Would-be cybercriminals can simply purchase superior instruments, widespread exploits, and stolen credentials on underground markets for a number of {dollars} — a low barrier to entry for novices, in line with a research of 33,000 Darkish Internet marketplaces.
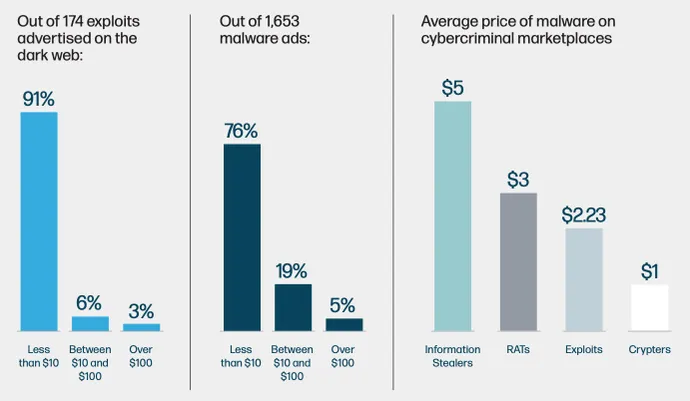
Based on new evaluation from HP Wolf Safety and researchers at Forensic Pathways, there are many bargains available. Out of the 174 exploits discovered marketed on the Darkish Internet, 91% price lower than $10, whereas 76% of the greater than 1,650 commercials for malware have an analogous value.
Different widespread attacker property even have equally low costs: The typical price, for instance, for stolen credentials for accessing a Distant Desktop Protocol (RDP) occasion is simply $5.
Whereas extra superior malware teams use personal boards to commerce zero-day exploits, the obtainable credentials, exploits, and instruments on supply within the wider underground financial system permit novices to shortly create a reputable toolset, says Alex Holland, senior malware analyst at HP and first creator of the report.
Novice cybercriminals “can use a freely obtainable open supply instrument, and — so long as you’re expert sufficient to encrypt, use a packer, use methods to evade defenses — then that instrument will do a superbly good job,” he says.
The research of Darkish Internet marketplaces analyzed roughly 33,000 lively websites, boards, and marketplaces over a two-month interval, discovering that the marketplace for fundamental instruments and information is nicely entrenched, and attracting new clients on a regular basis.
The rise within the variety of risk actors may imply companies will discover their operations focused much more than they’re at present, in line with Michael Calce, HP Safety Advisory Board member and former hacker (aka MafiaBoy). HP introduced in criminologists and former hackers to assist put the research in context.
“Right this moment, solely a small minority of cybercriminals actually code, most are simply in it for the cash — and the barrier to entry is so low that just about anybody is usually a risk actor,” Calce says within the report. “That is unhealthy information for companies.”
To guard themselves from the swelling ranks of cyberattackers, HP recommends that corporations do the fundamentals, utilizing automation and greatest practices to scale back their assault floor space. As well as, companies must usually conduct workouts to assist plan for and reply to the worst-case assaults, as attackers will more and more try and restrict executives decisions following an assault to make ransom funds one of the best worst possibility.
“If the worst occurs and a risk actor breaches your defenses, then you don’t need this to be the primary time you’ve gotten initiated an incident response plan,” Joanna Burkey, chief data safety officer at HP, says within the report. “Guaranteeing that everybody is aware of their roles, and that persons are conversant in the processes they should observe, will go a protracted solution to containing the worst of the influence.”
Cybercrime Convergence: Nation-State Ways Mix With Monetary Campaigns
The report additionally discovered that superior actors have gotten extra skilled, utilizing more and more damaging assaults to scale up the strain on victims to pay. On the similar time, financially motivated cybercriminals teams proceed to undertake lots of the ways utilized by high-end nation-state risk actors.
These particularly deal with living-off-the-land assaults the place the attacker makes use of system administration instruments to keep away from endpoint-detection programs that will in any other case flag malware, in line with HP.
Whereas the shift probably comes from the switch of data as cybercriminals change into extra skillful and be taught the most recent ways utilized by superior persistent threats, a lot of teams are additionally mixing nation-state actions—equivalent to cyberespionage — and cybercriminal actions aimed toward turning a revenue. The leak of textual content messages from the Conti group highlighted that the members sometimes carried out operations on the request of not less than two Russian authorities companies.
Ransomware Is Right here to Keep
Elsewhere within the report, researchers observe that ransomware gangs will deal with timing their assaults to place probably the most strain on organizations, equivalent to attacking retailers through the vacation seasons, the agriculture sector throughout harvest seasons, or universities as college students return to highschool.
Ransomware has declined within the first half of the 12 months for varied causes, however HP sees the pattern as short-term.
“We do not see ransomware going away, however we do see it evolving over time,” Holland says. “Ransomware assaults will truly change into extra artistic.”
Imposing Ethics on the Darkish Internet
The research additionally discovered that belief continues to be a significant drawback for Darkish Internet markets in the identical manner that on-line companies have needed to take care of fraud and unhealthy actors. The Darkish Internet, after all, has sides that make belief even tougher to come back by: An internet site on the nameless Tor community, for instance, has a median lifespan of 55 days, in line with the researchers.
To make sure that distributors and clients play honest, the marketplaces have adopted lots of the similar methods as reputable companies. Distributors are normally required to supply a bond of 1000’s of {dollars} to make sure belief. Clients can depart rankings on each market. And escrow funds have change into commonplace, with 85% of transactions utilizing escrow fee programs.










