Two zero-day vulnerabilities have been found in Ivanti Safe VPN, a well-liked VPN resolution utilized by organizations worldwide. The vulnerabilities are at the moment being exploited within the wild by at the least one Chinese language nation-state risk actor dubbed UTA0178. The chaining of the 2 vulnerabilities enable any attacker to execute distant code with none authentication and compromise affected techniques.
What are the Ivanti Safe VPN zero-day vulnerabilities?
Ivanti revealed an official safety advisory and data base article about two zero-day vulnerabilities, CVE-2023-46805 and CVE-2024-21887, affecting all supported variations of Ivanti Join Safe (beforehand often called Pulse Join Safe) and Ivanti Coverage Safe Gateways.
- CVE-2023-46805 is an authentication bypass vulnerability within the net part of Ivanti Join Safe and Ivanti Coverage Safe. It permits an attacker to entry restricted sources by bypassing management checks.
- CVE-2024-21887 is a command injection in net elements of Ivanti Join Safe and Ivanti Coverage Safe. It permits an authenticated administrator to ship specifically crafted requests and execute arbitrary instructions on the equipment and may be exploited through the web.
When mixed, these two vulnerabilities enable an attacker to run instructions on affected home equipment.
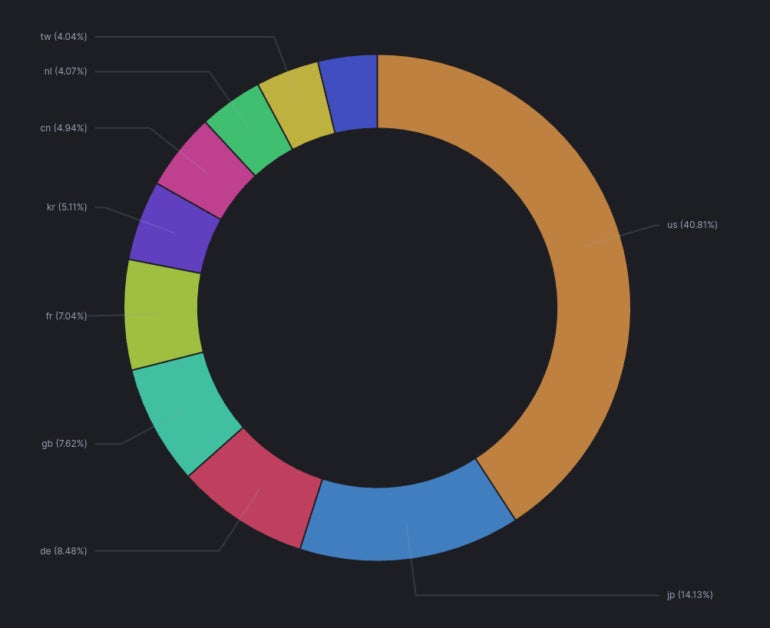
Patrice Auffret, founder, chief govt officer and chief expertise officer at ONYPHE, a French cyber protection search engine devoted to assault floor discovery and assault floor administration, informed TechRepublic in an e mail interview earlier immediately that 29,664 Ivanti Safe VPN home equipment are linked to the web, with greater than 40% of the uncovered techniques being within the U.S., adopted by Japan (14.3%) and Germany (8.48%) (Determine A).
Determine A
Exploitation of those zero-day vulnerabilities within the wild
U.S.-based cybersecurity firm Volexity found each vulnerabilities throughout an incident response investigation throughout a number of techniques. The incident response revealed {that a} risk actor modified a number of recordsdata positioned on the Ivanti Join Safe VPN equipment (Determine B).
Determine B
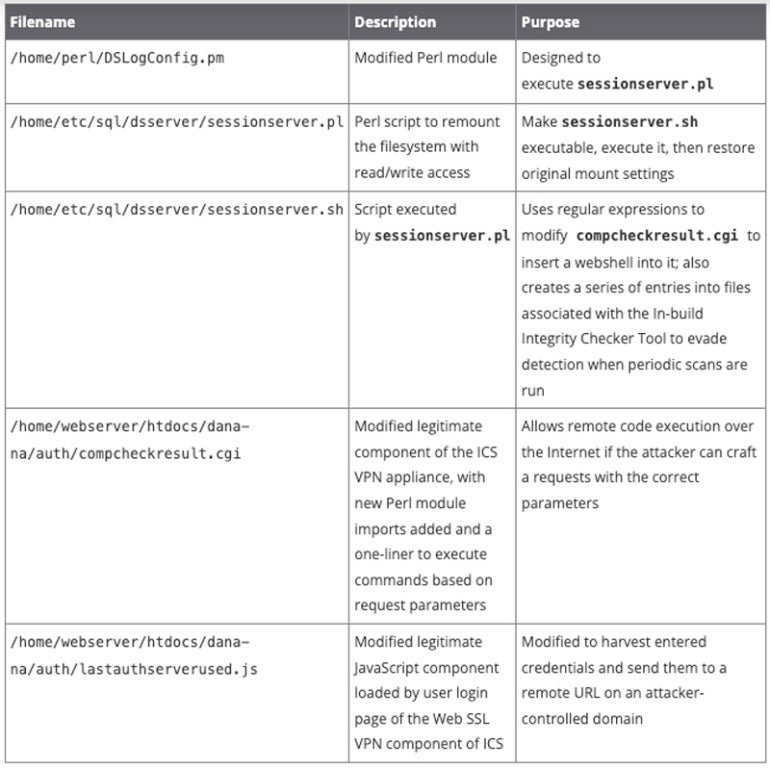
Volexity additionally believes a lot of recordsdata have been created and used/executed within the system’s non permanent folder (/tmp) however have been now not accessible for investigation on the time of the incident response, reminiscent of:
- /tmp/rev
- /tmp/s.py
- /tmp/s.jar
- /tmp/b
- /tmp/kill
A Python-based proxy utility, PySoxy, believed to be s.py, was discovered on a disk picture. It’s a SOCKS5 proxy script freely accessible on the web.
The risk actor, dubbed UTA0178 by Volexity, deployed webshells and modified recordsdata to permit credential theft earlier than shifting from system to system utilizing the compromised credentials. The risk actor saved gathering newly harvested credentials on each system they hit, and was noticed dumping a full picture of the Lively Listing database. Lastly, the attacker modified the JavaScript loaded by the online login web page for the VPN equipment to seize any credential supplied to it. The reliable lastauthserverused.js script was modified to ship the stolen credentials to an attacker-controlled area: symantke(.)com.
As soon as in possession of credentials, the risk actor explored the community, consumer recordsdata and configuration recordsdata, and deployed extra webshells on the community, together with a customized webshell dubbed GLASSTOKEN.
Customized GLASSTOKEN webshell
Whereas the risk actor made use of a number of public and recognized instruments, GLASSTOKEN was deployed in two barely totally different variations.
The primary model contains two code paths, relying on the parameters supplied within the request. The primary path is used to relay a connection, whereas the second is used to execute code that’s decoded from hexadecimal earlier than being base64 decoded. In accordance with Volexity’s observations, the risk actor used it principally to execute PowerShell instructions.
The second model of the webshell is near the primary one besides that it misses the proxying characteristic, solely permitting code execution.
Full code for these webshells has been supplied by Volexity.
Risk detection
Community visitors evaluation
Cautious evaluation of the outbound visitors from the VPN equipment can detect suspicious exercise. Apart from the reliable join again to pulsesecure.internet and every other customer-related configured integration (SSO, MFA and many others.), any suspicious exercise ought to be analyzed. Examples as noticed by Volexity are curl requests to distant web sites, SSH connections to distant IP addresses, or encrypted communications to hosts that aren’t related to suppliers or system updates.
Exercise on the inbound community visitors from IP addresses related to the VPN equipment must also be checked fastidiously. Suspicious visitors that is likely to be noticed on such connections may be RDP or SMB exercise to inner techniques, SSH connection makes an attempt or port scanning, to call just a few.
VPN system log evaluation
Any indication that the VPN home equipment log recordsdata have been wiped or disabled is a robust indicator of compromise, in case it was beforehand energetic.
Requests for recordsdata in atypical paths within the logs must also be regarding and analyzed, as risk actors would possibly retailer or manipulate recordsdata out of the same old folders.
Integrity Checker instrument
The In-Construct Integrity Examine instrument can be utilized to run routinely and detect new or mismatched recordsdata. As written by Volexity’s researchers, “if any new or mismatched recordsdata are listed, the system ought to be thought-about compromised.”
Ivanti gives an exterior model of the Integrity Checker instrument, which ought to be utilized in case the system is suspected of being compromised. The instrument ought to solely be put in and launched in spite of everything forensic proof has been collected from the system — particularly a reminiscence picture as a result of the execution of the instrument will reboot the equipment and probably overwrite proof knowledge.
Risk mitigation
Ivanti gives a mitigation methodology till a full patch will likely be accessible. Ivanti signifies that “patches will likely be launched in a staggered schedule with the primary model focused to be accessible to clients the week of twenty-two January and the ultimate model focused to be accessible the week of 19 February.”
The mitigation consists of importing a mitigation.launch.20240107.1.xml file through the obtain portal. Relying on the configuration, system degradation would possibly end result from this operation, as listed on the devoted Ivanti web page. It’s strongly suggested to fastidiously observe all of Ivanti’s directions and verify that the mitigation is working appropriately.
Disclosure: I work for Development Micro, however the views expressed on this article are mine.










