A safety researcher, often known as ‘Cellular Hacker’, has proven how weak unpatched Android telephones are. Of their demonstration, they revealed a probably devastating zero-click assault that exploits newly uncovered Bluetooth vulnerabilities to put in intrusive payloads by way of Metasploit, a preferred penetration testing framework, onto gadgets that have not obtained their newest patches.
‘Cellular Hacker’ used proof-of-concept (PoC) exploitation scripts which have been launched by Marc Newlin earlier this month. These scripts are freely accessible on GitHub and make the most of the weaknesses tracked as CVE-2023-45866, CVE-2024-21306, and CVE-2024-0230 (extra data). They successfully force-pair emulated keyboards via Bluetooth to totally different OS architectures, thereby enabling keystroke injection.
What’s actually alarming about these scripts is that they work on gadgets the place Bluetooth is enabled and lively, which means they’re in an unlocked state. The assault can spring from one other cell system inside Bluetooth vary with out requiring any interplay with the sufferer or leaving any noticeable indicators of a breach. This vulnerability highlights the significance of maintaining our gadgets up to date and vigilant towards potential threats lurking in our digital house.
These assaults are as stealthy as they sound and might impression unpatched Android telephones. Let’s dive deeper to know this contemporary menace.
Zero-click assaults, for individuals who could not know, are cyber threats that do not require any interplay from the sufferer – no clicking on suspicious hyperlinks or downloading rogue purposes. The hacker wants proximity to execute these nefarious actions by way of Bluetooth. The vulnerability in query impacts a variety of working techniques throughout totally different gadgets but it surely’s particularly regarding for older Android variations.
Why is that this so? Properly, think about the truth that most Android distributors cease supporting gadgets after solely two years and observe rare updating circles (quarterly at finest). This implies safety updates get delayed typically for months making these gadgets ripe targets for hackers exploiting Bluetooth vulnerabilities.
To present you a clearer image, all Android gadgets working model 10 and older are weak to those Bluetooth flaws. They’re basically sitting geese for zero-click assaults except patched instantly. As for newer variations like Android 11 to 14 which have lively assist, the failings have been addressed within the December 2023 patch.
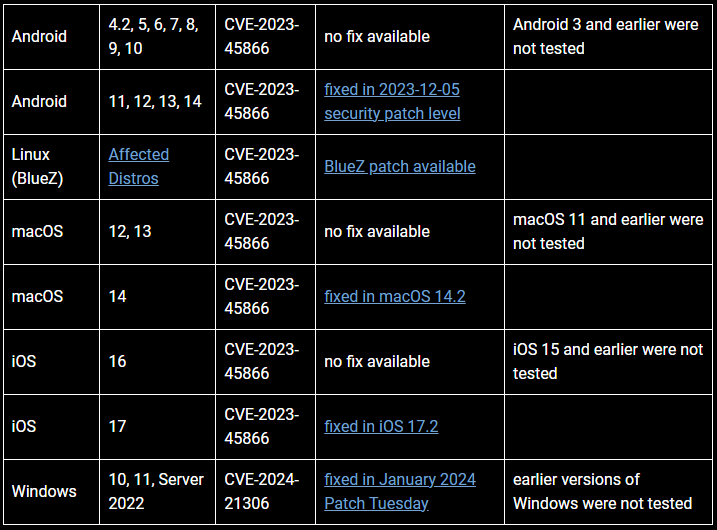
Not like their Android counterparts although Apple’s iPhones had their flaws mounted by iOS replace 17.2 however left earlier variations utilized by older fashions uncovered. MacOS mounted its flaw in model 14.2 whereas Microsoft issued fixes for Home windows 10,11 and Server 2022 of their January ‘Patch Tuesday’ launch of updates in 2024. Older macOS variations like 12 and 13 are weak, and no fixes will probably be made out there.
If you’re unable to improve to a protected model I like to recommend both disabling Bluetooth or maintaining their telephones locked when in public areas with many individuals close by.
Commercial