What’s DAST and what’s SAST?
To get the definitions out of the best way, dynamic utility safety testing (DAST) is a black-box testing methodology the place a working utility is examined from the skin. A DAST instrument crawls the appliance and probes it for runtime vulnerabilities identical to an attacker would. However, static utility safety testing (SAST) is a white-box safety testing methodology that inspects the appliance supply code to establish potential safety vulnerabilities.
So, in a nutshell, DAST checks a working internet utility whereas SAST checks its static code.
What’s IAST, then?
Interactive utility safety testing (IAST), typically known as gray-box testing, occupies the center floor between dynamic evaluation (white-box testing) and static evaluation (black-box testing). Relying on the seller, IAST generally is a standalone safety testing instrument that provides some dynamic testing functionality to SAST or a approach so as to add supply code insights to dynamic testing. For Invicti particularly, IAST is applied as a server-side agent that always communicates with the core vulnerability scanner to search out greater than DAST alone may (extra on that later).
SAST vs. DAST protection in internet utility safety testing
Protection is a basic attribute of safety testing, each inside a selected app and throughout your complete internet utility atmosphere. To precisely assess the safety of an utility, your safety testing answer must know what to check and the way to interpret the issues it finds in your utility.
SAST works on the appliance supply code, so you could have that code together with instruments that assist a selected programming language and internet utility framework. For a number of completely different expertise stacks, which will imply a number of SAST instruments. In a wider context, SAST protection is mostly restricted to apps which can be in energetic inside growth because you want each the code and the appropriate testing toolchains. So whilst you could hear opinions that solely SAST offers full check protection as a result of it checks all code, that is solely true for the codebase of a selected utility and the restricted subset of safety dangers that may be detected statically.
DAST instruments resembling vulnerability scanners, however, are technology-agnostic as a result of they check functions from the skin and look at their conduct, not their supply code. This permits DAST to cowl any variety of functions, no matter tech stack, growth standing, or supply code availability, testing the whole lot that’s externally accessible to a visiting browser. Main dynamic scanners can establish a variety of vulnerabilities, together with misconfigurations and different runtime points. In addition they assist trendy authentication schemes to entry web site sections and performance obtainable solely to authenticated customers.
Net API safety testing
Net utility programming interfaces (APIs) are the lifeblood of the cloud and gatekeepers of the info delivered by internet companies. Doing safety testing on API endpoints is now a crucial requirement to forestall knowledge breaches – and that’s primarily a job for DAST and handbook penetration testing.
Get the Invicti white paper on API safety testing to study why it is a essential a part of internet safety.
Safety testing accuracy and effectivity with SAST vs DAST
False positives are all the time a sizzling matter in utility safety testing, understood each as faulty outcomes and legitimate however non-actionable findings. SAST instruments, particularly, have a status for flooding builders with safety points that, whereas technically correct, are irrelevant in a selected context. This requires tedious fine-tuning to forestall builders from being flooded with false constructive reviews that devour their time for no safety profit and, in impact, are routinely ignored.
The large benefit of DAST is the potential to establish precise exploitable vulnerabilities relatively than merely signaling doubtlessly insecure code constructs. Whereas some early DAST instruments struggled to ship on that promise, industry-leading trendy DAST options depend on proof, not suspicions, and a few may even mechanically verify exploitability to flag high-priority points. This makes DAST the perfect method for time-strapped growth groups, permitting them to focus remediation on vulnerabilities that actually matter.
Discovering vulnerabilities with DAST and SAST
To offer a selected instance, let’s say an utility fetches knowledge from an SQL database based mostly on person enter from an online kind. A SAST instrument may establish the supply code fragment that does this and warn the developer that the SQL question in a selected line of code is assembled in an insecure approach and will doubtlessly result in an SQL injection (however won’t). A DAST instrument will discover the net kind on a web page and run safety checks to simulate precise SQL injection assaults. If any of the check assaults succeed, the scanner will report that the appliance has an SQL injection vulnerability on that particular web page:
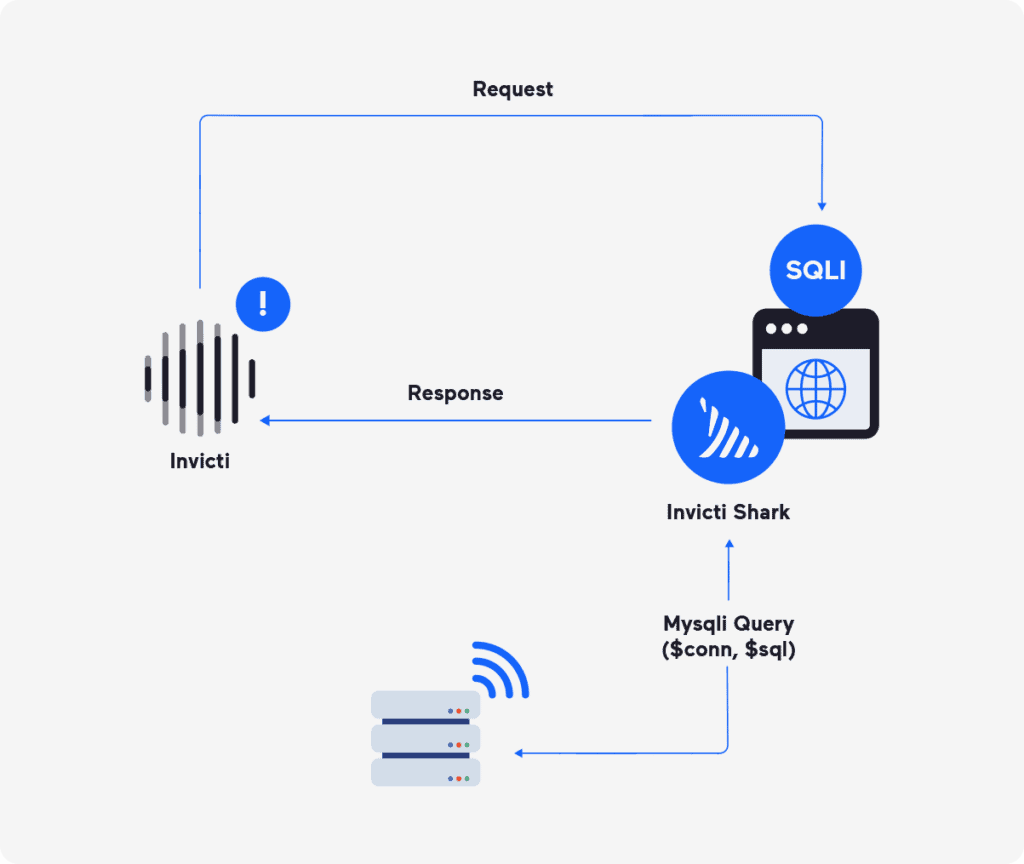
So the distinction between SAST and DAST outcomes is the distinction between “we should always most likely have a look at this” and “we have to repair this now” – particularly vital for weaknesses resembling cross-site scripting (XSS), the place many suspicious code constructs won’t ever result in an precise exploitable vulnerability.
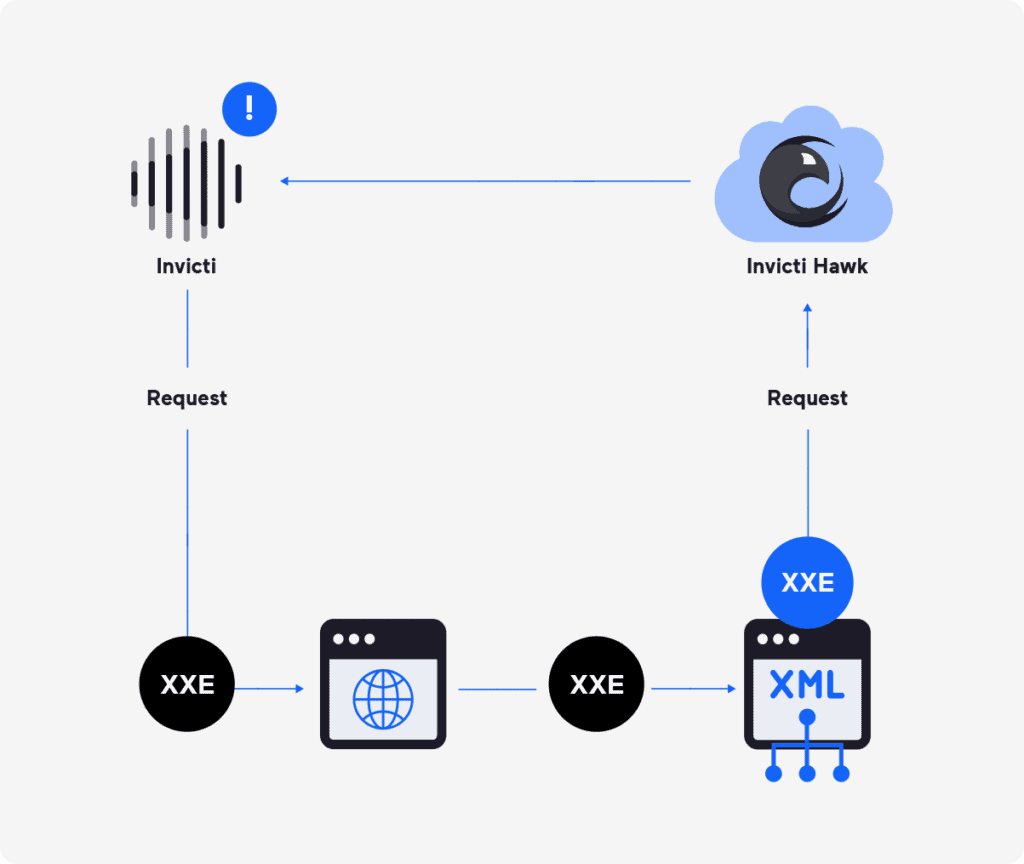
The standard of DAST instruments varies extensively, however any first rate DAST also needs to establish out-of-band vulnerabilities – safety weaknesses that don’t yield rapid reactions to safety checks. Invicti makes use of its integral Hawk part to pay attention for site visitors that indicators out-of-band and second-order vulnerabilities resembling XXE:
Constructing SAST and DAST into your SDLC
Safety testing from the early levels of your software program growth lifecycle (SDLC) is essential to search out and remediate vulnerabilities earlier than they make it into later phases and even into manufacturing. Supply code evaluation is essentially the most pure technique to discover and get rid of safety defects already throughout early growth. SAST is usually simple to combine with growth environments and workflows, whether or not as an IDE checker or standalone evaluation course of. Nonetheless, as a result of SAST can’t establish runtime vulnerabilities and misconfigurations, some type of dynamic testing remains to be wanted within the SDLC.
No matter some long-standing misconceptions, DAST instruments can also (and will) be built-in into the SDLC. Whereas it’s true that DAST can solely be achieved on a deployed utility, most trendy internet frameworks can autogenerate code for prototyping at any stage of growth to make this much less of a hindrance. The large benefit is that DAST can run at a number of levels of the SDLC, from partial testing in growth to full-scope checks in staging and even manufacturing testing by safety groups. As a result of DAST checks all the utility for weak behaviors and responses whatever the implementation particulars, it’s the really useful start line for including safety testing into the SDLC.
The Invicti approach: DevSecOps with DAST+IAST+SCA
With all of the acronyms in AppSec, it’s simple to get drawn into selecting one AST method over one other or (worse nonetheless) ticking bins to ensure you get all of the acronyms, ideally in a bundle. The final word purpose, although, isn’t to finish a purchasing listing however to discover a technique to get your internet functions safe and hold them safe. The way in which to get there’s completely different for every group and barely fast or simple. At Invicti, we’ve give you one fast-track method that builds on the really distinctive capabilities and have mixtures of our merchandise.
The Invicti answer is constructed across the {industry}’s most mature DAST platform and makes use of Proof-Primarily based Scanning to mechanically verify the overwhelming majority of exploitable high-impact vulnerabilities with no threat of false positives. These confirmed outcomes might be despatched on to builders by way of out-of-the-box integrations with subject trackers and CI/CD pipelines to ensure that utility safety can sustain with the in depth automation of DevOps growth processes. Every vulnerability report contains detailed remediation steering, and every repair might be mechanically retested, enabling organizations to arrange a hands-off AppSec course of that doesn’t intrude with growth and results in safer code in the long term.
The core DAST engine might be complemented by an IAST instrument with extra software program composition evaluation (SCA) capabilities. With an Invicti IAST agent put in on the internet or utility server, you may get extra detailed crawl and scan outcomes, extra vulnerability confirmations, and SCA checks to detect weak open supply dependencies. IAST brokers are at the moment obtainable for PHP, .NET, Java, and Node.js, with extra in growth.










