
Akamai Applied sciences introduced this week that it’ll purchase privately funded software programming interface menace detection and response agency Neosec, a finalist within the 2022 RSA Convention Innovation Sandbox Contest. The deal is about to shut in June. Neosec’s workers, together with co-founder and chief govt officer, Giora Engel, and co-founder and CEO, Ziv Sivan, are additionally anticipated to hitch Akamai’s safety expertise enterprise.
The acquisition speaks to the wake-up name second: the rising significance of API threat detection and assault remediation as a part of always-on detection and response, and the ascendance of extra holistic safety platforms.
Within the latter circumstance, IT firms like Cisco, Examine Level and others are providing a holistic single platform different to a multiple-vendor method — one centered on myriad safety software-as-a-service options to particular vulnerabilities — quite like dozens of proverbial Hollanders plugging recognized leaks with their thumbs however not addressing the large image.
Rupesh Chokshi, normal supervisor of software safety at Akamai, defined that the acquisition brings much-needed experience in API to Akamai.
SEE: Coordinated cybersecurity is safety aligned with enterprise objectives (TechRepublic)
“There are a variety of issues we’ve got grow to be actually good at, however we haven’t centered on API interactions. With this new functionality we’re in a position to see anomalies: Why are these calls being made? What’s the knowledge shared or traversed, what recognized vulnerabilities are we seeing? We are going to now have the flexibility to rapidly alert the shopper that that is what’s occurring,” Chokshi mentioned.
Mani Sundaram, govt vice chairman and normal supervisor of the safety tech group at Akamai mentioned, “Enterprises expose full enterprise logic and course of knowledge through APIs, which, in a cloud-based financial system, are susceptible to cyberattacks. Neosec’s platform and Akamai’s software safety portfolio will permit clients to achieve visibility into all APIs, analyze their conduct and shield in opposition to API assaults.”
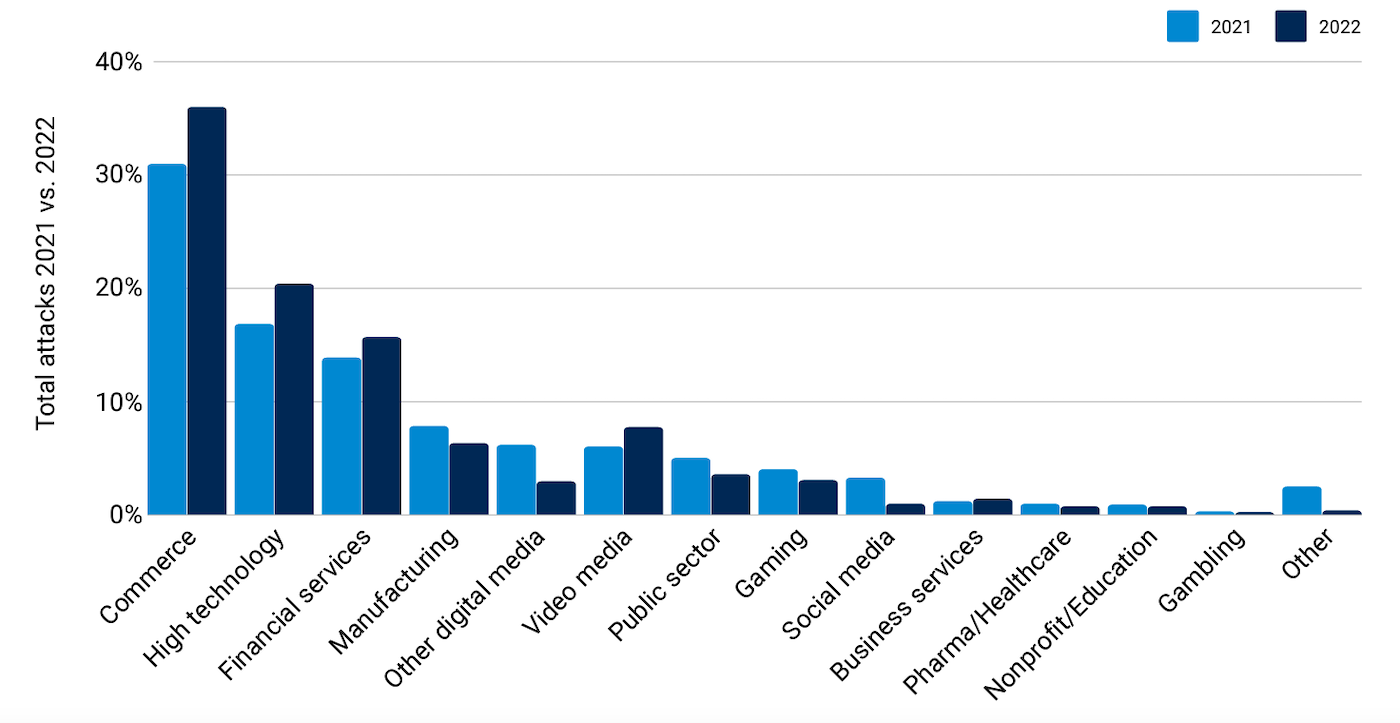
API assaults on the rise
Safety companies are seeing a brisk improve in API menace exercise. Salt Safety, in its March State of API Safety report famous a 400% improve in attackers over the prior six months. The report additionally discovered:
- 80% of assaults occurred over authenticated APIs.
- Almost half of respondents now state that API safety has grow to be a C-level concern.
- 94% of survey respondents skilled safety issues in manufacturing APIs prior to now yr.
- 70% mentioned their organizations suffered a knowledge breach because of safety gaps in APIs.
One instance illustrates how efficient a comparatively easy API assault might be: the NCC Group, in its 2022 annual Risk Monitor, famous that Australian telecom Optus had the non-public data of 10 million clients uncovered in a knowledge breach accessed by an uncovered API.
Roey Eliyahu, co-founder and CEO, Salt Safety famous that whereas APIs are powering digital transformation delivering new enterprise alternatives and aggressive benefits, “The price of API breaches, reminiscent of these skilled lately at T-Cell, Toyota and Optus, put each new providers and model repute, along with enterprise operations, in danger.”
Akamai’s State of the Web report famous the inclusion of API vulnerabilities within the upcoming Open Net Utility Safety Challenge API Safety High 10 launch is emblematic of rising business consciousness of API safety dangers.
Danger grows with elevated velocity of software program improvement
The Akamai report cites two elements driving the rise in API assault quantity. One is acceleration within the software improvement lifecycle, which “requires a sooner turnaround in creating and deploying these purposes in manufacturing, which might lead to a scarcity of safe code,” mentioned the report.
Akamai cited Veracode’s Enterprise Technique Group survey, during which 48% of organizations said that they launch susceptible purposes into manufacturing due to time constraints (Determine A).
Determine A
Akamai additionally reported the variety of vulnerabilities is on the rise, with one-tenth of all vulnerabilities within the excessive or important class present in internet-facing purposes. The report additionally mentioned open supply vulnerabilities like Log4Shell doubled between 2018 and 2020.
Attackers see APIs… however do you?
Akamai mentioned that amongst different issues, Neosec’s answer gives visibility of APIs — which is of important significance as a result of organizations usually don’t know the place, or what number of APIs they’ve under the digital decks.
“That’s precedence primary,” mentioned Chokshi. “In safety language, it’s discovery and visibility. And it’s going to be fascinating as a result of clients need the baseline: they need to perceive (their API publicity).”
As a result of giant organizations can have 1000’s of apps, they usually need to deal with high-risk APIs, as a result of they’ll’t deal with all the things directly, he added.
“They’re utilizing a number of completely different exit factors, API gateways like (Google Cloud’s) Apigee, or Kong, or load balancers like F5, so there’s this complete complexity that every enterprise surroundings has that we’ve got to work with clients to sort out as we go ahead. The top goal can be visibility and discovery found out, and intelligence, after which work on safety: How a lot of this may we do with blocking, how a lot with response and may we automate?” Chokshi mentioned.
Former FBI Particular Agent Dean Phillips, govt director of public sector applications at API safety agency Noname mentioned the dangers are multiplied by visibility points, a perennial downside with enterprises with giant and rising numbers of built-in purposes and interfaces.
“We have now discovered that in personal safety upwards of 30% of APIs which are energetic in an surroundings are unknown by customers,” he mentioned “So there may be rather a lot that goes on that customers simply aren’t conscious of, together with motion of delicate knowledge, not simply names and addresses however social safety numbers, birthdays, that the applying doesn’t essentially want or use. It’s a significant downside. When you don’t know what you’ve, or what it’s doing, how do you shield it?”
Rising API assault incidents in 2022
In accordance with Google Cloud Cybersecurity Motion Staff’s April 2023 Risk Horizons Report, the rise in API compromise was a consider one-fifth of incidents final yr. In accordance with the report, clients delayed safety upgrades as a result of “they frightened that such upgrades may additionally convey unanticipated API modifications, which could undermine their purposes’ performance.”
The report mentioned, nevertheless, that APIs don’t really change with minor upgrades, addressing Kubernetes cluster’s total working surroundings, and the scope of the updates might be managed. “Prospects weren’t all the time conscious of this configuration choice, nevertheless,” the report mentioned.
Rising deal with API safety
Due to the ubiquity of APIs as intermediaries in increasingly cloud native transactions, Chokshi mentioned he sees the API safety market probably changing into a safety superset.
“The interactions will likely be that a lot better due to areas just like the automotive business, healthcare, and sensible cities, versus traditional finish consumer or cellular purposes,” he mentioned.
“You even have numerous companies the place APIs are important to the again finish: A buyer is attempting to open an app or account, and within the again finish there’s a credit score examine, or different actions. Increasingly business-to-business transactions happening on this cloud financial system, together with provide chains, are API-driven. The API market, usually, is quickly rising and the tooling that’s required to maintain up is missing. Safety turns into much more necessary due to that,” Chokshi added.
Phillips agrees APIs are an brisk area. “It’s changing into white scorching, and plenty of people are attempting to get entangled in API safety as a result of there’s a rising recognition that they’re the primary assault vector,” he mentioned, noting that in 2022, Gartner had estimated that by final yr, APIs can be the No. 1 assault vector. “And we’ve got seen super progress,” Phillips mentioned.
API surveillance joins the platform
Alamai’s acquisition follows a shift away from single-point options to complete providers — from merchandise to platforms — the virtues of which business consultants have been extolling for years.
“It’s a relentless dialog between best-of-breed expertise and platform options,” mentioned Wendi Whitmore, SVP of Palo Alto Networks’ Unit 42 crew. “The dialogue beforehand had been one or the opposite. I’ll say that our means to offer a much wider vary of options throughout expertise is admittedly compelling, and I’ll say nearly all of our merchandise are better of breed. It is going to be harder for organizations to compete in a world fixing one small downside,” she mentioned. “There may be by no means one single silver bullet. It’s too advanced immediately.”
Chokshi mentioned Akamai’s acquisition — and a security-platform method to cyberdefense — permits the agency to profit from adjacency in order that an attacker doesn’t get misplaced in transit between one level of visibility (or safety product if the group is utilizing a number of distributors) and one other. “We’re already offering a excessive stage of safety, they’re snug with our portals and platforms and so this turns into a further functionality in that very same continuum.”
Phillips, who mentioned Noname employs a “left of growth” method — basically shifting left to handle API vulnerabilities earlier than an incident makes them apparent — predicts there will likely be extra consolidation that brings API safety capabilities beneath the aegis of main gamers. “There’s sufficient recognition within the business that API safety is rising. APIs have been round for a very long time however recognition of vulnerabilities hasn’t. Assaults are growing however the query turns into what’s the influence? Is the ache of the assault sufficient to drive motion?”










