For the reason that begin of 2024, the Sophos X-Ops Managed Detection and Response (MDR) crew has responded to a number of incidents through which the preliminary entry vector has been recognized as an uncovered Microsoft Distant Desktop Internet Entry portal missing multi-factor authentication (MFA) safety. This text will present an outline of what we’ve got noticed when this portal is abused, add perception into how we conduct these investigations, and provides some suggestions and mitigating methods to assist anybody else that is perhaps encountering (or just anticipating) the identical state of affairs.
What’s the RD Internet Entry portal?
The Microsoft Distant Desktop Companies structure is made up of a number of distinct roles, as proven in Determine 1.

Determine 1: Instance of the roles put in on an uncovered Distant Desktop Companies (RDS) host
- The Distant Desktop Connection Dealer (RD Connection Dealer) position manages incoming distant desktop connections to RD Session Host server farms and routes connections to an acceptable host.
- The Distant Desktop Gateway (RD Gateway) position is chargeable for granting customers on public networks entry to Home windows desktops and functions hosted throughout the RDS cluster. This position is usually put in on the identical host because the RD Internet Entry position, mentioned under.
- The Distant Desktop Licensing (RD Licensing) position manages the consumer licenses and lets customers hook up with the RD Session Host servers internet hosting the digital desktops or functions.
- Lastly, the Distant Desktop Internet Entry (RD Internet Entry) login portal is the means by which customers, and in these investigations risk actors, authenticate and in the end attain the Distant Desktop Session Host (RD Session Host) – the aim on this stage. From the RD Session host, varied types of actions will be launched, for the reason that attacker has at that time achieved entry inside your system. (In MITRE ATT&CK, that is T1133, Preliminary Entry and Exterior Distant Companies.)
This text focuses on the RD Gateway, RD Internet Entry, and RD Session Host roles. For a broader have a look at how Distant Desktop Protocol (RDP) will be abused and the way attackers achieve this, please see the RDP sequence we printed earlier this yr.
What occurs when RD Internet Entry is abused?
When an RD Internet Entry host is uncovered to the Web, it permits customers to login with their area credentials to realize entry to an RD Session Host, or to a virtualized software that enables them to work from anyplace and achieve entry to essential enterprise assets. If these servers should not adequately protected whereas being uncovered on to the Web, they are often abused by risk actors to realize entry to an property. The login portals are generally brute-forced to realize professional consumer credentials, that are then used to login, create persistence, and try to escalate privileges and even transfer laterally throughout the property.
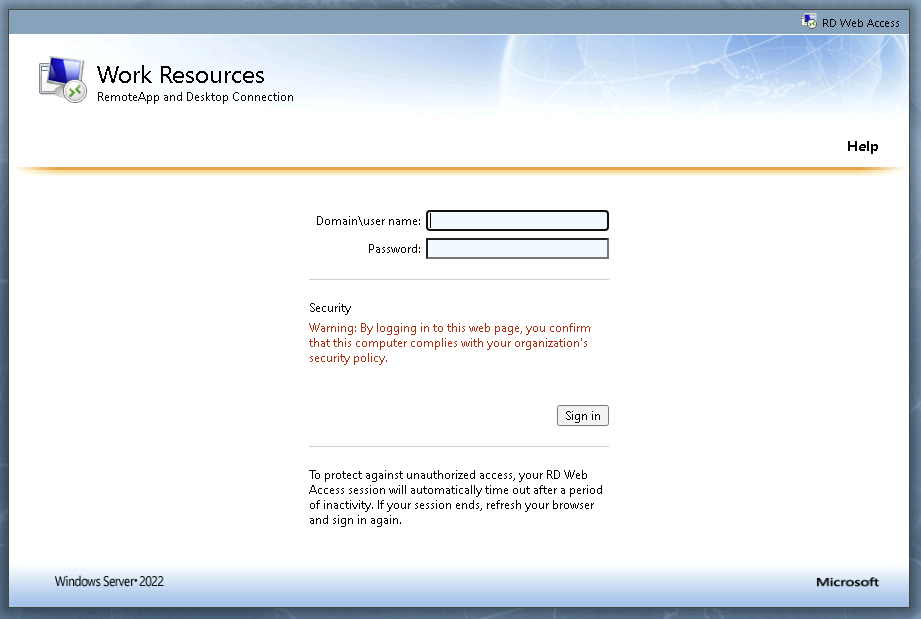 Determine 2: Default login web page for an RD Internet Entry portal
Determine 2: Default login web page for an RD Internet Entry portal
Upon profitable authentication, the consumer might be introduced with choices to connect with a printed RD Session Host or to a digital software. If solely introduced with digital functions, a malicious actor would wish to “escape” of the contained software to execute code on the underlying host.
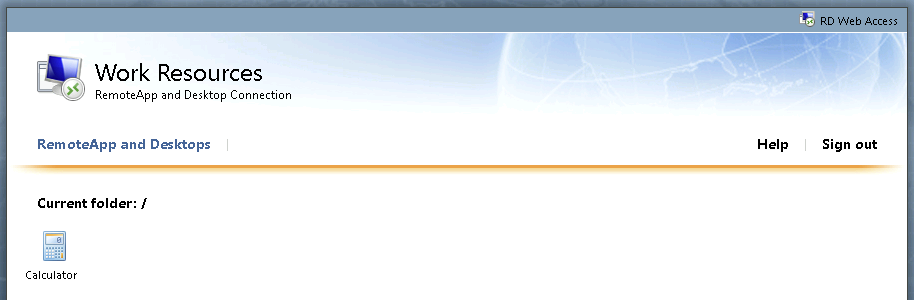
Determine 3: An RD Internet portal presenting solely a single printed digital software
The instance in Determine 3 reveals an RD Internet portal with only one software, the Home windows calculator, supplied. As soon as the consumer selects the appliance, an .RDP file might be downloaded that might be pre-configured to launch the Calculator software. Since on this case there isn’t a possibility to connect with a printed RD Session Host, the aim for risk actors on this state of affairs is to find out a option to execute code on the distant server that’s internet hosting the calculator software.
One method that has been noticed by MDR leverages built-in Home windows Accessibility performance to realize entry to a command immediate. When the Calculator software window has focus, the actor can press the shift key on their keyboard 5 instances to convey up the Sticky Keys immediate. This immediate might be loaded from the distant RD Session host. Inside the Sticky Keys immediate, there may be an choice to launch the accessibility choices Management Panel merchandise. This launches the Home windows Management Panel, which generally will outcome within the basic Management Panel loading in a Home windows Explorer window. From the Home windows Explorer search bar, the actor can now merely sort ‘cmd.exe’ and press enter to load an interactive command immediate on the RD Session host and start motion on their goals.
If introduced with the choice to connect with an RD Session Host, the actor might be logged immediately into an interactive Distant Desktop Session with a graphical consumer expertise, from which they’ll additional pursue their goals. When a direct connection is established from the RD Internet Entry host to any of the session hosts, authentication logs will present an interactive RDP logon from the RD Internet Entry host, though it serves as a proxy for the connection from the actor’s machine to the RD Session host.
In 4 out of the 5 RD Internet Entry incidents MDR analyzed for this text, the MDR crew responded to detections triggered within the discovery part of the assault, when the risk actor(s) executed the command ‘nltest / domain_trusts’ to enumerate whether or not any Energetic Listing trusts existed on the targets. (The fifth case we analyzed likewise triggered on this conduct, however first fired on a unique occasion, distinctive to that case.) Actors will usually execute discovery instructions to raised perceive the surroundings and underlying Energetic Listing area infrastructure to which they’ve efficiently gained entry.
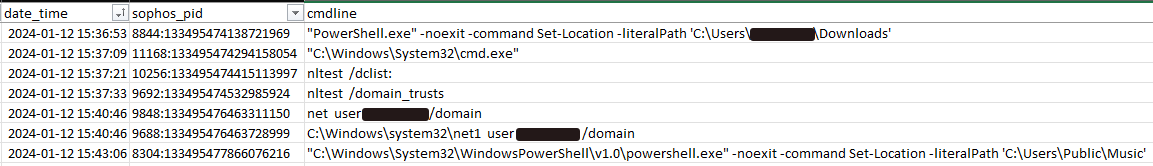
Determine 4: Examples of discovery instructions following a profitable connection
Upon investigation of those incidents, the MDR crew noticed constant brute drive makes an attempt directed on the IIS course of that serves the RD Internet Entry portal, ultimately ensuing within the risk actor gaining entry.
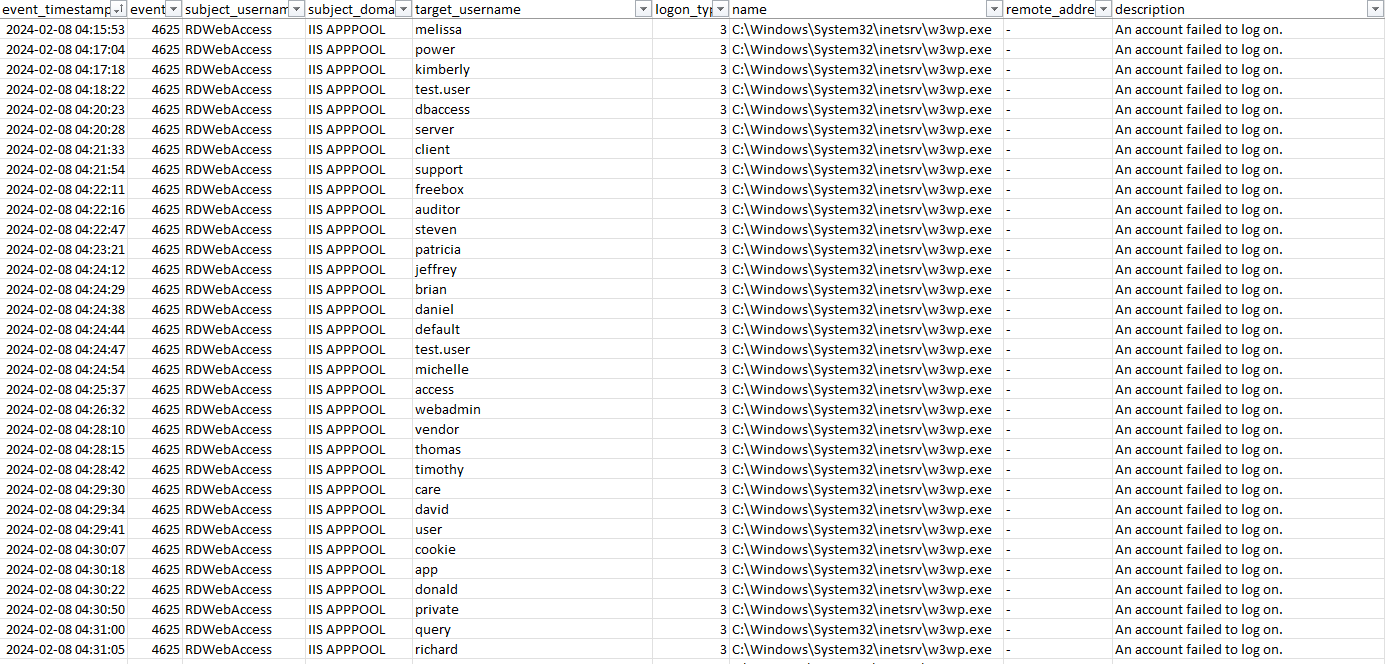
Determine 5: Examples of brute drive exercise in opposition to the RDWebAccess IIS course of
All through the triage part of an incident response, the MDR crew takes acceptable actions to disable any affected customers and disconnect any lively periods to include the risk as rapidly as doable. If a number of accounts present indicators of compromise, MDR can even isolate the RD Internet Entry host to in the end cease any additional entry to the property by way of that preliminary entry vector. The MDR crew makes use of quite a few queries to help with the investigation course of and have included a lot of them within the following Investigative Information part.
Investigative Information
On this part, we offer numerous queries that investigators can use in instances the place RD Internet Entry abuse is suspected. The queries on this part have been developed by the Sophos MDR crew and will be run throughout the Sophos Central portal by navigating to Menace Evaluation Middle -> Reside Uncover. For readers not at present utilizing Sophos Central, the overall recommendation nonetheless holds, however the processes ought to be undertaken based on the expertise you employ.
Figuring out uncovered RD Internet Entry portals by way of OSINT
Usually, a evaluation of the exterior assault surfaces reveals quite a few companies which are uncovered to the web. The next Shodan search can determine uncovered RDWeb servers.
hostname: path=/RDWeb/
Figuring out RD Gateway servers utilizing Reside Question
RD Gateway servers will be recognized by the presence of the Distant Desktop Gateway service named ‘TSGateway.’ That is an endpoint question, so you will have to pick out all on-line servers inside Sophos Central Reside Uncover to see which hosts have the RD Gateway position put in.
SELECT identify, display_name, start_type, path, standing FROM companies WHERE identify="TSGateway"
Reviewing RD Gateway logs
As soon as it has been decided {that a} managed host is working the RD Gateway position, you’ll be able to leverage the question under by way of Sophos Central Reside Uncover to acquire the newest connection occasions from the RD Gateway Home windows Occasion Logs. These logs will return the connection and disconnection occasions for the affected consumer and can reveal the distant supply IP handle chargeable for connecting to the session. As soon as the supply IP handle has been decided, it’s strongly beneficial that you simply block it at your community perimeter. That is an endpoint question, so you will have to pick out solely the hosts that had been proven within the earlier question (Figuring out RD Gateway servers utilizing Reside Question) to be working the RD Gateway position.
SELECT
strftime('%Y-%m-%d %H:%M:%S',swe.datetime) AS Datetime,
swe.time,
swe.eventid AS EventID,
CASE
WHEN eventid = 200 THEN 'Shopper Related'
WHEN eventid = 303 THEN 'Shopper Disconnected'
END AS Description,
JSON_EXTRACT(swe.knowledge, '$.UserData.Username') AS Username,
JSON_EXTRACT(swe.knowledge, '$.UserData.AuthType') AS AuthType,
JSON_EXTRACT(swe.knowledge, '$.UserData.IpAddress') AS IpAddress,
JSON_EXTRACT(swe.knowledge, '$.UserData.Useful resource') AS Useful resource,
JSON_EXTRACT(swe.knowledge, '$.UserData.BytesReceived') AS BytesReceived,
JSON_EXTRACT(swe.knowledge, '$.UserData.BytesTransfered') AS BytesTransfered,
JSON_EXTRACT(swe.knowledge, '$.UserData.SessionDuration') AS SessionDuration,
JSON_EXTRACT(swe.knowledge, '$.UserData.ConnectionProtocol') AS ConnectionProtocol
FROM sophos_windows_events as swe
WHERE supply="Microsoft-Home windows-TerminalServices-Gateway/Operational"
AND eventid IN (200,303)
AND swe.time > $$starttime$$
--AND swe.time > )$$starttime$$ AND swe.time < $$endtime$$
ORDER BY swe.time
Word the date/time-range info on the finish of the question. This ought to be adjusted to swimsuit the timeframe of the investigation. Within the Sophos Central GUI, this may be chosen utilizing the date variable sort; click on on the calendar to pick out the beginning and finish instances.
Reviewing IIS logs
By default, IIS writes its logs in UTC and makes use of the format ‘YYYY-MM-DD hh:mm:ss.’ Minutes and seconds have been deliberately unnoticed of the under grep sample, so we seize a full hour of logs surrounding the login occasions. Additionally, you will have to replace the ‘file.path’ worth to mirror the date of the IIS log you wish to evaluation. The format for that is simply YYMMDD (for instance, 240223 for February 23, 2024).
After getting run the earlier question and know the timestamp for the profitable logins from the RD Gateway occasion logs, you’ll be able to modify the question under to acquire the encompassing IIS logs. This gives you knowledge on the IIS login time, and on what the actor may need clicked on whereas related to the net portal. Because the supply IP handle is thought from the outcomes of the earlier question, that info will also be used as a ‘grep.sample’ filter to show all IIS logs containing that handle. That is an endpoint question, so you will have to pick out the precise host inside Sophos Central Reside Uncover.
SELECT grep.* FROM file CROSS JOIN grep ON (grep.path = file.path) WHERE file.path LIKE 'C:inetpubLogsLogFilesW3SVCpercentu_exYYMMDD.log' AND grep.sample = 'YYYY-MM-DD hh: '
Reviewing for indicators of brute drive exercise
Brute drive makes an attempt in the direction of an RD Internet portal will be seen by filtering login occasions to the Home windows IIS course of, w3wp.exe, as seen in Determine 5 (above, earlier part). It is a Sophos Central knowledge lake question; as with the question for reviewing RD Gateway logs (above), time-range choices for narrowing down the question will be set from the central GUI.
SELECT
meta_hostname, date_format(from_unixtime(CAST(event_timestamps AS bigint)), '%Y-%m-%d %H:%i:%S') AS event_timestamp, eventid, subject_username, subject_domain, target_username, target_domain, target_logon_id, subject_logon_id, logon_type, logon_process, authentication_package, transmitted_services, key_length, identify, remote_address, remote_port, description, provider_name, supply
FROM
xdr_data
WHERE
event_timestamps NOT LIKE '%,%'
AND
query_name IN ('windows_event_successful_logon','windows_event_invalid_logon')
AND identify LIKE '%w3wp.exe%'
AND meta_hostname="$$hostname$$"
Record RD Internet-published functions by way of the Home windows Registry
Evaluation the Home windows Registry to acquire an inventory of printed functions or session hosts, together with any permission restrictions that could be in place for these listed objects. That is an endpoint question, so that you’ll want to pick out the precise host inside Sophos Central Reside Uncover.
SELECT path, knowledge, sort, strftime('%Y-%m-%d %H:%M:%S',datetime(mtime,'unixepoch')) AS modified_time
FROM registry
WHERE path LIKE 'HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionTerminal Server%%'
Reviewing compromised account historical past throughout the property
As soon as a compromised account is recognized as logging in by the RD Internet portal, the next question can be utilized to analyze the consumer exercise. This lets you uncover if the risk actor has moved to different hosts throughout the community based mostly on the outcomes. It is a Sophos Central knowledge lake question. Word that you will want to offer the total username on the second-to-last line of the question.
SELECT meta_hostname, date_format(from_unixtime(time), '%Y-%m-%d %H:%i:%s') as date_time, username, cmdline, identify, path, sophos_pid, parent_name,parent_cmdline,parent_path, parent_sophos_pid, uid, gid,file_size, sha1, sha256 FROM xdr_ext_data WHERE query_name="running_processes_windows_sophos" AND username="$$username$$" ORDER BY date_time DESC
Gathering details about the compromised account
The next Sophos Central knowledge lake question can be utilized to get extra info on the compromised account.
SELECT meta_hostname,uid, gid, username, description, listing, shell, sort, uuid FROM xdr_data WHERE query_name="user_accounts" AND username = ‘$$username$$’
At the side of the above question, these PowerShell instructions can be utilized to look at a website or native consumer with a view to acquire extra consumer account properties like final password change, account enabled, and such. As with the earlier question, observe that you will want to offer the total username on the second-to-last line of the question.
MDR Response Actions
Incidents involving an uncovered RD Internet Entry host require immediate motion be taken to neutralize the risk earlier than any lateral motion takes place. As such, our MDR crew generally performs the next response actions to maneuver compromised techniques to a contained state as rapidly as doable.
- Isolate impacted hosts, together with the RD Gateway, to cease additional authentication makes an attempt in opposition to the uncovered login portal
- Word and block the supply IP handle that was used to illegitimately log into the portal
- Disable impacted area customers
- Block malicious executable hashes in Sophos Central
- Implement Software Management insurance policies inside Sophos Central to limit the execution of generally abused instruments
- Submit malicious and unknown recordsdata to SophosLabs to be categorised and have new detections created
Suggestions and Mitigation Methods
Whereas RD Internet Entry is beneficial as a method for customers to connect with enterprise assets from distant areas, there are some essential suggestions that ought to be applied to cut back the assault floor of the uncovered techniques. The next three actions, taken previous to an assault, might mitigate assault efficacy:
- Implement multi-factor authentication and guarantee it’s being enforced for all area customers
- Evaluation the configuration of the printed functions and RD Session hosts to make sure that solely anticipated and accepted objects have been printed, and to solely the customers which are anticipated to have entry to them. Take into account creating a gaggle coverage object to disclaim entry to cmd.exe and PowerShell for any customers that don’t require it.
- If doable, prohibit Web entry to the login portal to solely accepted supply IP addresses
If the above suggestions and mitigation methods can’t be applied and you need to proceed to make use of an RDS cluster, take into account defending the RD Internet Entry portal behind a VPN, with MFA enabled and enforced. This retains the portal from direct publicity to the web and thus reduces the assault floor of the uncovered software.
Conclusion
Evaluation of the present reputation of RD Internet Entry abuse, or which risk actor(s) is perhaps selecting this system, is past the scope of this text. We do nevertheless observe that unprotected internet-facing Distant Desktop entry is a known-bad alternative, as is the dearth of MFA on the techniques we noticed. Articles resembling this one should not an effort to disgrace the victims of assaults; moderately, we hope to offer perception into methods to examine such incursions, whereas encouraging readers to observe greatest safety practices and, maybe, keep away from ending up on this state of affairs.









