Nationwide protection and safety specialists lengthy predicted that future warfare wouldn’t be waged by firearms however with code designed to disable companies individuals depend upon for every day life.
In Might 2021, safety specialists’ worst fears got here true, when a ransomware assault struck the Colonial Pipeline. Fuel supply to a lot of the US Northeast halted nearly in a single day. Though techniques have been ultimately restored, the occasion nonetheless lives in infamy at present and reminds us of the damaging potential cyberattacks can have when levied towards important infrastructure. Since then, related infrastructure assaults have dominated headlines throughout a lot of the world and are more and more carried out by non-state-sponsored actors.
In our “Q2/Q3 Ransomware Index Replace,” Securin (previously Cyber Safety Works) researchers mapped out the influence of ransomware on industrial management techniques (ICS) deployed in important infrastructure institutions. They recognized the three most at-risk sectors: healthcare, power, and manufacturing. Our researchers additionally examined 16 ransomware vulnerabilities and the unhealthy actors who exploit them, corresponding to Ryuk, Conti, WannaCry, and Petya. We’ve included a desk on the finish of the article with the total record of vulnerabilities and impacted distributors.
With every profitable assault, ransomware teams develop bolder and goal industries that may trigger probably the most ache to take advantage of the crises for max extortion. Understanding the menace actors and their strategies is the important thing to defending important industries and sustaining clean operations.
Healthcare
Cybersecurity and Infrastructure Safety Company (CISA) advisories to healthcare suppliers come within the aftermath of ongoing assaults by ransomware teams corresponding to Black Basta, Quantum, and MountLocker. The influence of unpatched important vulnerabilities on this sector could possibly be probably life threatening.
Public well being and healthcare techniques are affected by the vast majority of vulnerabilities — 9 out of the 16 recognized — as a result of they’re depending on different sectors for the continuity of their service supply and operations. Philips Healthcare, a technology-based firm that develops superior visualization software program for essential imaging tools, is probably the most affected vendor, clocking in eight vulnerabilities present in its IntelliSpace Portal 9.0. Vulnerabilities CVE-2017-0144 and CVE-2017-0147 must be patched instantly for his or her excessive ransomware household associations utilized in real-world assaults.
Vitality
An assault on an power supplier can lead to grid failure or inconsistent power output to properties, industrial buildings, or different important service suppliers. The power sector is suffering from six vulnerabilities that organizations should watch, significantly these present in Schneider Electrical’s merchandise.
CVE-2017-6032 and CVE-2017-6034 have an effect on Schneider Electrical’s Modicon Modbus Protocol, an open communications customary that’s used throughout important infrastructure, which might result in chain response assaults. Nonetheless, vulnerabilities CVE-2019-18935 and CVE-2020-10713 present in Hitachi ABB Energy Grid techniques and Hitachi Vitality Transformer Asset Efficiency Administration (APM) Edge, respectively, pose simply as a lot threat. They need to be handled as critical by community safety directors.
Manufacturing
The important manufacturing sector could be divided into 4 core subindustries: transportation tools; equipment manufacturing; electrical tools, equipment and part manufacturing; and first metals manufacturing.
1 / 4 of the vulnerabilities included in our evaluation have an effect on distributors within the manufacturing sector, together with Exacq Applied sciences, Sensormatic Electronics, and Schneider Electrical.
The way to Keep Protected
We encourage organizations to remain conscious of vendor advisories of the merchandise they make the most of and take steps to arrange vulnerability enumeration in response to severity. A lot of the vulnerabilities on this article reap the benefits of legacy setups comprising out-of-date software program and, typically, unsupported end-of-life parts. Listed below are key insights to maintain your system and trade secure:
- Improper enter validation is probably the most prevalent weak point powering ICS ransomware CVEs. Correct enter screening can stop unhealthy actors from infiltrating databases and locking admins out of the system.
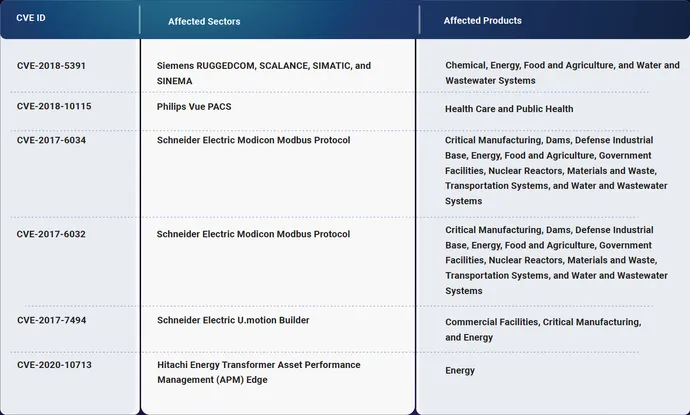
- Six vulnerabilities are lacking from the CISA Identified Exploited Vulnerability (KEV) catalog and must be patched: CVE-2018-5391, CVE-2018-10115, CVE-2017-6034, CVE-2017-6032, CVE-2017-7494, and CVE-2020-10713.
- Performing simulated penetration checks of your techniques can determine hidden entry factors that criminals would in any other case use. Discovering the place you might be most uncovered can assist set patch priorities and construct defenses earlier than attackers can leverage them.
The US financial system relies on an interconnected infrastructure of power, well being, and manufacturing. Hospitals want the power to operate and render life-saving companies, and oil and pure gasoline refineries ship essential gas to energy home manufacturing — it is a marvelous system to understand, however a relatively treasured one as properly, and we should always take steps to guard it.