A passkey is a particular authentication methodology that can be utilized as generally as a password however to offer extra safety. Passkeys differ from passwords as they mix non-public and public cryptographic keys to authenticate customers, whereas a password depends on a particular variety of characters.
In keeping with Google, probably the most quick advantages of passkeys are that they’re phishing-resistant and spare individuals the headache of remembering numbers and particular characters in passwords.
As passwordless authentication continues to evolve — in response to phishing-related dangers — think about using passkeys to implement an added layer of safety to guard your on-line accounts and information.
This text will outline passkey expertise, discover the way it works and talk about the added safety advantages of utilizing a passkey.
1
ESET PROTECT Superior
Workers per Firm Measurement
Micro (0-49), Small (50-249), Medium (250-999), Massive (1,000-4,999), Enterprise (5,000+)
Any Firm Measurement
Any Firm Measurement
Options
Superior Menace Protection, Full Disk Encryption , Fashionable Endpoint Safety, Server Safety
2
ManageEngine Desktop Central
Workers per Firm Measurement
Micro (0-49), Small (50-249), Medium (250-999), Massive (1,000-4,999), Enterprise (5,000+)
Any Firm Measurement
Any Firm Measurement
Options
Exercise Monitoring, Antivirus, Dashboard, and extra
3
Dashlane
Workers per Firm Measurement
Micro (0-49), Small (50-249), Medium (250-999), Massive (1,000-4,999), Enterprise (5,000+)
Micro (0-49 Workers), Small (50-249 Workers), Medium (250-999 Workers), Massive (1,000-4,999 Workers), Enterprise (5,000+ Workers)
Micro, Small, Medium, Massive, Enterprise
Options
Automated Provisioning
What’s a passkey?
A passkey refers to a code or a collection of characters used to achieve entry to a secured system, machine, community or service. Passkeys are sometimes used together with usernames or consumer IDs to create two-factor authentication (2FA).
After you’ve established a passkey, all you want to do is log in to finish the authentication course of, usually utilizing biometric information comparable to a fingerprint or facial recognition. For individuals who make the most of a passkey, logging in turns into a easy, practically computerized course of; for malicious actors, it turns into practically inconceivable.
The implementation of passkeys is very adaptable since they could be configured to be cloud-synced or hardware-bound, contingent on the consumer’s selections concerning the actual utility, service or machine.
How do passkeys work?
When logging in for the primary time, a consumer who needs to entry an app or web site with passkey expertise — comparable to NordPass — shall be requested to generate an unique passkey. This passkey, which shall be required for authentication sooner or later, may be accessed utilizing both biometrics or private PINs based mostly on the consumer’s choice and the capabilities of their most popular machine.
Determine A
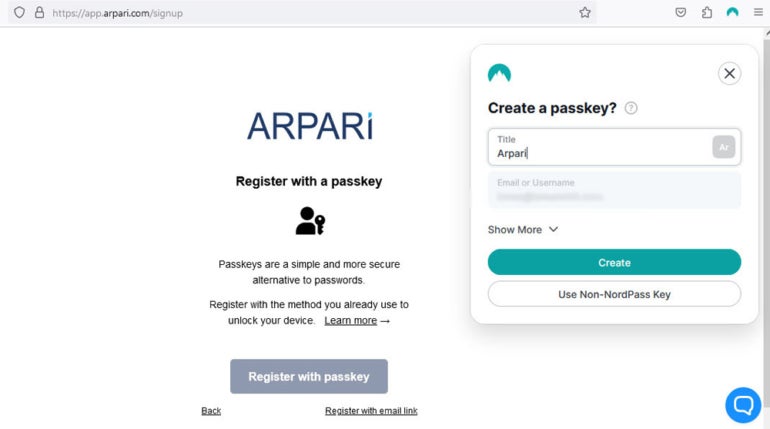
Throughout this stage, two mathematically linked cryptographic keys are generated: a public key that stays with the web site, service or utility however is linked to the account, and a non-public key that stays on the consumer’s {hardware} or cloud account. The service or utility will ship a randomly generated “problem” to the consumer’s machine throughout successive logins, which the consumer should react to by signing in with the non-public key.
The app or web site can verify the legitimacy of the non-public key by using the corresponding public key to substantiate the response. Entry is allowed, and authentication is validated if the consumer’s verified signature connected to the problem’s response agrees with the unique randomly generated problem; if not, entry is denied.
This authentication course of is completed within the background, making login on the consumer’s finish seamless — with simply the press of a button.
Determine B
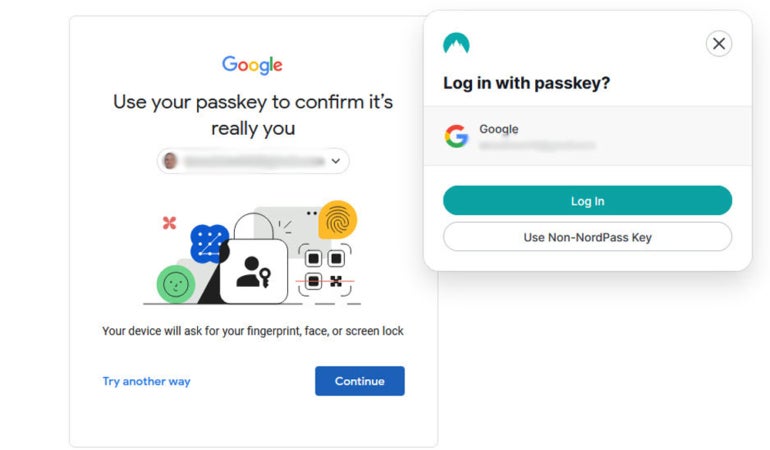
Can passkeys be shared?
The implementation of passkey expertise continues to be growing, however some firms have talked about the potential for credential sharing amongst customers — so long as the precise passkeys are saved protected within the cloud and out of the palms of potential hackers. Since sharing account entry with household, buddies and coworkers is a quite simple and fast course of, this function might enhance the general consumer expertise. Nevertheless, it’s nonetheless unclear how this perform may be securely managed in a enterprise setting.
One other essential issue to contemplate is whether or not companies ought to turn into much more depending on cloud suppliers and quit much more possession and management over credential administration, given {that a} breach of these events’ information would, surely, have disastrous penalties.
{Hardware}-bound passkeys, versus cloud-based passkeys, are saved on safety keys, bodily {hardware} authenticators or specialised {hardware} built-in into laptops and desktops. Which means that the passkey is neither transferable nor duplicated. {Hardware}-bound passkeys may be an alternate for organizations wanting to forestall staff from copying or sharing keys throughout units.
Are passkeys safer than passwords?
Generally, each passkeys and passwords may be safe if managed correctly. Nevertheless, safety will depend on varied components, together with the complexity of authentication, implementation and the way effectively customers handle and shield their credentials. To be deemed safe by right now’s requirements, passkeys and passwords ought to have the next traits:
- Complexity: The longer and extra complicated the passkey or password, the tougher it’s for unhealthy actors to compromise.
- 2FA: A second issue of authentication can improve safety for each passkeys and passwords, making it more difficult for unauthorized customers to achieve entry.
- Encryption: Sturdy encryption strategies are essential for safeguarding saved credentials.
In the end, the safety of passkeys and passwords isn’t inherently dependent upon the kind of credential however as an alternative how they’re applied and managed.










