A lately found subtle cellular phishing method has been noticed in monetary fraud campaigns throughout the Czech Republic, Hungary and Georgia.
This phishing methodology leverages progressive net purposes (PWA), a majority of these net purposes provide a native-app-like expertise and are gaining momentum on each Android and iOS gadgets.
This system is noteworthy as a result of it installs a phishing software from a third-party web site with out the consumer having to permit third-party app set up, mentioned ESET, the cybersecurity agency which detected the campaigns.
Decoding PWA Phishing on iOS and Android
This new phishing method is just potential due to how PWAs work, bypassing the necessity for the consumer to permit third-party set up on their cellular.
On iOS, phishing web sites impersonating well-known purposes’ touchdown pages and instruct victims so as to add a PWA to their dwelling screens.
Earlier than the touchdown pages are arrange, the risk outlined the goal PWA as a standalone in a single file known as the manifest that guidelines how the PWA will behave. This leads to the PWA behaving like an everyday cellular app.
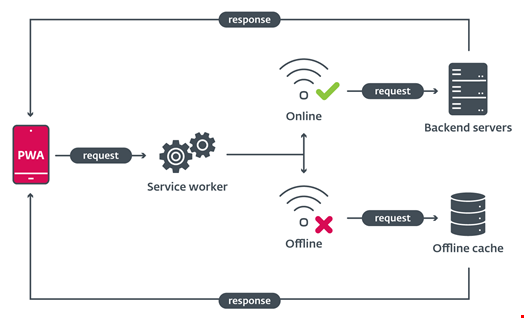
On Android gadgets, the PWA is put in after confirming customized pop-ups within the browser, which leads to the silent set up of an internet Android Package deal Equipment (WebAPK).
WebAPKs are a particular type of APK, the usual Android software file, that may be thought of an upgraded model of PWAs, because the Chrome browser generates a local Android software from a PWA.
ESET added that WebAPKs put in as a part of the detected phishing campaigns even gave the impression to be put in straight from the Google Play retailer.
This system was first disclosed by CSIRT KNF, a pc safety incident response group devoted to Poland’s monetary sector, in July 2023.
Monetary Fraud Campaigns Focused Banks in Czech Republic, Hungary and Georgia
In November 2023, ESET noticed cellular phishing campaigns concentrating on a number of Czech banks, the Hungarian OTP Financial institution and the Georgian TBC Financial institution, utilizing this similar method alongside normal phishing supply strategies.
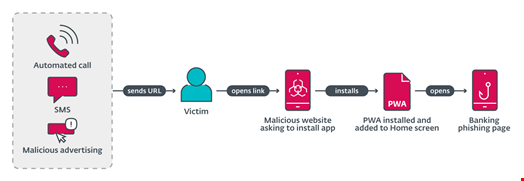
These phishing campaigns used three completely different URL supply mechanisms:
- Voice name supply: an automatic name warns the consumer about an out-of-date banking app and asks the consumer to pick out an possibility on the numerical keyboard. After urgent the proper button, a phishing URL is distributed by way of SMS
- SMS supply: textual content messages with a phishing hyperlink had been despatched indiscriminately to Czech telephone numbers
- Malvertising supply: advertisements together with a name to motion, like a restricted provide for customers who “obtain an replace beneath,” had been registered on Meta platforms like Instagram and Fb
All of the malicious hyperlinks led to phishing web sites, encouraging victims to put in a “new model” of the banking software.
“We found the primary phishing-via-PWA case in early November 2023 and observed the transition to WebAPKs in mid-November 2023,” the ESET researchers famous.
“Command and management (C2) servers that acquired info from phishing purposes had been first found in March 2024, with information in them confirming that they had been most likely not operational earlier.”
Based mostly on these C2 servers and backend infrastructure, the researchers concluded that two completely different risk actors had been working the campaigns.
ESET has notified the focused banks.
Learn extra: Prime Social Engineering Methods










