Mishaal Rahman / Android Authority
TL;DR
- Google could also be cracking down on a recognized Android safety assault methodology in Android 15.
- Malicious apps that may learn your notifications can intercept one-time passwords (OTPs) and hijack your accounts, and Google desires to forestall this.
- Code inside Android 15 suggests Google may cease untrusted apps from studying notifications with OTPs.
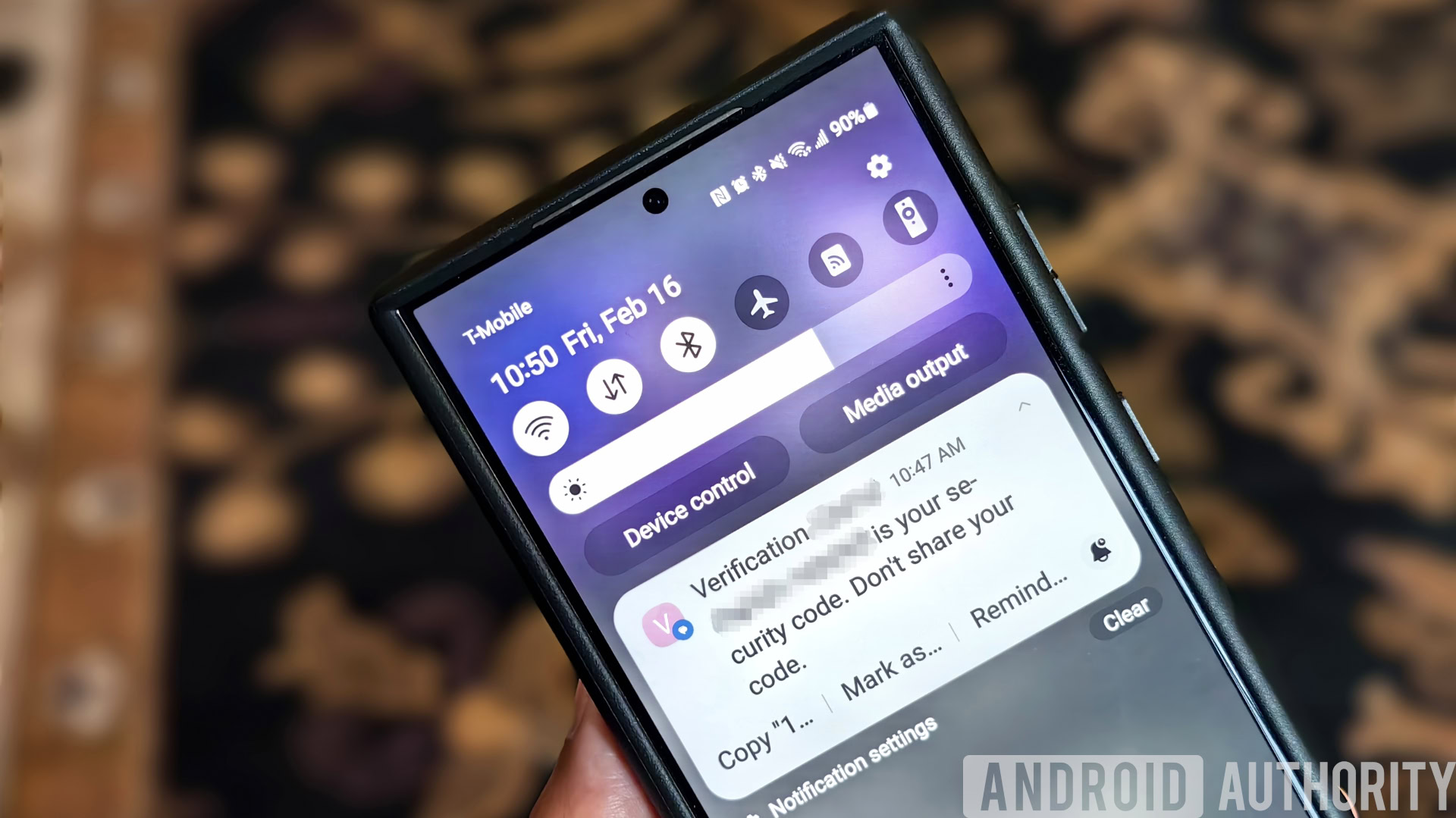
It’s important to guard your on-line accounts in order that they don’t fall into the fingers of hackers, which is why it is best to use a passkey or allow two-factor authentication (2FA) each time potential. Whereas some types of 2FA are safer than others, some platforms solely assist probably the most fundamental strategies, whereby your one-time passwords (OTPs) are despatched through e-mail or textual content. These strategies are handy since they don’t require further setup, however they’re additionally much less safe since they’re simpler to intercept. Thankfully, Android 15 is likely to be including a brand new function that forestalls your OTPs from being learn by malicious Android apps.
Whereas digging by the Android 14 QPR3 Beta 1 replace, I found the addition of a brand new permission named RECEIVE_SENSITIVE_NOTIFICATIONS. This permission has a protectionLevel of position|signature, which implies it might solely be granted to functions with the requisite position or to functions that the OEM indicators. Whereas the precise position that grants this permission hasn’t been outlined but, it’s doubtless that Google doesn’t intend to open this permission as much as third-party apps.
<permission android:title="android.permission.RECEIVE_SENSITIVE_NOTIFICATIONS" android:protectionLevel="position|signature"/>
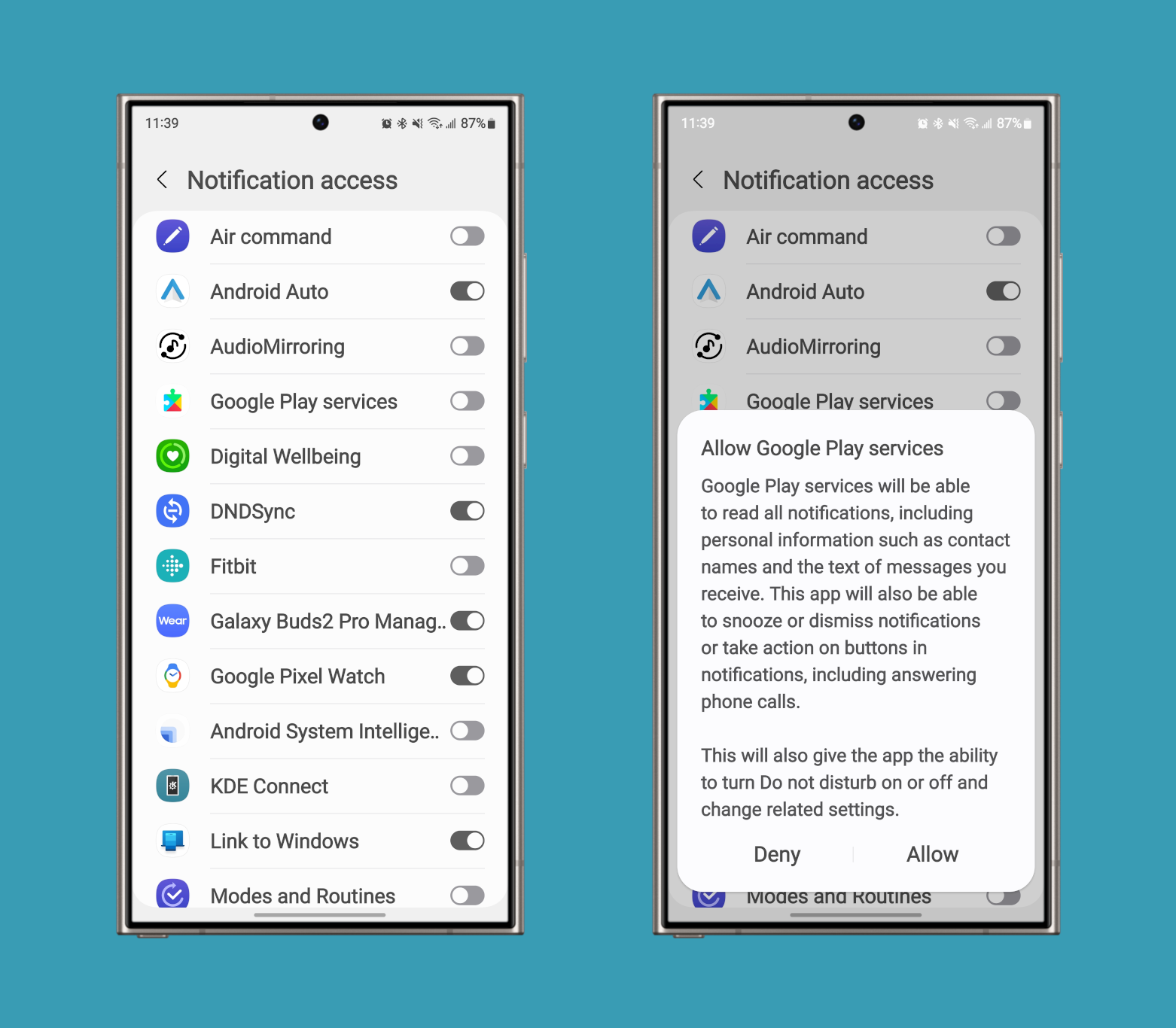
As for why I imagine that, it’s as a result of this permission is tied to a brand new, in-development platform function that goals to redact delicate notifications from untrusted apps that implement a NotificationListenerService. That is an API that lets apps learn or take motion on all notifications. Customers must manually grant apps permission in Settings earlier than the NotificationListenerService API turns into out there, although.
Mishaal Rahman / Android Authority
Notification entry settings in Android 14 on a Galaxy S24 Extremely.
Given how highly effective this permission and API are, it’s no shock that Google would wish to restrict the type of knowledge that apps can get from them. We don’t know exactly what constitutes an “untrusted” app, but it surely’s doubtless any apps that don’t maintain the brand new RECEIVE_SENSITIVE_NOTIFICATIONS permission. This permission would most likely solely apply to pick system apps.
We additionally don’t know precisely what sorts of notifications Google thinks are “delicate,” however we’ve got cause to imagine they’re referring to notifications with 2FA codes. Whereas digging by the supply code for Android 14, we found a brand new flag referred to as OTP_REDACTION that’s used to gate “the redaction of OTP notifications on the lock display.” This flag is at present unused in Android 14, although, because it’s doubtless one thing that Google intends to launch with Android 15.
With the addition of the OTP_REDACTION flag and the RECEIVE_SENSITIVE_NOTIFICATIONS permission, Android can have 3 ways to guard customers from leaking their 2FA codes to 3rd events. The OTP_REDACTION flag means that Android will cease customers from leaking their 2FA codes on the lock display, whereas the RECEIVE_SENSITIVE_NOTIFICATIONS permission means that Android will cease untrusted apps from studying notifications with 2FA codes. Lastly, an present function from Android 13 blocks customers from enabling an app’s notification listener service if it was put in from an untrusted supply.







.jpeg)

