It’s been seven years because the on-line dishonest web site AshleyMadison.com was hacked and extremely delicate knowledge about its customers posted on-line. The leak led to the general public shaming and extortion of many Ashley Madison customers, and to at the least two suicides. So far, little is publicly identified in regards to the perpetrators or the true motivation for the assault. However a latest evaluation of Ashley Madison mentions throughout Russian cybercrime boards and far-right web sites within the months main as much as the hack revealed some beforehand unreported particulars that will deserve additional scrutiny.

As first reported by KrebsOnSecurity on July 19, 2015, a gaggle calling itself the “Affect Crew” launched knowledge sampled from thousands and thousands of customers, in addition to maps of inside firm servers, worker community account info, firm financial institution particulars and wage info.
The Affect Crew mentioned it determined to publish the data as a result of ALM “earnings on the ache of others,” and in response to alleged lies that Ashley Madison father or mother agency Avid Life Media allegedly informed its clients a few service that permits members to fully erase their profile info for a $19 charge.
In line with the hackers, though the “full delete” function that Ashley Madison advertises promised “removing of web site utilization historical past and personally identifiable info from the positioning,” customers’ buy particulars — together with actual identify and tackle — aren’t truly scrubbed.
“Full Delete netted ALM $1.7mm in income in 2014. It’s additionally a whole lie,” the hacking group wrote. “Customers nearly at all times pay with bank card; their buy particulars aren’t eliminated as promised, and embrace actual identify and tackle, which is in fact crucial info the customers need eliminated.”
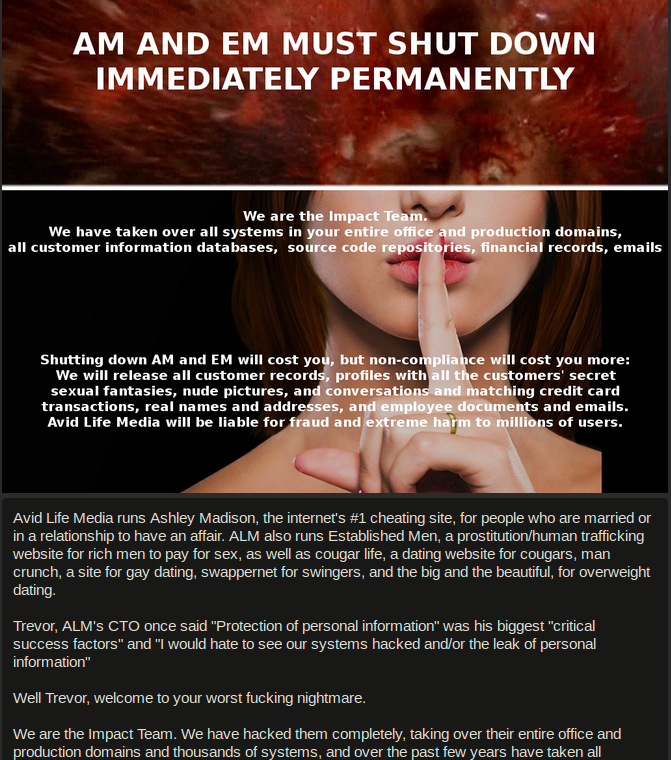
A snippet of the message left behind by the Affect Crew.
The Affect Crew mentioned ALM had one month to take Ashley Madison offline, together with a sister property referred to as Established Males. The hackers promised that if a month handed and the corporate didn’t capitulate, it could launch “all buyer data, together with profiles with all the purchasers’ secret sexual fantasies and matching bank card transactions, actual names and addresses, and worker paperwork and emails.”
Precisely 30 days later, on Aug. 18, 2015, the Affect Crew posted a “Time’s up!” message on-line, together with hyperlinks to 60 gigabytes of Ashley Madison person knowledge.
AN URGE TO DESTROY ALM
One side of the Ashley Madison breach that’s at all times bothered me is how the perpetrators largely solid themselves as preventing a crooked firm that broke their privateness guarantees, and the way this narrative was sustained at the least till the Affect Crew determined to leak the entire stolen person account knowledge in August 2015.
Granted, ALM had so much to reply for. For starters, after the breach it turned clear that an amazing lots of the feminine Ashley Madison profiles had been both bots or created as soon as and by no means used once more. Consultants combing by means of the leaked person knowledge decided that fewer than one p.c of the feminine profiles on Ashley Madison had been used frequently, and the remainder had been used simply as soon as — on the day they had been created. On high of that, researchers discovered 84 p.c of the profiles had been male.
However the Affect Crew needed to know that ALM would by no means adjust to their calls for to dismantle Ashley Madison and Established Males. In 2014, ALM reported revenues of $115 million. There was little probability the corporate was going to close down a few of its greatest cash machines.
Therefore, it seems the Affect Crew’s purpose all alongside was to create prodigious quantities of drama and stress by saying the hack of a significant dishonest web site, after which letting that drama play out over the subsequent few months as thousands and thousands of uncovered Ashley Madison customers freaked out and have become the targets of extortion assaults and public shaming.
Robert Graham, CEO of Errata Safety, penned a weblog put up in 2015 concluding that the ethical outrage professed by the Affect Crew was pure posturing.
“They look like motivated by the immorality of adultery, however most likely, their motivation is that #1 it’s enjoyable and #2 as a result of they’ll,” Graham wrote.
Per Thorsheim, a safety researcher in Norway, informed Wired on the time that he believed the Affect Crew was motivated by an urge to destroy ALM with as a lot aggression as they may muster.
“It’s not only for the enjoyable and ‘as a result of we will,’ neither is it simply what I might name ‘moralistic fundamentalism,’” Thorsheim informed Wired. “Provided that the corporate had been shifting towards an IPO proper earlier than the hack went public, the timing of the information leaks was possible no coincidence.”
NEO-NAZIS TARGET ASHLEY MADISON CEO
Because the seventh anniversary of the Ashley Madison hack rolled round, KrebsOnSecurity went again and appeared for any mentions of Ashley Madison or ALM on cybercrime boards within the months main as much as the Affect Crew’s preliminary announcement of the breach on July 19, 2015. There wasn’t a lot, besides a Russian man providing to promote cost and phone info on 32 million AshleyMadison customers, and a bunch of Nazis upset a few profitable Jewish CEO selling adultery.
Cyber intelligence agency Intel 471 recorded a collection of posts by a person with the deal with “Brutium” on the Russian-language cybercrime discussion board Antichat between 2014 and 2016. Brutium routinely marketed the sale of huge, hacked databases, and on Jan. 24, 2015, this person posted a thread providing to promote knowledge on 32 million Ashley Madison customers:
“Information from July 2015
Whole ~32 Million contacts:
full identify; e mail; cellphone numbers; cost, and so on.”
It’s unclear whether or not the postdated “July 2015” assertion was a typo, or if Brutium up to date that gross sales thread sooner or later. There’s additionally no indication whether or not anybody bought the data. Brutium’s profile has since been faraway from the Antichat discussion board.
Flashpoint is a menace intelligence firm in New York Metropolis that retains tabs on a whole bunch of cybercrime boards, in addition to extremist and hate web sites. A search in Flashpoint for mentions of Ashley Madison or ALM previous to July 19, 2015 exhibits that within the six months main as much as the hack, Ashley Madison and its then-CEO Noel Biderman turned a frequent topic of derision throughout a number of neo-Nazi web sites.
On Jan. 14, 2015, a member of the neo-Nazi discussion board Stormfront posted a vigorous thread about Ashley Madison within the common dialogue space titled, “Jewish owned courting web site selling adultery.”
On July 3, 2015, Andrew Anglin, the editor of the alt-right publication Every day Stormer, posted excerpts about Biderman from a narrative titled, “Jewish Hyper-Sexualization of Western Tradition,” which referred to Biderman because the “Jewish King of Infidelity.”
On July 10, a mocking montage of Biderman images with racist captions was posted to the extremist web site Vanguard Information Community, as a part of a thread referred to as “Jews normalize sexual perversion.”
“Biderman himself says he’s a fortunately married father of two and doesn’t cheat,” reads the story posted by Anglin on the Every day Stormer. “In an interview with the ‘Present Affair’ program in Australia, he admitted that if he came upon his personal spouse was accessing his cheater’s web site, ‘I might be devastated.’”
The leaked AshleyMadison knowledge included greater than three years’ price of emails stolen from Biderman. The hackers informed Motherboard in 2015 that they had 300 GB price of worker emails, however that they noticed no have to dump the inboxes of different firm workers.
A number of media retailers pounced on salacious exchanges in Biderman’s emails as proof he had carried on a number of affairs. Biderman resigned as CEO on Aug. 28, 2015. The final message within the archive of Biderman’s stolen emails was dated July 7, 2015 — nearly two weeks earlier than the Affect Crew would announce their hack.
Biderman informed KrebsOnSecurity on July 19, 2015 that the corporate believed the hacker was some sort of insider.
“We’re on the doorstep of [confirming] who we consider is the perpetrator, and sadly that will have triggered this mass publication,” Biderman mentioned. “I’ve received their profile proper in entrance of me, all their work credentials. It was undoubtedly an individual right here that was not an worker however actually had touched our technical providers.”
Sure language within the Affect Crew’s manifesto appeared to help this principle, resembling the road: “For an organization whose major promise is secrecy, it’s such as you didn’t even strive, such as you thought you had by no means pissed anybody off.”
However regardless of ALM providing a belated $500,000 reward for info resulting in the arrest and conviction of these accountable, to this present day nobody has been charged in reference to the hack.










