very own methods, particularly damaging if the group lacks the correct backup and restoration strategies.
“When you perceive these three distinctly, it turns into clear that every should be accounted for individually in your ransomware and extortion protection technique,” Raman defined.
SEE: Ransomware: How executives ought to put together given the present menace panorama (TechRepublic)
Community protection towards the levels of ransomware assaults
To begin with, organizations should spend money on prevention and detection methods to mitigate infiltration. Nonetheless, that is solely the beginning, as attackers can nonetheless reap the benefits of stolen credentials to bypass some of these instruments.
To forestall knowledge exfiltration, organizations should spend money on all three forms of encryption, particularly encryption at relaxation, encryption in transit and most significantly encryption in use. The most recent kind of safety out there, encryption in use secures each structured and unstructured knowledge whereas it’s actively getting used. With this stage of encryption, attackers utilizing stolen credentials can’t entry knowledge even with privileged entry. Nor can they seize knowledge dumped from reminiscence or by querying databases. Because of this, encryption in use is a stable protection towards data-related facets of ransomware assaults.
Within the occasion an attacker is ready to infiltrate a community, organizations can guard towards system lockout by investing in backup and restoration options.
“Specializing in only one or two … is actually not ample, as evidenced by 1000’s of profitable ransomware assaults which have already taken place this yr,” Raman stated. “A whole ransomware protection technique ought to embody all three.”
Nonetheless, ransomware gangs are more and more apt to focus extra on knowledge exfiltration and fewer on system lockup, in keeping with Raman. For attackers, it might appear simpler to easily steal knowledge and threaten to reveal it reasonably than danger getting caught whereas taking the time to encrypt recordsdata and cope with decryption expertise.
Subsequently, in keeping with Raman, it’s higher for firms to concentrate on growing methods that mitigate knowledge exfiltration together with decreasing infiltration and system lockup makes an attempt.