
Examine Level Analysis launched a brand new report that exposes the actions of a Chinese language state-sponsored APT menace actor the analysis workforce tracks as Camaro Dragon. The menace actor makes use of a customized implant to compromise a selected TP-Hyperlink router mannequin and steal data from it, in addition to present backdoor entry to the attackers.
The report gives further technical particulars about this cyberattack, who’s impacted and easy methods to detect and shield towards this safety menace.
Bounce to:
“Horse Shell” implant present in TP-Hyperlink router firmware
Throughout their evaluation of Camaro Dragon, the researchers found numerous information used of their assaults, with two of them being TP-Hyperlink firmware photographs for the WR940 router mannequin launched round 2014. These implants have been present in an assault marketing campaign focused primarily at European International Affairs entities.
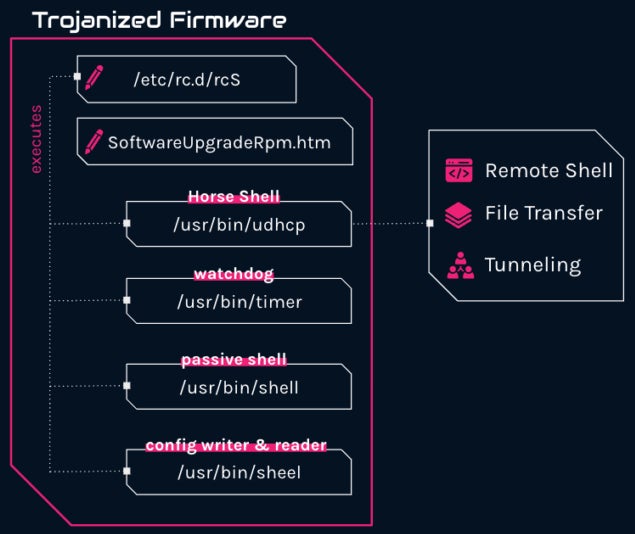
By evaluating these information to legit firmware photographs for the TP-Hyperlink WR940 router, Examine Level found that the file system has been altered, with 4 information added to the firmware and two information modified with a purpose to execute a malicious implant (Determine A).
Determine A
The primary discovery reveals the attackers modified the SoftwareUpgradeRpm.htm legit file from the firmware, which is accessible by way of the router’s internet interface and permits handbook firmware upgrades (Determine B).
Determine B
The modified model of the web page utterly hides the firmware improve possibility so the administrator can not improve it anymore (Determine C).
Determine C

The second discovery is the modification of the file /and so on/rc.d/rcS that’s a part of the working system’s startup scripts. The attackers added the execution of three of the information they added on the firmware’s file system so it could be executed every time the working system restarts, guaranteeing the persistence of the implant on the compromised router.
One file to be executed at boot time by the script is /usr/bin/shell. This file is a password-protected bind shell on port 14444, which implies it’s doable to get entry to this shell by offering it with a very good password. A fast examination of the file revealed the password (J2)3#4G@Iie), saved in clear textual content within the file.
One other file, /usr/bin/timer, gives a further layer of persistence for the attackers as its sole position is to make sure that /usr/bin/udhcp is working, with this file being the primary implant.
The primary malicious implant is /usr/bin/udhcp, dubbed Horse Shell by Examine Level Analysis. The title comes from the file’s inside knowledge. It runs within the background as a daemon on the system and gives three functionalities: distant shell, file switch and tunneling.
One final file, /usr/bin/sheel, is answerable for writing and studying a C2 configuration it shops in one other partition of the gadget. The information is written and skim immediately from a block gadget in an apparent effort to remain undetected or noticed by an administrator.
As soon as the udhcp implant is executed, it collects and sends knowledge to its C2 server: person and system names, working system model and time, CPU structure and variety of CPUs, complete RAM, IP and MAC addresses, options supported by the implant (distant shell, file switch and tunneling) and the variety of energetic connections.
In keeping with Examine Level Analysis, the truth that the malware sends knowledge associated to the CPU structure and help functionalities to the menace actor suggests the attackers might need different variations supporting completely different gadgets and completely different units of functionalities.
The malware communicates with its C2 server through the use of the HTTP protocol on port 80, encrypting the content material with a customized encryption scheme. The usage of this technique ensures the information might be transmitted as gadgets normally use such a way to speak on networks and the port 80 is usually not blocked by firewalls. The HTTP content material additionally has particular hard-coded headers that the researchers discovered on coding boards and repositories from Chinese language web sites and contains the language code zh-CN particular to China. As well as, typos within the code point out the developer won’t be a local English speaker.
The tunneling performance permits the attackers to create a sequence of nodes, with every node being a compromised gadget. Each node solely had details about the earlier and subsequent nodes, so it makes it more durable to trace the attackers as they could use a number of completely different nodes for speaking with the implant. Additionally, in case one node is immediately eliminated, the attacker can nonetheless route visitors by way of a special node within the chain.
Ties between Camaro Dragon and Mustang Panda
Examine Level Analysis mentions the usage of code present in Chinese language coding boards solely and the usage of a zh-cn language parameter in HTTP headers utilized by the implant. The researchers additionally point out the invention of all kinds of instruments utilized by the attacker — a few of them being generally related to Chinese language state-sponsored menace actors.
The group exercise has vital overlaps with one other Chinese language state-sponsored APT menace actor dubbed Mustang Panda. The strongest overlap as noticed by Examine Level consists of Camaro Dragon utilizing the identical IP handle as Mustang Panda for C2 servers, however different non-disclosed components make the researcher point out that “there may be sufficient proof to counsel that Camaro Dragon has vital overlaps with Mustang Panda, alas we will’t say that it is a full overlap or that these two are the very same group.”
Within the case of Horse Shell, it’s doable that different menace actors will use it, particularly seeing the ties between Camaro Dragon and Mustang Panda. It’s even doable that Mustang Panda would possibly use it sooner or later for their very own operations.
Router implants are a rising menace
Router implants aren’t very fashionable for attackers as a result of they require extra creating abilities. Within the Horse Shell case, it wanted good information of MIPS32-based working techniques. Additionally it is wanted to personal one or a number of of the routers with a purpose to develop and check the code previous to deploying it in an actual assault.
However, gadgets resembling routers are much less monitored and fewer anticipated to be compromised. Lately, router infections have appeared.
In 2018, with the Slingshot APT, attackers exploited a vulnerability in Mikrotik routers to plant malware on it with the objective of infecting the router administrator and shifting ahead with their assault.
In 2021, the French governmental pc emergency response workforce CERT-FR reported about Chinese language menace actor APT31 (aka Judgment Panda or Zirconium) utilizing compromised small workplace/dwelling workplace routers, primarily from Pakedge, Sophos and Cisco. The company found about 1,000 IP addresses utilized by the attacker throughout its assault marketing campaign.
In 2022, the ZuoRAT malware utilized by an unknown but probably state-sponsored menace actor focused SOHO routers from ASUS, Cisco, DrayTek and Netgear.
In 2023, the Hiatus malware struck the U.S. and Europe, concentrating on routers from DrayTek principally utilized by medium-sized organizations, together with firms in prescription drugs and IT companies, consulting corporations and governments.
Final month, Russian menace actor APT28 (aka Fancy Bear, Strontium, Pawn Storm) exploited a Cisco router vulnerability to focus on U.S. authorities establishments and different organizations in Europe and Ukraine.
Consultants from Examine Level Analysis specific their concern about router compromises and write that “such capabilities and varieties of assaults are of constant curiosity and focus of Chinese language-affiliated menace actors.”
Consultants within the area count on router compromises to extend sooner or later.
Find out how to detect this menace and shield from it
Examine Level strongly advises to test HTTP community communications and hunt for the precise HTTP headers utilized by the malware. These headers have been shared in Chinese language-speaking coding boards, so it may also point out an assault from menace actors apart from Camaro Dragon.
The TP-Hyperlink file system on WR940 router gadgets ought to be checked for the presence of the reported information and modifications of the prevailing information.
Because the preliminary an infection to put in the modified firmware on routers stays unknown, it’s strongly suggested to at all times deploy patches and preserve all software program and firmware updated to keep away from being compromised by attackers triggering a standard vulnerability.
It’s suggested to vary the default credentials on such gadgets so attackers can not simply log in with it, as some routers are configured with default credentials, that are publicly identified and might be utilized by anybody to log in to the router.
Distant administration of routers ought to solely be performed from the inner community; it shouldn’t be accessible from the web.
It’s suggested to observe router exercise and test logs for anomalies and suspicious exercise or unauthorized entry makes an attempt.
Disclosure: I work for Development Micro, however the views expressed on this article are mine.










