A potential Chinese language assault marketing campaign on compromised unpatched SonicWall SMA edge gadgets stayed undetected since 2021 and will persist even via firmware updates.

As reported by a brand new Mandiant analysis doc, a brand new malware is manufactured from a number of bash scripts and a single Executable and Linkable Format (ELF) binary file recognized as a TinyShell backdoor variant. Tinyshell is a publicly obtainable instrument utilized by a number of risk actors (Determine A).
Determine A
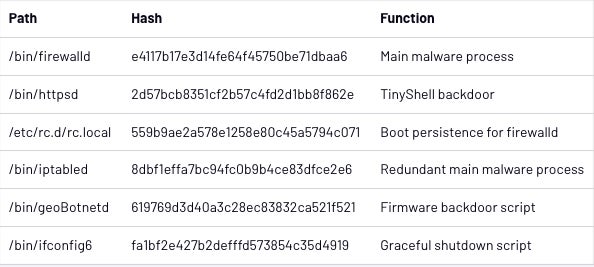
The primary malware course of is a file known as “firewalld,” which executes the TinyShell backdoor with parameters that permit it to supply a reverse shell to the risk actor. The reverse shell calls a C2 server at a time and day supplied by the script. If no IP tackle is supplied when calling the TinyShell binary, it embeds a hardcoded IP tackle to achieve.
A duplicate of the “firewalld” file known as “iptabled” was altered to make sure continuity of the first malware in case of a crash or termination. The 2 scripts had been set as much as activate each other in case the opposite wasn’tt already working, which created a backup occasion of the first malware course of and thereby enhanced its resilience.
The “firewalld” course of is launched at boot time by a startup script named “rc.native” supposed to facilitate an attacker’s extended entry.
A file named “ifconfig6” can be used to extend stability. The primary “firewalld” course of provides a small patch to a legit SonicWall binary named “firebased,” which replaces a shutdown string with a name to the “ipconfig6” script. Mandiant researchers suspect that attackers encountered points when the “firebased” script was shutting down the occasion and determined to create a small script to patch it.
As soon as the whole lot is ready, the ultimate objective of the malware is to routinely execute a SQL command to seize the hashed credentials of all logged in customers. The attacker may then retrieve these hashes to crack them offline.
Firmware updates modified
A bash script named “geoBotnetd” discovered on an contaminated machine checks each 10 seconds for a firmware improve to look in /cf/FIRMWARE/NEW/INITRD.GZ. If that’s the case, the script will backup the file, unzip it, mount it, after which copy over the entire bundle of malware information. It additionally provides a backdoored root consumer named “acme” to the system. The malware then rezips all of it and places it again in place.
This system, though not very refined, reveals how motivated the attackers are to maintain their entry long-term, as a result of a stable information of the firmware improve course of is critical to create and deploy such a way.
Mandiant researchers point out that this method is in line with one other assault marketing campaign they’ve analyzed that supported key Chinese language authorities priorities.
A protracted working marketing campaign for cyber espionage functions
Whereas the first vector of an infection stays unknown on this assault marketing campaign, Mandiant researchers point out that the malware or a predecessor of it was probably deployed in 2021 and that the risk actor most likely retained entry, even via a number of firmware updates.
As a result of the only real objective of the malware is to steal consumer credentials, it’s strongly suspected that the assault marketing campaign follows cyber espionage objectives.
Mandiant insists on the truth that growing malware for a managed equipment is not any trivial job, as distributors don’t typically supply direct entry to the working system and even to the filesystem of such gadgets. This makes it more durable to develop exploits and malware for these gadgets.
How you can shield from this risk
For this specific assault, SonicWall urges SMA100 clients to improve to model 10.2.1.7 or increased. The improve consists of hardening enhancements similar to File Integrity Monitoring (FIM) and anomalous course of identification.
On a bigger scale, defending edge gadgets from compromise requires a multi layered strategy that features each bodily and software program safety measures.
As well as, educate workers on cybersecurity finest practices, similar to figuring out phishing emails and avoiding suspicious web sites or downloads. Whereas the preliminary an infection vector isn’t recognized, it’s extremely potential that it might need been phishing emails.
Disclosure: I work for Pattern Micro, however the views expressed on this article are mine.

_678x452.jpg)




/cdn.vox-cdn.com/uploads/chorus_asset/file/24830575/canoo_van_photo.jpeg)



