There are extra vulnerabilities round than ever. The Verizon Knowledge Breach Investigations Report highlighted an nearly 200% progress within the exploitation of vulnerabilities in 2023. Within the first seven months of 2024, new vulnerabilities rose by one other 30% in comparison with the earlier 12 months. No surprise vulnerability administration instruments have gotten a staple of the enterprise cybersecurity arsenal.
“Vulnerability administration is a core perform of cybersecurity,” stated Michelle Abraham, analysis director, Safety and Belief at IDC. “Leaving vulnerabilities with out motion exposes organizations to limitless danger since vulnerabilities might depart the information however not the minds of attackers.”
1
Semperis
Staff per Firm Measurement
Micro (0-49), Small (50-249), Medium (250-999), Massive (1,000-4,999), Enterprise (5,000+)
Enterprise (5,000+ Staff), Massive (1,000-4,999 Staff)
Enterprise, Massive
Options
Superior Assaults Detection, Superior Automation, Wherever Restoration, and extra
2
ESET PROTECT Superior
Staff per Firm Measurement
Micro (0-49), Small (50-249), Medium (250-999), Massive (1,000-4,999), Enterprise (5,000+)
Any Firm Measurement
Any Firm Measurement
Options
Superior Menace Protection, Full Disk Encryption , Trendy Endpoint Safety, and extra
3
NordLayer
Staff per Firm Measurement
Micro (0-49), Small (50-249), Medium (250-999), Massive (1,000-4,999), Enterprise (5,000+)
Medium (250-999 Staff), Enterprise (5,000+ Staff), Massive (1,000-4,999 Staff), Small (50-249 Staff)
Medium, Enterprise, Massive, Small
High vulnerability administration instruments comparability
Many vulnerability administration instruments have related options. However once I regarded into them extra carefully, I observed that they every have their very own focus or strategy. Some are extra specialised than others. I in contrast them based mostly on value in addition to 4 key options:
- Cloud, on-prem, or each.
- Being a part of a complete cybersecurity suite.
- Automated discovery.
- Automated remediation.
Bear in mind, nonetheless, that an apples-to-apples comparability based mostly on value is inconceivable because of the other ways distributors value their services in addition to a scarcity of transparency on pricing.
| Beginning value | Cloud or on-prem | Cybersecurity suite options | Automated discovery | Automated remediation | |
|---|---|---|---|---|---|
| Tenable | About $4,000 per 12 months for 100 property. | Cloud-based. There’s a separate on-prem suite referred to as Tenable Safety Heart that features vulnerability administration. | Vulnerability administration, net software scanning, cloud safety, id publicity, operational know-how safety, connect floor administration, and danger evaluation. | Sure | Sure |
| ESET | $275 for 5 gadgets per 12 months for the ESET Defend bundle that features ESET Vulnerability and Patch Administration | Cloud-based. A separate on-prem suite is out there that features vulnerability administration | EDR, server safety, cellular risk protection, encryption, risk protection, cloud safety, vulnerability & patch administration, MFA, and MDR | Some automated discovery however not as broad as among the others | Some auto-remediation capabilities are included |
| Syxsense | $9 per machine per thirty days or $960 per 12 months for 10 gadgets | One model for the cloud and one other for on prem | Patch administration, vulnerability scanning, IT administration, cellular machine administration, and 0 belief | Sure | Sure |
| CrowdStrike | $184 per 12 months for the total suite and about $40 per 12 months for Publicity Administration | Cloud-based | EDR, antivirus, risk looking/intelligence, publicity administration, AI, risk looking, cloud safety, SIEM, information safety, automation | Sure | Sure |
| Qualys | $295 per 12 months for the small enterprise model and about $2000 for the enterprise model. | Cloud-based with an on-prem model out there. | Asset administration, vulnerability & configuration administration, danger remediation, risk detection & response, EDR, cloud safety, and compliance. | Sure | Sure |
| Rapid7 | $6 per thirty days per asset or $2 per thirty days per asset for a 500-asset license. | Cloud and on-prem | AI engine, XDR, publicity administration, and assault floor administration. | Sure | Sure |
| Ivanti | $4 per thirty days per person. | Cloud or on-prem | Discovery, IT automation, real-time perception, endpoint administration, community and endpoint safety, provide chain, and repair and asset administration. | Sure | Sure |
| StorageGuard | $200 per thirty days for as much as 50 methods. | Cloud | No | Sure | Restricted |
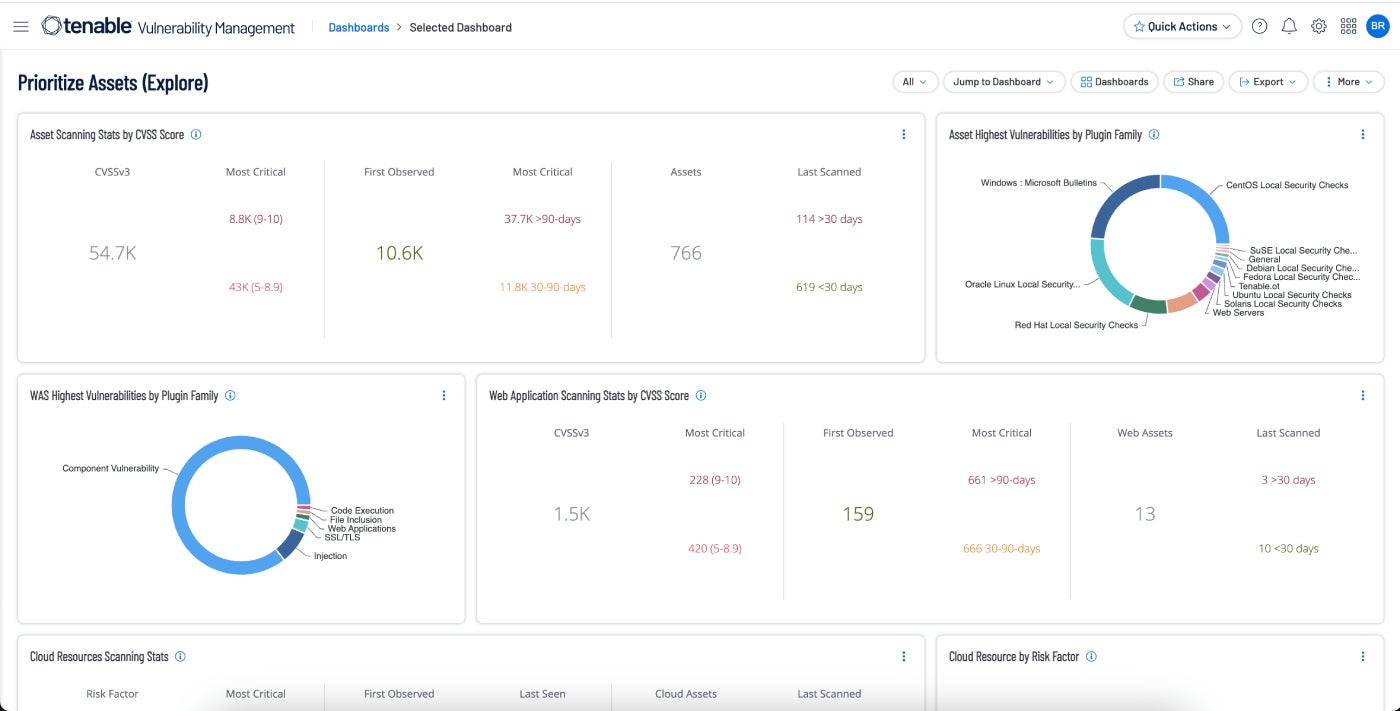
Tenable Vulnerability Administration: Finest general

Tenable Vulnerability Administration takes a risk-based strategy to vulnerability administration. It focuses on community visibility to be able to predict when assaults will happen and to have the ability to reply quickly when crucial vulnerabilities are in play. A 60-day free trial is out there.
SEE: Methods to Create an Efficient Cybersecurity Consciousness Program (TechRepublic Premium)
Why I selected Tenable
I chosen Tenable as the most effective general vulnerability administration software general for a lot of causes. It’s the market chief amongst vulnerability administration instruments with a 25% market share. It features a wealth of options and ticks nearly all of the bins. It accommodates a whole bunch of integrations with different platforms and safety instruments that make automation of workflows simple and cut back the variety of sources wanted to maintain the enterprise protected.
Pricing
- Tenable prices about $4,000 per 12 months for 100 property.
Options
- The Tenable Group is energetic with loads of customers keen to help you to deal with issues.
- Energetic and passive scanning of on-premise methods, digital machines, cloud situations, and cellular gadgets.
- Cloud Connectors give steady visibility and evaluation into public cloud environments like Microsoft Azure, Google Cloud Platform, and Amazon Internet Providers.
- Constructed-in prioritization, risk intelligence, and real-time reporting assist customers to grasp danger and proactively disrupt assault paths.
Execs and cons
| Execs | Cons |
|---|---|
| Absolutely built-in into the broader Tenable One platform. | Some customers report that assist could possibly be improved. |
| Steady, always-on discovery and evaluation | Actual-time scanning and general scanning velocity could possibly be improved. |
| Menace intelligence | Not the most cost effective resolution in the marketplace. |
| Automated vulnerability prioritization. | Higher suited to skilled IT professionals |
| Actual-time visualization of danger, and monitoring of vulnerabilities, property, and remediations. | |
| Vulnerability danger scores to determine danger. |
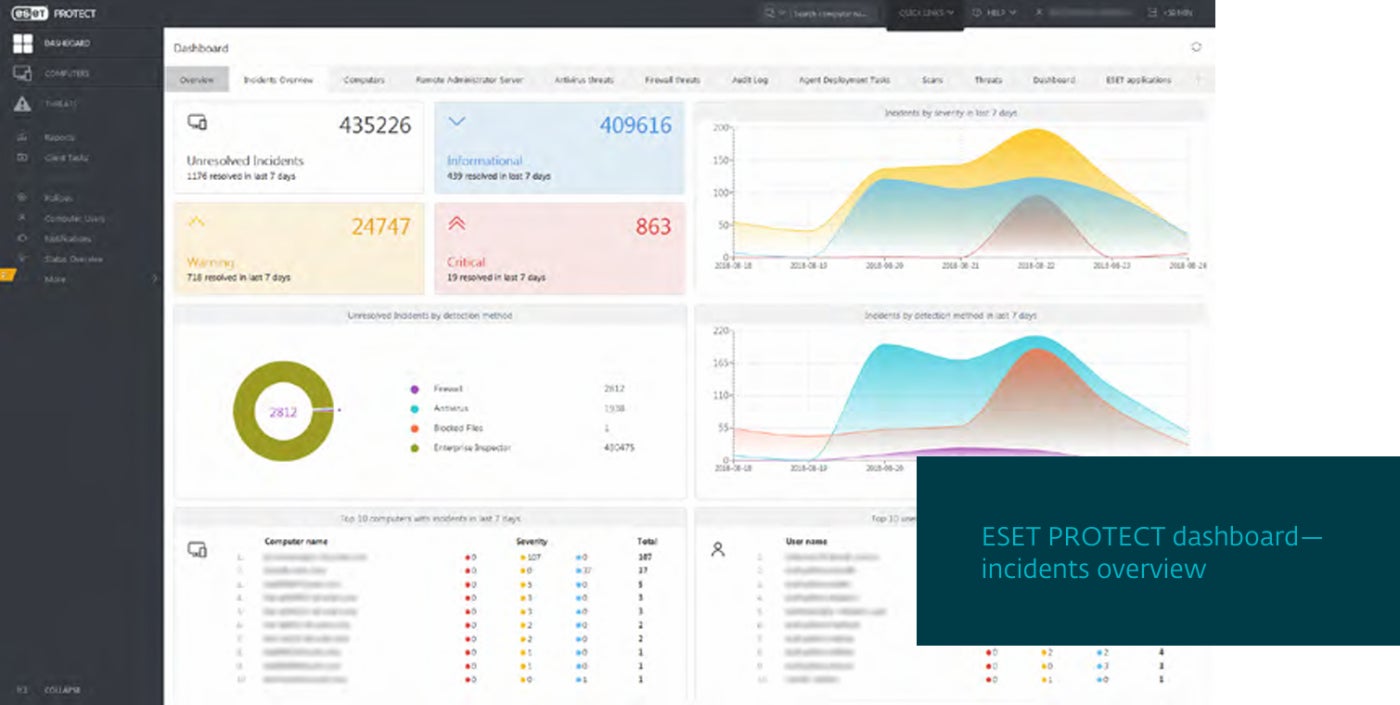
ESET Vulnerability and Patch Administration: Finest for SMEs

ESET Vulnerability and Patch Administration can routinely scan hundreds of purposes for any of tens of hundreds of widespread vulnerabilities and exposures. It may possibly prioritize and filter vulnerabilities by publicity rating and severity.
Why I selected ESET Vulnerability and Patch Administration
I appreciated ESET as it’s simple to put in and run. This makes it enticing for SMEs and bigger organizations that lack IT and cybersecurity sources.
Pricing
- $275 for 5 gadgets per 12 months for the ESET Defend bundle that features ESET Vulnerability and Patch Administration.
Options
- Helps a number of variations of Home windows, Linux, and macOS.
- Detects over 35,000 CVEs.
- Automated scans with customizable schedule settings.
- Prioritizes and filters vulnerabilities by publicity rating and severity.
Execs and cons
| Execs | Cons |
|---|---|
| Simplifies patching by prioritizing crucial property and scheduling the rest for off-peak occasions. | Automated discovery and remediation options lack the scope of another options. |
| Safety in opposition to ransomware and zero-day threats. | Extra targeted on small and mid-size organizations moderately than the enterprise market. |
| Simple to arrange, use, and keep. |
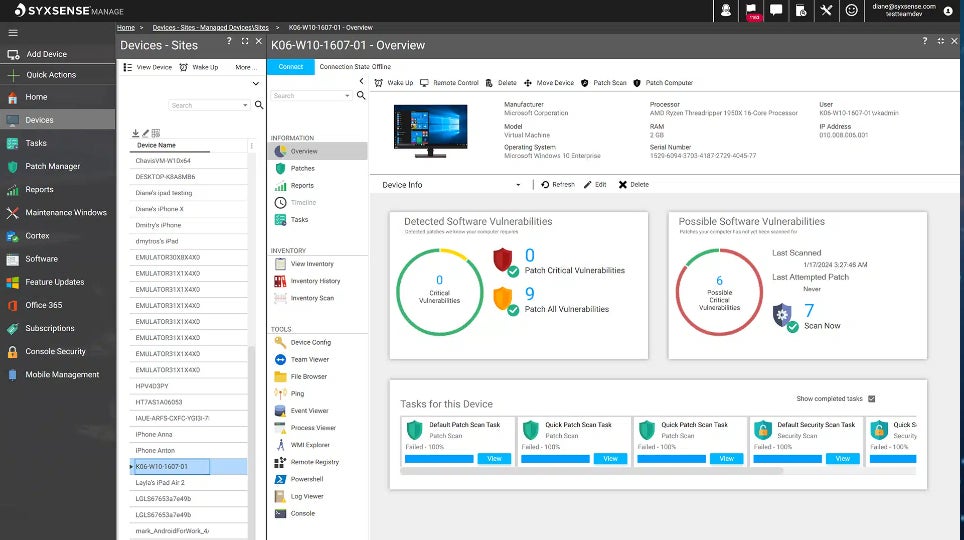
Syxsense Enterprise: Finest for patch administration

Syxsense Enterprise contains patch administration, vulnerability scanning, IT administration, and cellular machine administration inside its vulnerability administration platform. Most lately, it has added built-in remediation options in addition to zero belief. Every thing is now mixed into one console through Syxsense Enterprise.
Why I selected Syxsense
Syxsense started life as a patch administration specialist. Constructing on that success, it has steadily expanded right into a full featured vulnerability administration suite. Nonetheless, I observed that it doesn’t embody the breadth of safety modules that most of the different distributors on this information. It’s lacking SIEM, risk intelligence, and antivirus, for instance. Regardless of that, I appreciated the tight deal with vulnerability and machine administration. For people who have already got a safety platform and simply wish to enhance patch administration and vulnerability administration, Syxsense is an efficient alternative.
Pricing
- $9 per machine per thirty days or $960 per 12 months for 10 gadgets.
Options
- Automated discovery and remediation workflows.
- Complete patch administration together with patch supersedence, patch rollback, and patching any endpoint together with cellular gadgets.
- A Zero Belief Analysis Engine creates a trusted safety posture for endpoints.
Execs and cons
| Execs | Cons |
|---|---|
| Wonderful patch administration performance. | Syxsense was simply acquired by Absolute Safety, which might impede the excessive stage of steady innovation that propelled Syxsense to the forefront of the patch and vulnerability administration subject. |
| Tightly targeted on vulnerability administration. | Suite is lacking parts corresponding to antivirus, risk looking, and SIEM. |
| Separate variations for cloud and on-prem. |
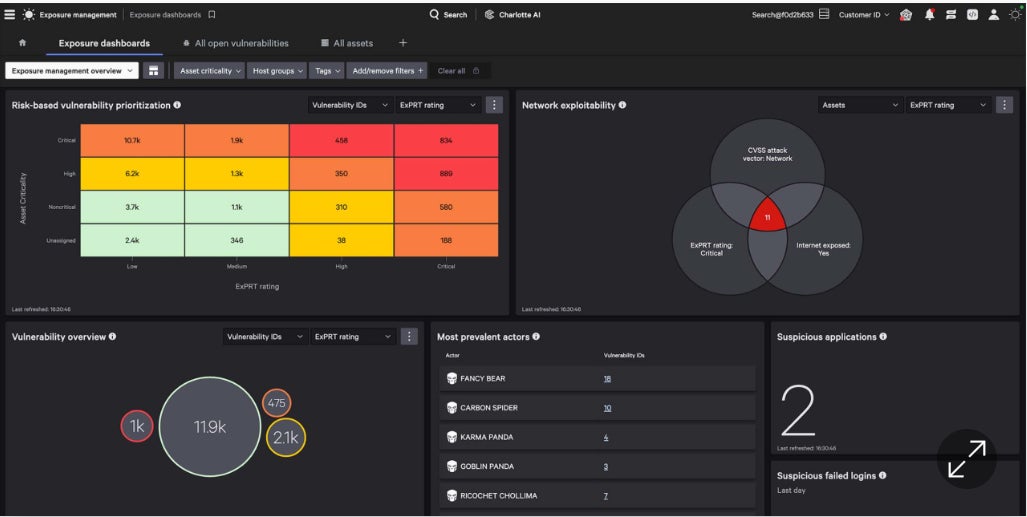
CrowdStrike Publicity Administration: Finest cybersecurity suite incorporating vulnerability administration

CrowdStrike Publicity Administration grew out of an older product often known as Falcon Highlight, which I used to be already accustomed to. I observed the way it broadens the capabilities of Falcon Highlight by including extra of a danger administration strategy together with a number of AI-based capabilities.
Why I selected CrowdStrike Publicity Administration
CrowdStrike Publicity Administration is a strong product in its personal proper. It’s one a part of a complete suite with a variety of safety features. Most patrons will buy the whole CrowdStrike platform moderately than solely the Publicity Administration component. Often called the CrowdStrike Falcon Platform, it encompasses EDR, antivirus, risk looking/intelligence, publicity administration, AI, risk looking, cloud safety, SIEM, information safety, automation, and extra, all from a single agent. Anybody needing a vulnerability administration software and a brand new safety suite can’t go far fallacious adopting all the Falcon Platform.
Pricing
- $184 per 12 months for the total suite and about $40 per 12 months for the publicity administration module.
Options
- Automated evaluation for vulnerabilities, whether or not on or off the community.
- Shortened time-to-respond with real-time visibility into vulnerabilities and threats.
- The flexibility to prioritize and predict which vulnerabilities are almost definitely to have an effect on the group.
- The corporate boasts a single lightweight-agent structure.
Execs and cons
| Execs | Cons |
|---|---|
| Vulnerability and patching orchestration. | Restricted capabilities in relation to scanning for misconfigurations in safety purposes. |
| Integration inside the CrowdStrike Falcon. | Extra deal with all the suite than on vulnerability administration. |
| AI ties collectively risk intelligence with vulnerability evaluation in actual time. | |
| A single agent for all modules. |
Qualys VMDR: Finest for cloud-based enterprises

Qualys Vulnerability Administration Detection and Response takes the context of threats under consideration as a technique to prioritize and remediate critical threats quickly. I appreciated the worth of its automated scoring methodology, often known as TruRisk.
Why I selected Qualys VMDR
Qualys VMDR does a great job bringing collectively a set of key safety features, together with vulnerability evaluation, asset discovery, stock administration, and assault floor administration. It’s half of a giant, cloud-based suite of safety merchandise. As such, I think about it to be a good selection for enterprises and bigger companies working within the cloud.
Pricing
- Qualys pricing appeared fairly complicated to me. It’s based mostly on the quantity or compute items within the cloud: digital machines, serverless, and container photographs. The unit worth varies based mostly on variations within the performance, complexity, and general worth proposition of every module. The enterprise model of all the suite begins at about $500 per thirty days and ramps up from there based mostly on the variety of customers. The vulnerability administration module is claimed to be out there to small companies beginning at $250 per 12 months and $2000 for enterprises.
Options
- Primarily cloud-based however an on-prem personal cloud equipment is out there for purchasers with strict information sovereignty necessities.
- A cloud-based service provided primarily to SMEs gives VMDR together with endpoint detection and response and patch administration instruments.
- Threat-based and context-based prioritization of threats
- Integration with patch administration, stock administration, and ITSM.
- Qualys Menace Analysis Unit proactively searches for brand new threats by analyzing information from its person base, dozens of risk intelligence feeds, third-party information, and the darkish net.
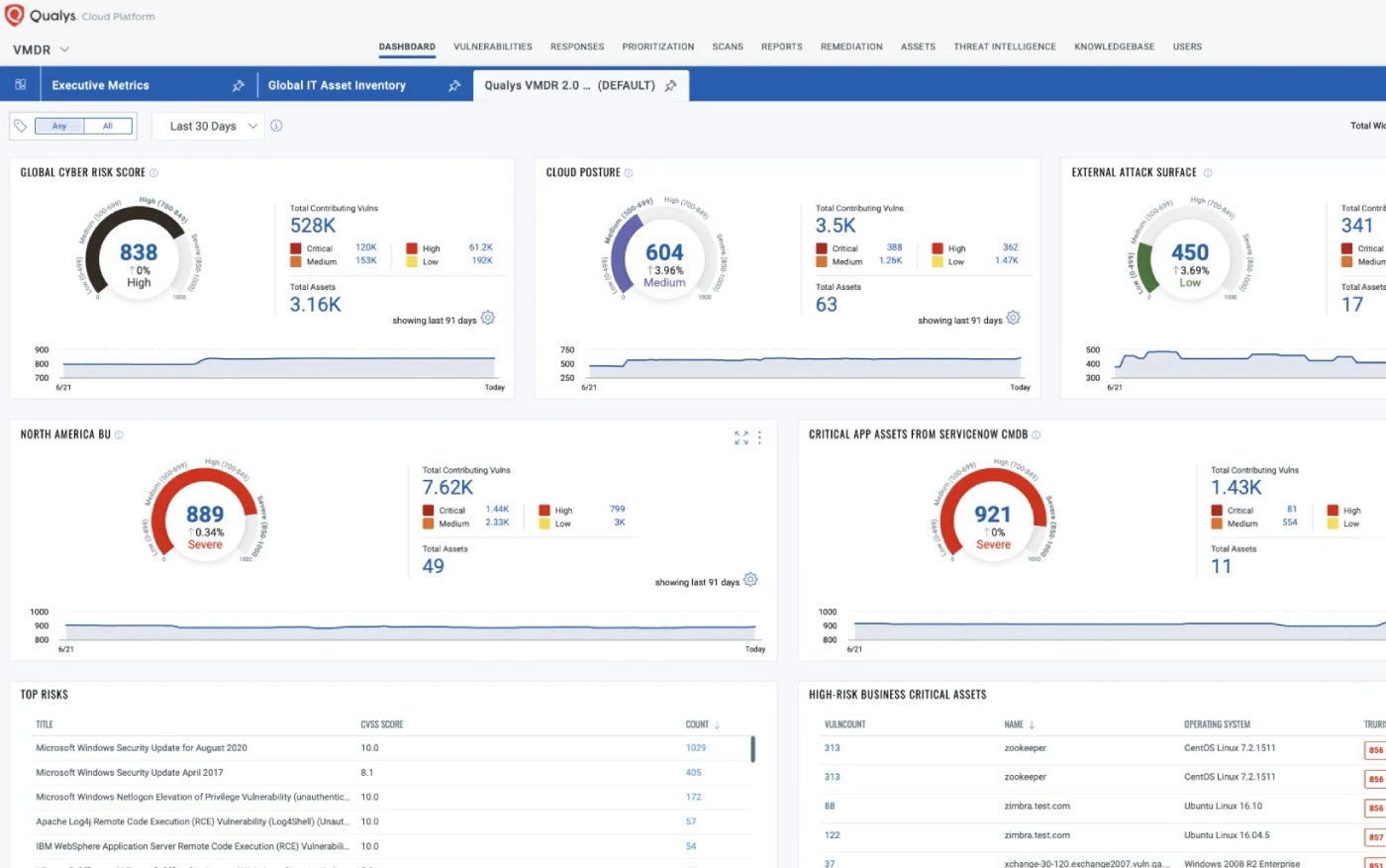
Execs and cons
| Execs | Cons |
|---|---|
| Broad vary of vulnerability signature databases. | Might be difficult to put in, be taught, and use for much less mature IT outlets. |
| Actual-time detection of vulnerabilities corresponding to patches that must be put in and misconfigurations. | Cloud and hypervisor assist could possibly be improved. |
| Robotically detects the newest superseding patch for the susceptible asset and deploys it. | |
| Qualys is without doubt one of the market leaders in vulnerability administration based mostly on market share. |
Options
- Regularly assesses and prioritizes crucial vulnerabilities utilizing danger scoring from 1 to 1000.
- Tracks compliance in opposition to coverage and rules, and compares to business benchmarks.
- Rapid7 Labs helps determine all internet-facing property and alert on vulnerabilities.
- Good scanning consistency and vary of gadgets.
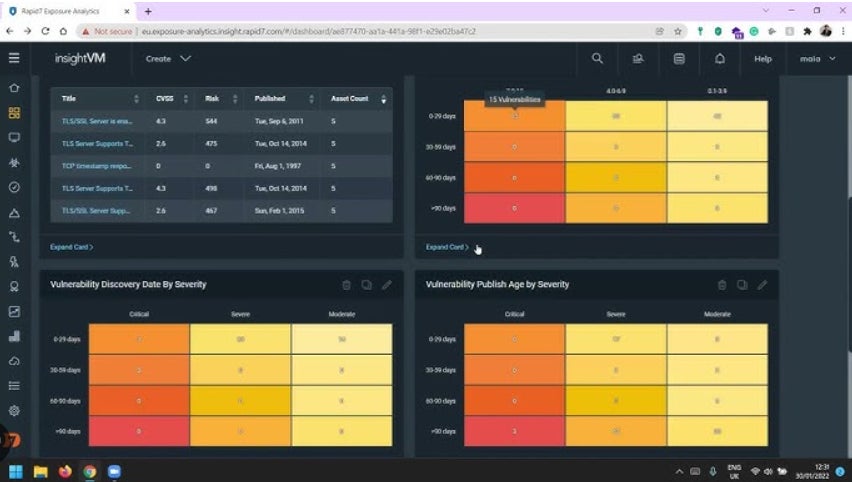
Execs and cons
| Execs | Cons |
|---|---|
| Automated remediation. | Finest suited to educated safety groups. |
| Automated pen-testing. | Can generally be difficult to arrange. |
| One of many prime vulnerability administration distributors per market share. | Some customers be aware integration and deployment points |
| Runs vulnerability scans throughout cloud, bodily, and digital infrastructure and routinely collects information from all endpoints. | Help responsiveness could possibly be improved. |
| Safety groups can streamline remediation actions corresponding to vulnerability patching and containment. | |
| Integrates with a spread of third-party instruments together with ticketing methods, patch administration options, and SIEM. |
Ivanti VMaaS: Finest as a service providing

Ivanti has an extended historical past as a prime vulnerability administration vendor. It gives instruments you may deploy inside the enterprise or as a service.
Why I selected Ivanti VMaaS
For me, Ivanti VMaaS stands out on account of its pairing of vulnerability administration as-a-service with knowledgeable safety analysts, scanning instruments, and processes that assist companies determine vulnerabilities on the community and in purposes. However the firm additionally gives prime cloud-based instruments corresponding to Ivanti Neurons for risk-based vulnerability administration.
Pricing
Options
- Ivanti Neurons for RBVM, can ingest information from a number of third-party scanners to assist shut gaps and blind spots.
- It routinely analyzes information from vulnerability scanners and gives perception to IT and safety groups.
- Scan findings are routinely correlated and contextualized with risk information and evaluation, and prioritized.
- Finds code weak spot and pinpoints coding errors.
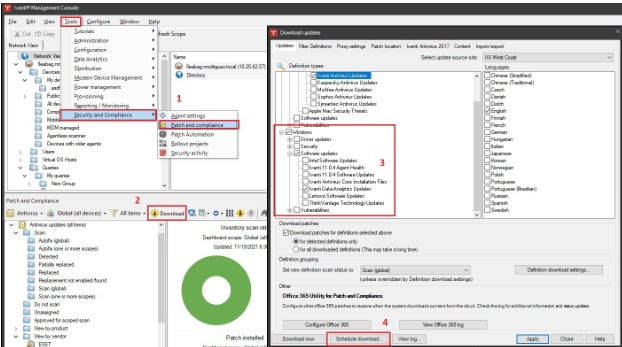
Execs and cons
| Execs | Cons |
|---|---|
| This absolutely managed service frees up personnel for different initiatives. | Some customers complain of lack of assist. |
| Simple-to-follow remediation plans. | Customization choices are restricted. |
| Threat scoring ensures remediation suggestions are targeted on actions that concentrate on probably the most critical threats. | Aggressive patch administration merchandise could also be extra complete at discovering all endpoints working on the community. |
| Automated workflows. |
StorageGuard: Finest for storage and backup purposes

StorageGuard by Continuity Software program scans, detects, and fixes safety misconfigurations and vulnerabilities throughout a whole bunch of storage, backup, and information safety methods.
Why I selected StorageGuard
Most instruments on this information present broad protection — both throughout all the vulnerability administration panorama or are a part of massive safety suites that go far past vulnerability administration. I picked StorageGuard because it takes the alternative strategy. It’s laser-focused on one facet of this market: a complete tackle to a significant hole discovered in lots of vulnerability administration merchandise — storage and backup vulnerabilities and misconfigurations. StorageGuard fills that area of interest so effectively that I like to recommend its use along with among the different instruments listed right here.
Pricing
- $200 per thirty days for as much as 50 methods.
Options
- Straight addresses the vulnerabilities and potential threats listed by NIST in Safety Tips for Storage Infrastructure.
- Broad protection of storage and backup apps and methods from the likes of Dell, NetApp, Hitachi Vantara, Pure, Rubrik, Commvault, Veritas, HPE, Brocade, Cisco, Veeam, Cohesity, IBM, Infinidat, VMware, AWS, and Azure.
- Can detect deviation from a selected configuration baseline.
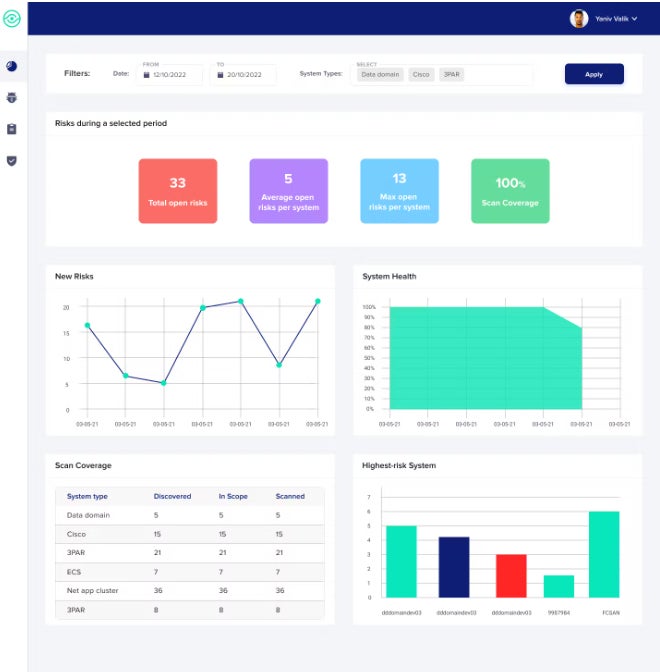
Execs and cons
| Execs | Cons |
|---|---|
| Scans and finds weaknesses in storage and backup purposes that different scanners miss. | Doesn’t tackle conventional vulnerabilities in third social gathering purposes and OSes. |
| Customers touch upon ease of use and thoroughness find backup and storage misconfigurations. | Targeted primarily on discovery of points versus decision. |
| Offers proof of audit compliance in opposition to CIS Controls, NIST, ISO, PCI, NERC CIP, and others. |
Vulnerability administration: Steadily requested questions
What are vulnerability administration instruments?
In response to NIST, vulnerability administration is a “functionality that identifies vulnerabilities [common vulnerabilities and exposures] on gadgets which can be doubtless for use by attackers to compromise a tool and use it as a platform from which to increase compromise to the community.”
In addition to mitigating configuration or code points which may enable an attacker to use an atmosphere, the definition is commonly broadened to incorporate patch administration, MDM, IT asset administration, and EDR. The vulnerability administration perform is commonly built-in into a big safety suite.
How do vulnerability administration instruments work?
Vulnerability administration might be damaged right into a sequence of steps, lots of which are actually automated:
- Vulnerability scanning.
- Reporting on any vulnerabilities found and prioritization based mostly on their potential influence on the enterprise.
- Deployment of remediation or advice of remediation steps.
- Validation of remediations to make sure points have been resolved.
- Reporting on the state of vulnerabilities and their decision inside the enterprise.
How are vulnerability administration instruments deployed?
They are often deployed as on-premises software program, delivered as SaaS, or as managed providers.
What’s vulnerability administration as a service?
Vulnerability administration as a managed service is delivered by a supplier through the cloud moderately than downloading and operating on-prem software program. It constantly identifies, assesses, experiences, and manages vulnerabilities throughout cloud identities, workloads, platform configurations, and infrastructure.
What options ought to I search for in a prime vulnerability administration software?
Sure core features are current in all prime vulnerability administration platforms. These embody:
- Discovery of all gadgets, purposes, and methods and detection of potential vulnerabilities and misconfigurations which will exist wherever inside the community on any machine that connects to the community.
- A database of vulnerabilities and threats that’s constantly up to date.
- Integration with a variety of platforms, safety methods, vulnerability scanners, ticketing methods, and different safety instruments.
- A way of danger scoring and prioritization.
- Automated remediation or remediation steerage.
- Reporting capabilities that spotlight points and compliance.
How do I select the most effective vulnerability administration software for my enterprise?
These in search of a vulnerability administration software ought to ask questions corresponding to:
- What platforms does the software function on? Bear in mind that some are targeted on Linux, some on Home windows, and a few cowl a number of or all OS and platforms. Additionally take into consideration what employees are already skilled on. Don’t add Linux instruments in case your inside personnel are skilled on Home windows, and vice-versa.
- What endpoints are coated? Some deal primarily with servers, PCs, and laptops, whereas others lengthen to smartphones, IoT, wi-fi, and different gadgets.
- Which components of the safety panorama are you trying so as to add or improve past vulnerability administration? In case you are within the midst of an entire overhaul of your complete safety infrastructure, begin with the suite after which discover one that features the vulnerability administration options you want. But when you have already got a strong safety spine, deal with vulnerability administration instruments that present the protection you want.
- Take note of the high quality print in contrasts and look carefully at price construction, the potential for extra charges, assist prices, and so on.
- Don’t be caught on one vendor for all safety wants. Vendor A may match for many of your safety infrastructure, however Vendor B could also be higher at vulnerability administration.
- What do analysts corresponding to Gartner say in regards to the totally different instruments, their market share, their execs and cons, and future route?
No matter software you select from the checklist above, the advantages of vulnerability administration shortly present up when it comes to fewer breaches, information that’s higher safeguarded, assaults being noticed far sooner than earlier than, and added automation.
Methodology
The instruments coated right here have been chosen based mostly on analyst experiences, peer opinions, and person satisfaction, in addition to opinions posted in TechRepublic and different Know-how Recommendation websites. I additionally supplied a mixture of full-fledged vulnerability administration merchandise, extremely specialised instruments, and people the place vulnerability administration is one module inside a a lot bigger suite.









