Often a tech story makes its approach out of our nerdy little bubble and into the large large world. Outages, bugs, and cybersecurity incidents occur within the tech business, however the harm often is not giant sufficient to warrant the sustained curiosity of most of the people at giant.
The CrowdStrike outage was totally different. Well being providers, flights, world banking operations, considerably affected. All-too-familiar blue screens of demise cropping up on billboards in Occasions Sq.. And 1,000,000 headlines, lots of which name-dropped Microsoft and borked Home windows PCs as the foundation explanation for the difficulty.
In fact, that is not fallacious, to a sure extent. It was certainly Microsoft Home windows machines that unceremoniously fell over en masse. Nevertheless, it was rapidly revealed that, whereas Microsoft definitely had its half to play, one other, lesser-known firm was the reason for the difficulty behind the difficulty: CrowdStrike.
Beforehand a reputation not notably well-known to the overall inhabitants (not less than, to not the identical extent as Microsoft), CrowdStrike, a Texas-based cybersecurity agency, discovered itself embroiled in a world catastrophe. Now the mud has settled, extra data has been revealed as to precisely what occurred and why.
And whereas we definitely have extra solutions, they immediate some troubling questions. What does this form of outage say concerning the stability of our ever-connected world? How might such a disastrous bug make its approach into so many methods directly? And what’s to stop occasions prefer it, maybe on a fair bigger scale, occurring sooner or later?
What occurred?
On Friday, July 19, at 9 minutes previous 4 within the morning, UTC, CrowdStrike pushed a content material configuration replace for a Home windows sensor on methods utilizing its Falcon cybersecurity platform. The replace itself appeared innocuous sufficient. CrowdStrike commonly tweaks its sensor configuration information, referred to by the corporate as “Channel Information”, as they’re a part of the safety mechanisms that may detect cybersecurity breaches.
This explicit replace was what the corporate refers to as a Speedy Response Content material replace. These updates are delivered as “Template Situations” that are themselves instantiations of a Template Kind. Template Situations map to particular behaviours for sensors to look at and detect, and are an important a part of Falcon’s cybersecurity safety capabilities.
Maintaining them up to date, at a velocity that retains up with ongoing cybersecurity developments, isn’t any simple activity, particularly with out error. Nonetheless, these updates usually undergo an in depth testing process. On the finish of that testing process is a Content material Validator, that performs validation checks on the content material earlier than publication.
This can be a traditional instance of the cascading affect a easy improve could cause to a number of enterprise sectors and on this case some vital infrastructure suppliers
Based on CrowdStrike, it was this Content material Validator that failed in its duties.
“As a consequence of a bug within the Content material Validator, one of many two Template Situations handed validation regardless of containing problematic content material information. Based mostly on the testing carried out earlier than the preliminary deployment of the Template Kind (on March 05, 2024), belief within the checks carried out within the Content material Validator, and former profitable IPC Template Occasion deployments, these situations had been deployed into manufacturing.”
For a extra detailed breakdown, CrowdStrike has since launched an exterior technical root trigger evaluation (PDF) of the precise causes. In the end, nevertheless, its testing system let by way of an misguided file, which was then pushed proper to the guts of many machines directly.
What occurred subsequent was disastrous. When the content material in Channel File 291 was obtained by the sensor on a Home windows machine, it precipitated an out-of-bounds reminiscence learn, which in flip triggered an exception. This exception precipitated a blue display of demise.
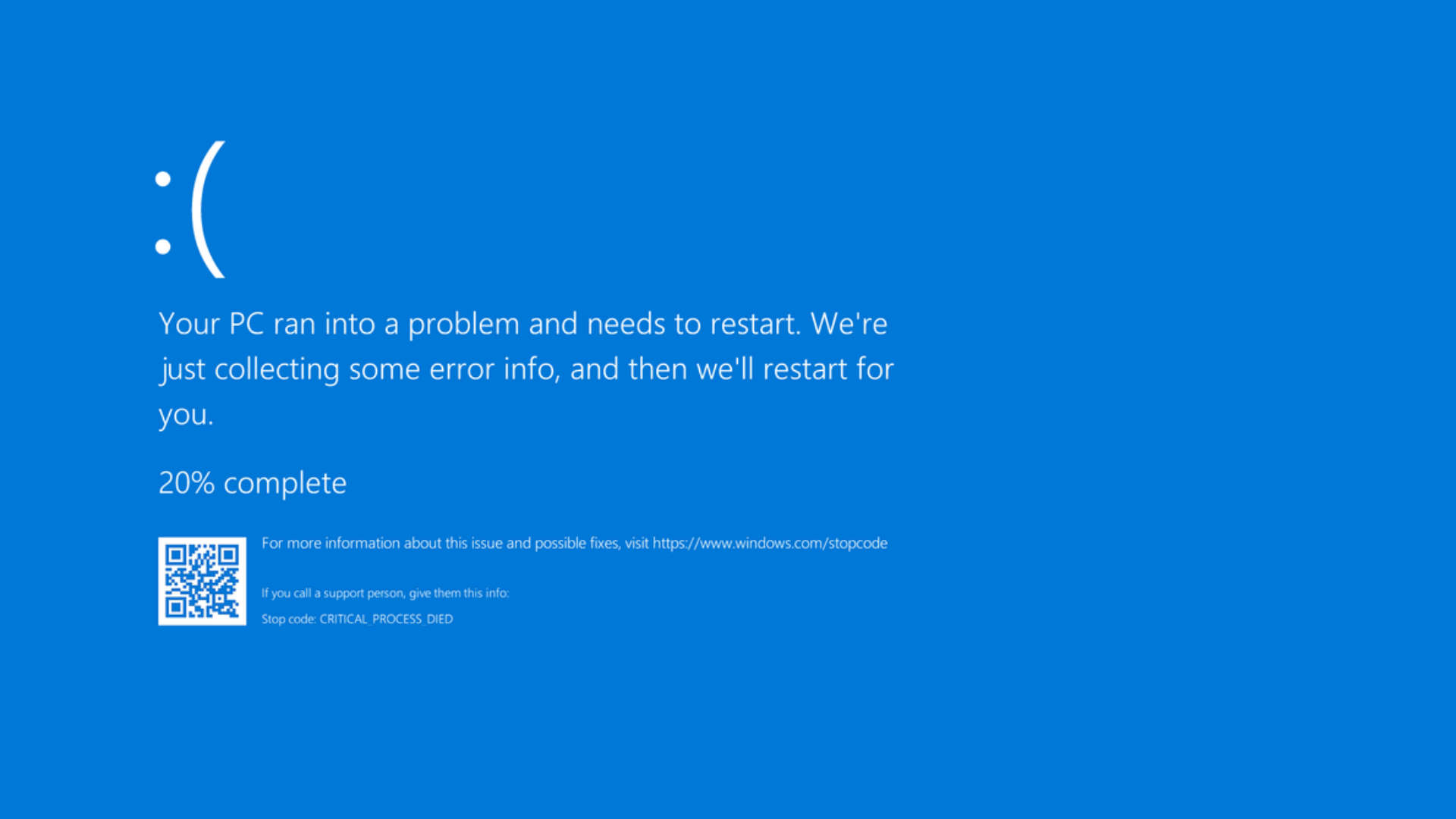
Worse nonetheless, these machines had been then caught in a boot loop, through which the machine crashes, restarts, after which crashes once more. For some this was a gentle irritation, and a foul day within the workplace. For others, nevertheless, the stakes had been a lot increased.
As Microsoft methods started crashing all over the world, some 911 dispatchers had been diminished to engaged on pen and paper. In Alaska, emergency calls went unanswered for hours, with comparable points affecting a number of emergency providers worldwide. Docs appointments and medical procedures had been cancelled, because the methods behind them failed. Some public transport methods floor to a halt. Flights, banks, and media providers went down with them.
Microsoft and CrowdStrike pulled the replace earlier than it might unfold any additional, with the latter releasing an replace file with out the error—however the harm was finished, and chaos was effectively underway.
For a time, fast repair options had been recommended. Microsoft’s Azure standing web page recommended that customers repeatedly reboot their affected machines, with the suggestion that a few of Microsoft’s prospects had rebooted their methods as much as 15 instances earlier than the system was in a position to seize a non-broken replace. Different alternate options included booting affected machines into Secure Mode and manually deleting the misguided replace file, or attaching known-working digital disks to restore VMs.
CrowdStrike’s CEO issued a public apology. IT staff dug in for the weekend, setting to work fixing boot-looping machines. Finally, Microsoft launched a restoration device, together with a press release estimating that 8.5 million Home windows units had been affected, and that it had deployed a whole bunch of engineers and consultants to revive affected providers.
By the point it was over, insurance coverage agency Parametrix estimated that, out of the highest 500 US corporations by income affected (excluding Microsoft), monetary losses had been round $5.4 billion, with solely an estimated $540 million to $1.08 billion of these losses being insured.
So what’s to stop such a catastrophe from occurring once more? Nicely, from CrowdStrike’s perspective, its testing procedures are below overview. The corporate has pledged to enhance its Speedy Response Content material testing, and add extra validation checks to “guard towards this sort of problematic content material from being deployed sooner or later”.
However there is a wider drawback right here, and it is partly to do with The Cloud.
A weak hyperlink within the chain
Within the huge, interconnected world we presently dwell in, it is develop into more and more impractical for big service suppliers, reminiscent of Microsoft, to deal with one thing as important as cybersecurity and cybersecurity updates throughout all of its networks in-house. This necessitates the necessity for third celebration suppliers, and people third celebration suppliers have to have the ability to replace their providers, deep throughout the system, en masse and at velocity, to maintain up with the most recent threats.
Nevertheless, that is primarily like handing somebody the keys to your own home to come back and test the locks when you’re away, and hoping they do not knock over your Ming vase within the course of. With the very best will on the planet, errors will likely be made, and with out overseeing issues your self (or in Microsoft’s case, itself), accountability is left to the third celebration to make sure that nothing is damaged within the course of.
Nevertheless, if that third celebration fails, it is you that in the end takes the blame. Or on this case, Microsoft, not less than when it comes to public notion. It might need been CrowdStrike’s identify within the headlines, however proper subsequent to it was Microsoft, together with photos of blue screens the world over—a picture tied so distinctively to the notion of Home windows instability that it is develop into consultant of the time period ‘system error’ in many individuals’s minds.
There have been lots of smug Linux people on the market crowing about how comfortable they had been to not be utilizing Microsoft’s ubiquitous OS, despite the fact that CrowdStrike had bricked a bunch of Linux-based methods only a month earlier. However due to the pervasiveness of the Home windows ecosystem, that failure did not have the widespread institutional harm or media consideration that the Microsoft-related error carried.
How we did this within the outdated days:After I was on Home windows, this was the kind of factor that greeted you each morning. Each. Single. Morning.You see, all of us had a secondary “debug” PC, and every evening we might run NTStress on all of them, and all of the lab machines. NTStress would… pic.twitter.com/rZkvpujbcrJuly 20, 2024
David W Plummer tweeted an attention-grabbing comparability of how issues work now in comparison with his days as a Microsoft engineer. Basically, whereas Home windows builds and drivers themselves nonetheless must move WHQL (Home windows {Hardware} High quality Labs testing), and the method is rigorous, a cloud-based system might want to obtain and execute code that hasn’t been examined by Microsoft particularly. If that code falls over, it might nonetheless probably take the system down with it.
Interconnectivity and the butterfly impact
After which there’s the issue of interconnectivity as an entire. Many important methods at the moment are so wholly depending on cloud suppliers and on-line updates that, regardless of staging and rigorous testing procedures, a small mistake can amplify itself rapidly. On this case, so rapidly that it was in a position to take down tens of millions of machines in a single fell swoop, and lots of of these machines had been essential for sustaining an unlimited community of others.
Not solely that, however in a world of accelerating cyberattacks and increasingly third celebration suppliers trying to defeat them, velocity is of the essence. Within the ongoing sport of cat and mouse between cybercrime and cybersecurity suppliers, those that snooze will inevitably lose. It is telling that, on the coronary heart of the difficulty right here, was a “Speedy Response” replace.
As Muttukrishnan Rajarajan, Professor of Safety Engineering and Director of the Institute for Cyber Safety at Metropolis College London, places it:
“As cyber threats are evolving at a fast part these corporations are additionally below lots of stress to improve their methods. Nevertheless, they’ve restricted assets to scale on the stage they should handle such upgrades rigorously as there are lots of interdependencies within the provide chain.
“This can be a traditional instance of the cascading affect a easy improve could cause to a number of enterprise sectors and on this case some vital infrastructure suppliers.”

Whereas this concern was attributable to CrowdStrike, and affected Microsoft machines, there’s nothing to say that this form of systemic failure could not have an effect on another giant cloud tech supplier. Particularly as Microsoft is much from the one firm counting on a small group of suppliers like CrowdStrike to complement its cybersecurity wants.
In a digital monoculture, single vulnerabilities throughout an interconnected set of methods can create a butterfly impact that ripples by way of infrastructure worldwide. Presently, 15 corporations worldwide are estimated to account for 62 p.c of the market in cybersecurity providers. That is lots of eggs in comparatively few baskets.
Whereas the CrowdStrike debacle is now over, and classes have been realized, the basic causes behind the difficulty are tough to repair. The cyber world is huge, inherently interconnected, and strikes at an ever rising tempo. Whereas extra rigorous testing, higher process, and extra strong launch processes might assist mitigate the difficulty, the basic course of behind it hinges on an interconnected system that can—by its very nature—require a mixture of velocity and deep system entry throughout huge numbers of machines to operate successfully as an entire. One weak hyperlink, one small replace gone awry, and the outcomes amplify at a tempo.
Right here, that potent mixture resulted in a damaged replace that unfold too rapidly, to too many methods—and chaos was the consequence. Transfer quick, break stuff, goes the adage. And on this case, an entire lot was damaged right here.