A 22-year-old man from the UK arrested this week in Spain is allegedly the ringleader of Scattered Spider, a cybercrime group suspected of hacking into Twilio, LastPass, DoorDash, Mailchimp, and almost 130 different organizations over the previous two years.
The Spanish each day Murcia In the present day reviews the suspect was needed by the FBI and arrested in Palma de Mallorca as he tried to board a flight to Italy.

A nonetheless body from a video launched by the Spanish nationwide police exhibits Tylerb in custody on the airport.
“He stands accused of hacking into company accounts and stealing important data, which allegedly enabled the group to entry multi-million-dollar funds,” Murcia In the present day wrote. “Based on Palma police, at one level he managed Bitcoins value $27 million.”
The cybercrime-focused Twitter/X account vx-underground stated the U.Okay. man arrested was a SIM-swapper who glided by the alias “Tyler.” In a SIM-swapping assault, crooks switch the goal’s cellphone quantity to a tool they management and intercept any textual content messages or cellphone calls despatched to the sufferer — together with one-time passcodes for authentication, or password reset hyperlinks despatched through SMS.
“He’s a identified SIM-swapper and is allegedly concerned with the notorious Scattered Spider group,” vx-underground wrote on June 15, referring to a prolific gang implicated in pricey information ransom assaults at MGM and Caesars casinos in Las Vegas final 12 months.
Sources acquainted with the investigation advised KrebsOnSecurity the accused is a 22-year-old from Dundee, Scotland named Tyler Buchanan, additionally allegedly often known as “tylerb” on Telegram chat channels centered round SIM-swapping.
In January 2024, U.S. authorities arrested one other alleged Scattered Spider member — 19-year-old Noah Michael City of Palm Coast, Fla. — and charged him with stealing at the very least $800,000 from 5 victims between August 2022 and March 2023. City allegedly glided by the nicknames “Sosa” and “King Bob,” and is believed to be a part of the identical crew that hacked Twilio and a slew of different firms in 2022.
Investigators say Scattered Spider members are a part of a extra diffuse cybercriminal neighborhood on-line often known as “The Com,” whereby hackers from completely different cliques boast loudly about high-profile cyber thefts that just about invariably start with social engineering — tricking individuals over the cellphone, e mail or SMS into gifting away credentials that enable distant entry to company inner networks.
One of many extra fashionable SIM-swapping channels on Telegram maintains a often up to date leaderboard of probably the most achieved SIM-swappers, listed by their supposed conquests in stealing cryptocurrency. That leaderboard at the moment lists Sosa as #24 (out of 100), and Tylerb at #65.
0KTAPUS
In August 2022, KrebsOnSecurity wrote about peering inside the information harvested in a months-long cybercrime marketing campaign by Scattered Spider involving numerous SMS-based phishing assaults in opposition to workers at main firms. The safety agency Group-IB referred to as the gang by a unique title — 0ktapus, a nod to how the prison group phished workers for credentials.
The missives requested customers to click on a hyperlink and log in at a phishing web page that mimicked their employer’s Okta authentication web page. Those that submitted credentials have been then prompted to offer the one-time password wanted for multi-factor authentication.
These phishing assaults used newly-registered domains that always included the title of the focused firm, and despatched textual content messages urging workers to click on on hyperlinks to those domains to view details about a pending change of their work schedule. The phishing websites additionally featured a hidden Telegram prompt message bot to ahead any submitted credentials in real-time, permitting the attackers to make use of the phished username, password and one-time code to log in as that worker at the true employer web site.
One in all Scattered Spider’s first large victims in its 2022 SMS phishing spree was Twilio, an organization that gives companies for making and receiving textual content messages and cellphone calls. The group then pivoted, utilizing their entry to Twilio to assault at the very least 163 of its prospects.
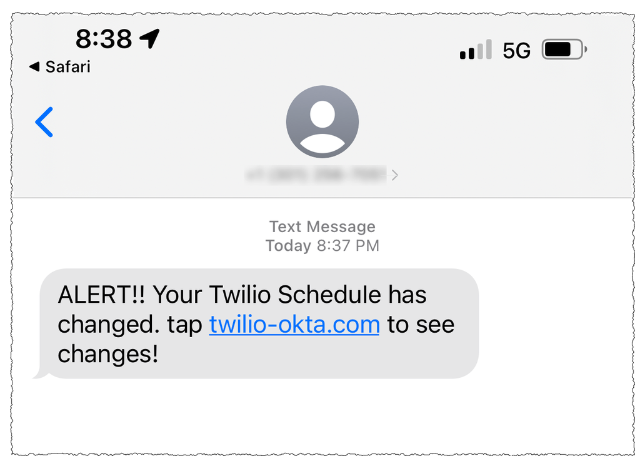
A Scattered Spider phishing lure despatched to Twilio workers.
Amongst these was the encrypted messaging app Sign, which stated the breach may have let attackers re-register the cellphone quantity on one other system for about 1,900 customers.
Additionally in August 2022, a number of workers at e mail supply agency Mailchimp supplied their distant entry credentials to this phishing group. Based on Mailchimp, the attackers used their entry to Mailchimp worker accounts to steal information from 214 prospects concerned in cryptocurrency and finance.
On August 25, 2022, the password supervisor service LastPass disclosed a breach during which attackers stole some supply code and proprietary LastPass technical data, and weeks later LastPass stated an investigation revealed no buyer information or password vaults have been accessed.
Nonetheless, on November 30, 2022 LastPass disclosed a much more critical breach that the corporate stated leveraged information stolen within the August breach. LastPass stated prison hackers had stolen encrypted copies of some password vaults, in addition to different private data.
In February 2023, LastPass disclosed that the intrusion concerned a extremely advanced, focused assault in opposition to an engineer who was considered one of solely 4 LastPass workers with entry to the company vault. In that incident, the attackers exploited a safety vulnerability in a Plex media server that the worker was working on his residence community, and succeeded in putting in malicious software program that stole passwords and different authentication credentials. The vulnerability exploited by the intruders was patched again in 2020, however the worker by no means up to date his Plex software program.
Plex introduced its personal information breach someday earlier than LastPass disclosed its preliminary August intrusion. On August 24, 2022, Plex’s safety staff urged customers to reset their passwords, saying an intruder had accessed buyer emails, usernames and encrypted passwords.
TURF WARS
Sosa and Tylerb have been each subjected to bodily assaults from rival SIM-swapping gangs. These communities have been identified to settle scores by turning to so-called “violence-as-a-service” choices on cybercrime channels, whereby individuals could be employed to carry out a spread geographically-specific “in actual life” jobs, comparable to bricking home windows, slashing automobile tires, and even residence invasions.
In 2022, a video surfaced on a preferred cybercrime channel purporting to point out attackers hurling a brick via a window at an deal with that matches the spacious and upscale residence of City’s mother and father in Sanford, Fl.
January’s story on Sosa famous {that a} junior member of his crew named “Foreshadow” was kidnapped, overwhelmed and held for ransom in September 2022. Foreshadow’s captors held weapons to his bloodied head whereas forcing him to document a video message pleading along with his crew to fork over a $200,000 ransom in alternate for his life (Foreshadow escaped additional hurt in that incident).
Based on a number of SIM-swapping channels on Telegram the place Tylerb was identified to frequent, rival SIM-swappers employed thugs to invade his residence in February 2023. These accounts state that the intruders assaulted Tylerb’s mom within the residence invasion, and that they threatened to burn him with a blowtorch if he didn’t hand over the keys to his cryptocurrency wallets. Tylerb was reputed to have fled the UK after that assault.
KrebsOnSecurity sought remark from Mr. Buchanan, and can replace this story within the occasion he responds.