As soon as used solely by the cybercriminals behind REVil ransomware and the Gootkit banking trojan, GootLoader and its major payload have advanced into an preliminary entry as a service platform—with Gootkit offering info stealing capabilities in addition to the aptitude to deploy post-exploitation instruments and ransomware.
GootLoader is thought for utilizing search engine marketing (Search engine marketing) poisoning for its preliminary entry. Victims are sometimes enticed into clicking on malicious adware or hyperlinks disguised as legit advertising, or on this case a legit Google search directing the person to a compromised web site internet hosting a malicious payload masquerading as the specified file. If the malware stays undetected on the sufferer’s machine, it makes approach for a second-stage payload generally known as GootKit, which is a extremely evasive data stealer and distant entry Trojan (RAT) used to determine a persistent foothold within the sufferer’s community surroundings. GootKit can be utilized to deploy ransomware or different instruments, together with Cobalt Strike, for follow-on exploitation.
Detection of a brand new GootLoader variant actively being utilized by adversaries earlier this 12 months led to a broad risk searching marketing campaign by Sophos X-Ops MDR for GootLoader situations throughout buyer environments. As is typical of Gootloader, the brand new variant was discovered to be utilizing Search engine marketing poisoning—the usage of search engine marketing ways to place malicious web sites managed by GootLoader’s operators excessive within the outcomes for particular search phrases—to ship the brand new, JavaScript-based Gootloader bundle. On this case, we discovered the GootLoader actors utilizing search outcomes for details about a specific cat and a specific geography getting used to ship the payload: “Are Bengal Cats authorized in Australia?”
In the course of the risk hunt marketing campaign, MDR found a .zip archive used to ship GootLoader’s first-stage payload whereas reviewing an impacted person’s browser historical past. This allowed MDR to determine the compromised web site that was internet hosting the malicious payload. This report highlights the MDR investigation course of and the technical particulars of the uncovered GootLoader marketing campaign.
Technical Evaluation and Identification
First-stage payload
On March 27, 2024, the MDR crew carried out a proactive risk searching marketing campaign throughout a number of prospects estates, following lately reported identification of a brand new GootLoader variant being actively exploited within the wild.
Our investigation revealed the risk actor was utilizing Search engine marketing poisoning via an simply accessed on-line discussion board discovered by way of a easy Google search, initiated by the person for ‘Do you want a license to personal a Bengal cat in Australia’. The primary search end result took us to this URL:
hxxps[://]ledabel[.]be/en/are-bengal-cats-legal-in-australia-understanding-the-laws-and-regulations/#:~:textual content=Eachpercent20statepercent20andpercent20territorypercent20in,topercent20keeppercent20thempercent20aspercent20pets.
Instantly after the person clicks the hyperlink, a suspicious .zip file was downloaded to C:Customers

Second-stage payload
Upon evaluation of the working processes, we have been capable of decide {that a} small JavaScript file was dropping a big JavaScript file on the location C:Customers
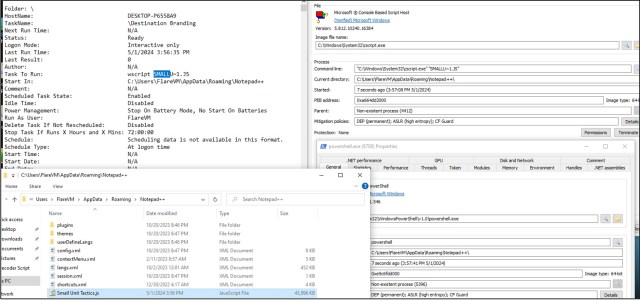
We moreover noticed the creation of a scheduled process named “Enterprise Aviation” with the command line “wscript REHABI~1.JS” (as proven in Determine 3). This was suspected to be a persistence methodology during which the risk actor was using WScript.exe to execute the second-stage payload of GootKit.
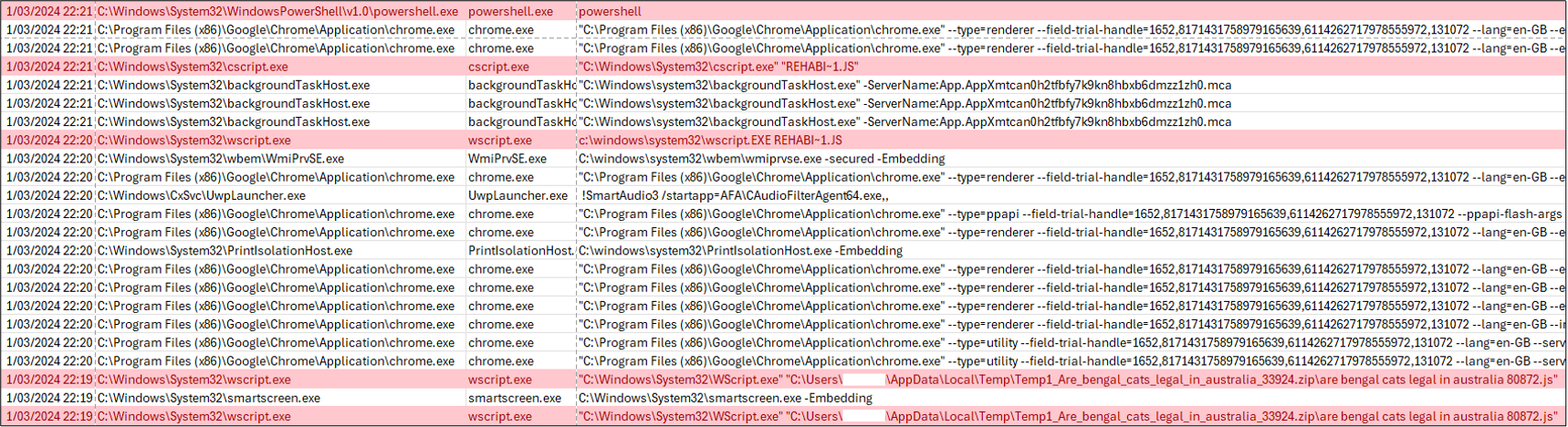

We additionally famous the utilization of the command C:WindowsSystem32cscript.exe REHABI~1.JS spawning PowerShell.exe, as proven in Determine 4. The cscript.exe command line software is restricted to Home windows Server. The instructions handed to PowerShell weren’t captured on this case.

Nevertheless, inspecting the URL historical past, we noticed PowerShell.exe reaching out to the next domains, as proven in Determine 5. Third-stage payload
Within the case the MDR crew examined, our crew didn’t observe the third stage being profitable in reaching a full deployment of GootKit, stopping the obtain of any further malicious tooling. This stage sometimes is the place the deployment of further instruments similar to Cobalt Strike happens, or when ransomware is added to the sufferer’s machine.
Malware Triage
Static Evaluation
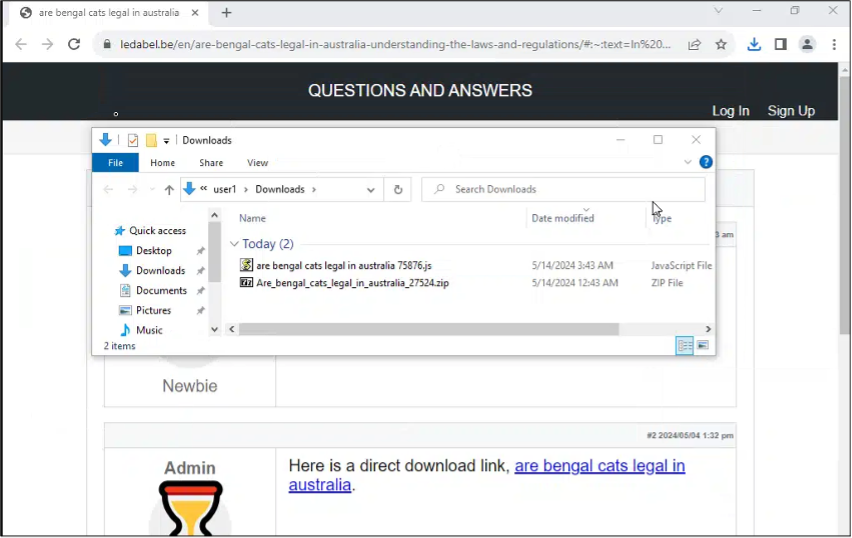
MDR carried out a static evaluation of the of the .zip pattern obtained from the malicious URL hxxps[://]ledabel[.]be/en/are-bengal-cats-legal-in-australia-understanding-the-laws-and-regulations/#:~:textual content=Inpercent20mostpercent20casespercent2Cpercent20youpercent20do,apercent20Bengalpercent20catpercent20inpercent20Australia. Inside the zip file was a JavaScript named “are bengal cats authorized in australia 72495.js”.
As we famous above, the JavaScript’s identify is modified every time the file is downloaded with a special concluding numerical sequence. This was additionally noticed when extracting the small JavaScript from the zip file, as proven in Determine 6. For instance, customers could observe a filename with are bengal cats authorized in australia 75876.zip as an alternative, when trying to acquire a pattern from the malicious URL.
A string evaluation of the dropped file was not helpful in figuring out its intent, because the JavaScript was closely obfuscated—as is frequent in Gootloader samples. The script additionally included boilerplate licensing feedback to make it seem like a legit JavaScript, as proven in Determine 7.
Nevertheless, Strings evaluation of the secondary bigger JavaScript that was downloaded into C:Customers

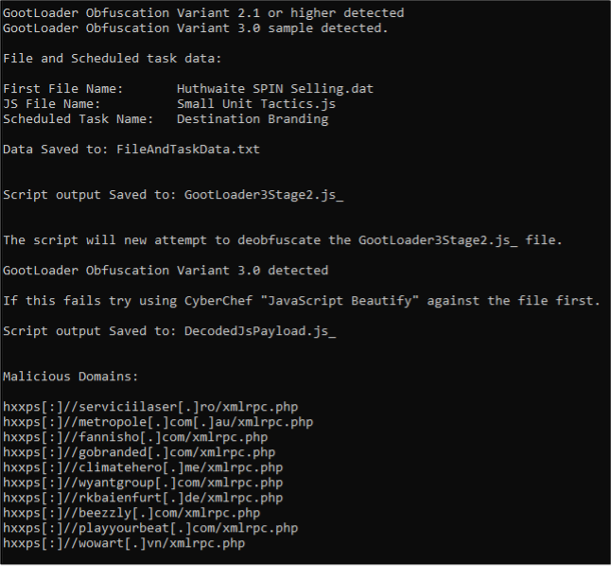
MDR used a Python script created by Mandiant for auto-decoding of GootLoader JavaScript to statically analyze the initially downloaded Are_bengal_cats_legal_in_australia_72495.js. As proven in Determine 9, the file was recognized as Gootloader variant 3.0 via the obfuscation methodology, the place the primary file created was named Huthwaite SPIN promoting.dat adopted by Small Items Ways.js and Scheduled Process named Vacation spot Branding. The decoder additionally recognized numerous malicious domains inside the obfuscated strings.
Dynamic evaluation
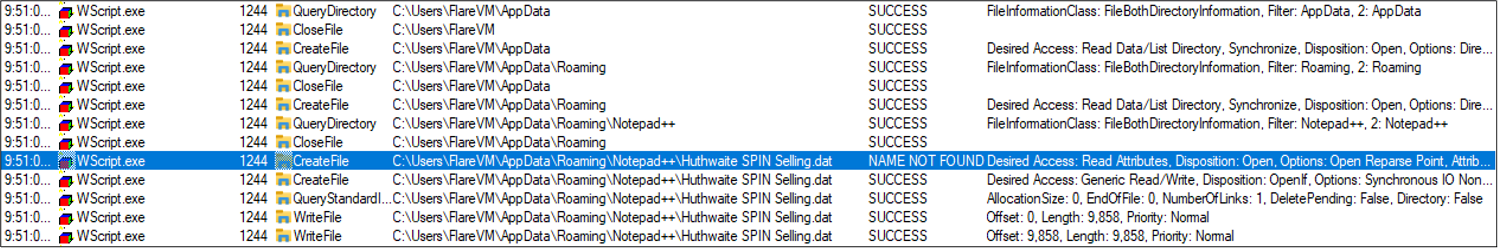
Numerous dynamic evaluation instruments have been utilized to look at the conduct of the malicious JavaScript. Upon execution, WScript.exe was noticed creating the primary file positioned inside C:Customers
Shortly after Wscript.exe executed Are_bengal_cats_legal_in_australia_72495.js, Course of Hacker confirmed CScript.exe and Powershell.exe being created with a conhost.exe spawned, as proven in Determine 11. MDR noticed that Wscript.exe would terminate, adopted by Cscript.exe that may additionally terminate shortly after, after which Powershell.exe was created.

Persistence was obtained by way of CScript.exe executing the file SMALLU~1.js by way of a scheduled process named Vacation spot Branding (with command line wscript SMALLU ~1.js , as proven in Determine 12). In the course of the lab evaluation, the secondary JavaScript could be dropped inside any folders positioned inside C:Customers
MDR performed community and C2 examinations utilizing Wireshark and FakeNet to carry out a community seize through the execution of Are_bengal_cats_legal_in_australia_72495.js. FakeNet confirmed numerous domains being reached out to with GET /xmlrpc.php HTTP/1.1 requests by way of Powershell.exe. The requests contained Base64-encoded cookies which, when decoded, confirmed enumeration info relating to gadget directories and host info such because the folder path of C:Customers
Examination of the PCAP seize lists numerous domains that have been additionally recognized throughout static evaluation, as proven in Determine 14. These domains and IOCs have been labeled by Sophos Labs as malware/callhome ; the preliminary and secondary JavaScript recordsdata are labeled as JS/Drop-DIJ and JS/Gootkit-AW respectively.

MITRE mapping
The next chart maps the noticed ways to the MITRE ATT&CK® framework.
| Tactic | Approach | Sub-Approach | ID |
| Reconnaissance | |||
| Useful resource Improvement | Stage Capabilities | Add Malware
Search engine marketing Poisoning |
T1608.001
T1608.006 |
| Preliminary Entry | Drive-by Compromise | T1189 | |
| Execution | Command and Scripting Interpreter | JavaScript | T1059.007 |
| Persistence | Scheduled Process/Job | Scheduled Process | T1053.005 |
| Privilege Escalation | |||
| Protection Evasion | Obfuscated Information or Data | Embedded Payloads | T1027.009 |
| Credential Entry | |||
| Discovery | System Data Discovery | T1082 | |
| Lateral Motion | |||
| Assortment | |||
| Command and Management | |||
| Exfiltration | Exfiltration Over Net Service | T1567 | |
| Impression |
Conclusion
GootLoader is considered one of plenty of persevering with malware-delivery-as-a-service operations that closely leverage search outcomes as a method to achieve victims. Using search engine marketing, and abuse of search engine promoting to lure targets to obtain malware loaders and dropper, usually are not new—GootLoader has been doing this since at the least 2020, and we’ve noticed Raccoon Stealer and different malware-as-a-service operations doing the identical for simply as lengthy. However we’ve seen continued progress on this strategy to preliminary compromise, with a number of huge campaigns utilizing this method over the previous 12 months.
Sophos endpoint safety blocks GootLoader via plenty of behavioral and malware-specific detections. However customers ought to nonetheless look out for search outcomes and search commercials that appear too good to be true on domains which might be off the crushed path—whether or not they’re seeking to get a Bengal Cat or not.
Indicators of Compromise
A listing of IOCs is obtainable as a CSV file within the Sophos GitHub repository right here.