Three new mobile-only surveillance instruments developed and utilized by state-sponsored organizations have been found by cell safety supplier Lookout.
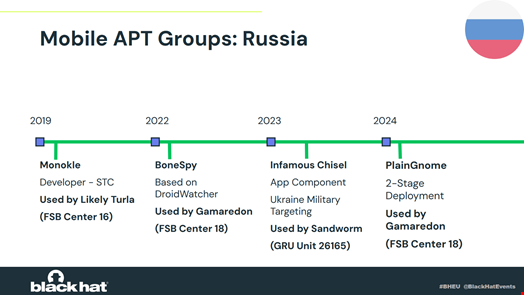
These new instruments embody BoneSpy and PlainGnome that are Android surveillance instruments developed by Gamaredon (aka Primitive Bear, Shuckworm), a complicated persistent menace (APT) group related to the Russian Federal Safety Service (FSB).
Moreover, a Chinese language software program growth firm has created EagleMsgSpy, a lawful surveillance device utilized by many authorities companies in mainland China to gather in depth info from cell units.
Kyle Schmittle and Alemdar Islamoglu, each Senior Safety Intelligence Researchers at Lookout, offered their findings at Black Hat Europe in London on December 11.
Russia’s BoneSpy and PlainGnome
Spyware and adware Overview
BoneSpy and PlainGnome are the primary identified cell households to be attributed to Gamaredon, an ATP group identified for its cyber espionage campaigns focusing on desktop units, that the Safety Service of Ukraine (SSU) attributed to the FSB in 2021.
BoneSpy has been in use since a minimum of 2021 and is derived from the Russian open-source DroidWatcher, a surveillance app developed between 2013 and 2014.
PlainGnome first appeared in 2024 however shares related theming and command-and-control (C2) server properties with BoneSpy.
Each households are nonetheless lively and primarily used to focus on Russian-speaking people in former Soviet international locations, resembling Uzbekistan, Kazakhstan, Tajikistan and Kyrgyzstan.
“Whereas Gamaredon has traditionally focused Ukraine, the focusing on of Central Asian international locations like Uzbekistan probably resulted from worsening relations between these international locations and Russia for the reason that begin of the Russian invasion of Ukraine in 2022,” the 2 researchers and their colleague Kristina Balaam wrote in a report revealed on December 11.
Spyware and adware Options
Each adware instruments have broad surveillance capabilities, together with:
- Trying to realize root entry to the machine
- Anti-analysis checks
- Location monitoring
- Getting details about the machine
- Getting delicate person knowledge resembling SMS messages, ambient audio and name recordings, notifications, browser historical past, contacts, name logs, photographs from the digicam, screenshots and cell service supplier info
PlainGnome acts as a dropper for a surveillance payload, saved throughout the dropper bundle, whereas BoneSpy is deployed as a standalone software.
Earlier than discovering BoneSpy and PlainGnome, Lookout’s Schmittle mentioned that his staff was solely conscious of two Russian-made adware households. First, Monokle, developed by St. Petersburg-based firm Particular Know-how Middle (STC) in 2019 and sure utilized by Turla. The opposite is Notorious Chisel, utilized by Sandworm in opposition to Ukraine navy entities since a minimum of 2023.
Learn extra on Turla: Palo Alto Reveals New Options in Russian APT Turla’s Kazuar Backdoor
China’s EagleMsgSpy
Spyware and adware Overview
EagleMsgSpy is a lawful surveillance device that has been working since a minimum of 2017 and is utilized by a number of Chinese language public safety bureaus to gather in depth info from cell units in Mainland China.
The Lookout researchers assessed that EagleMsgSpy is primarily used to focus on what is typically known as the ‘5 Poison’ communities:
- Practitioners of Falun Gong
- Uyghurs
- Tibetans
- Taiwanese folks
- Hong Kong pro-democracy advocates
Lookout additionally recognized two IP addresses related to EagleMsgSpy, which have beforehand been linked to different China-based surveillance instruments, together with CarbonSteal, identified for its position in previous campaigns focusing on the Tibetan and Uyghur communities.
Made in China, By the Personal Sector
Whereas the device’s origin stays unsure, the IP handle of one of many C2 servers encountered throughout Lookout’s investigation had beforehand been pointed to by a number of subdomains related to a personal Chinese language know-how firm, Wuhan Chinasoft Token Data Know-how Co., Ltd.
“The basis area, tzsafe[.]com, was encountered in promotional supplies discovered throughout an open supply intelligence (OSINT) investigation into this Wuhan-based know-how firm,” mentioned one other Lookout report revealed on December 11.
Moreover, the EagleMsgSpy admin person guide features a screenshot displaying places of what Lookout believes to be take a look at units that present two units of coordinates situated roughly 1.5 km from the registered official enterprise handle of Wuhan Chinasoft Token Data Know-how Co., Ltd.
This led Lookout to evaluate with “excessive confidence” that EagleMsgSpy has been developed by Wuhan Chinasoft Token Data Know-how.
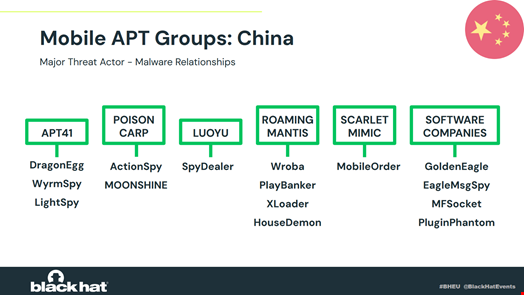
EagleMsgSpy has been recognized by Lookout as one in all a minimum of 4 totally different surveillance instruments utilized by the state, which have been made by the personal sector, with GoldenEagle, MFSocket and PluginPhantom.
Many different instruments originate from state-affiliated APT teams, resembling APT41, PoisonCarp, or Roaming Mantis.
Spyware and adware Options
The adware is positioned on victims’ Android units and configured by way of entry to the unlocked sufferer machine. As soon as put in, the headless payload runs within the background, hiding its actions from the machine person and amassing in depth knowledge.
The surveillance payload collects an intensive quantity of information concerning the sufferer machine together with, however not restricted to, screenshots, name logs, SMS messages and GPS coordinates.
Audio recordings of the machine whereas in use are additionally gathered.
It additionally collects all messages from QQ, Telegram, Viber, WhatsApp and WeChat.
After knowledge is collected, it’s saved in a staging space in a hidden listing of the machine’s file system for eventual exfiltration. The information information are then compressed and password-protected earlier than being despatched to the C2 server.
Whereas EagleMsgSpy solely targets Android units at current, inner paperwork retrieved from open directories on the attacker’s infrastructure recommend the presence of an undiscovered iOS part.

/cdn.vox-cdn.com/uploads/chorus_asset/file/25786875/Screenshot_2024_12_12_at_9.41.15_AM.png)








