Picture: Shutterstock, ArtHead.
In an effort to mix in and make their malicious visitors harder to dam, internet hosting companies catering to cybercriminals in China and Russia more and more are funneling their operations by way of main U.S. cloud suppliers. Analysis revealed this week on one such outfit — a sprawling community tied to Chinese language organized crime gangs and aptly named “Funnull” — highlights a persistent whac-a-mole downside dealing with cloud companies.
In October 2024, the safety agency Silent Push revealed a prolonged evaluation of how Amazon AWS and Microsoft Azure had been offering companies to Funnull, a two-year-old Chinese language content material supply community that hosts all kinds of pretend buying and selling apps, pig butchering scams, playing web sites, and retail phishing pages.
Funnull made headlines final summer time after it acquired the area title polyfill[.]io, beforehand the house of a widely-used open supply code library that allowed older browsers to deal with superior features that weren’t natively supported. There have been nonetheless tens of hundreds of official domains linking to the Polyfill area on the time of its acquisition, and Funnull quickly after performed a supply-chain assault that redirected guests to malicious websites.
Silent Push’s October 2024 report discovered an enormous variety of domains hosted through Funnull selling playing websites that bear the emblem of the Suncity Group, a Chinese language entity named in a 2024 UN report (PDF) for laundering hundreds of thousands of {dollars} for the North Korean Lazarus Group.
In 2023, Suncity’s CEO was sentenced to 18 years in jail on expenses of fraud, unlawful playing, and “triad offenses,” i.e. working with Chinese language transnational organized crime syndicates. Suncity is alleged to have constructed an underground banking system that laundered billions of {dollars} for criminals.
It’s possible the playing websites coming by way of Funnull are abusing high on line casino manufacturers as a part of their cash laundering schemes. In reporting on Silent Push’s October report, TechCrunch obtained a remark from Bwin, one of many casinos being marketed en masse by way of Funnull, and Bwin stated these web sites didn’t belong to them.
Playing is unlawful in China besides in Macau, a particular administrative area of China. Silent Push researchers say Funnull could also be serving to on-line gamblers in China evade the Communist celebration’s “Nice Firewall,” which blocks entry to playing locations.
Silent Push’s Zach Edwards stated that upon revisiting Funnull’s infrastructure once more this month, they discovered dozens of the identical Amazon and Microsoft cloud Web addresses nonetheless forwarding Funnull visitors by way of a dizzying chain of auto-generated domains earlier than redirecting malicious or phishous web sites.
Edwards stated Funnull is a textbook instance of an rising development Silent Push calls “infrastructure laundering,” whereby crooks promoting cybercrime companies will relay some or all of their malicious visitors by way of U.S. cloud suppliers.
“It’s essential for world internet hosting firms based mostly within the West to get up to the truth that extraordinarily low high quality and suspicious internet hosts based mostly out of China are intentionally renting IP house from a number of firms after which mapping these IPs to their prison shopper web sites,” Edwards advised KrebsOnSecurity. “We’d like these main hosts to create inside insurance policies in order that if they’re renting IP house to at least one entity, who additional rents it to host quite a few prison web sites, all of these IPs ought to be reclaimed and the CDN who bought them ought to be banned from future IP leases or purchases.”
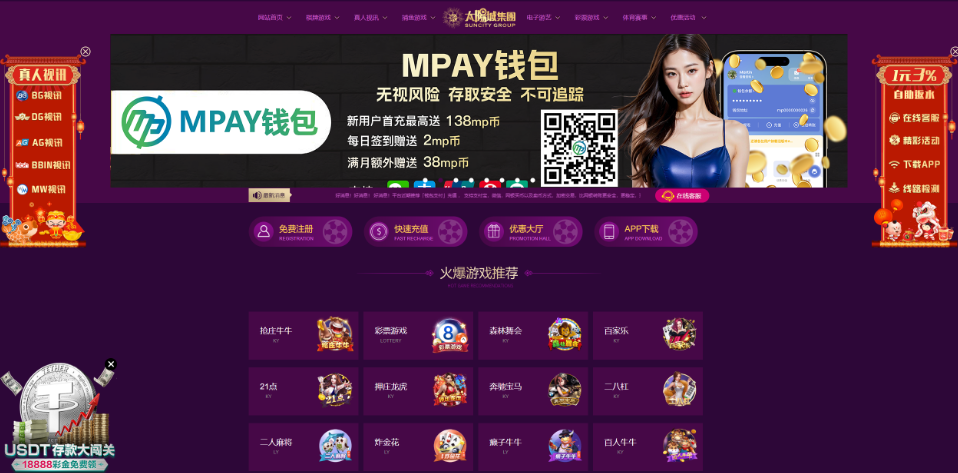
A Suncity playing web site promoted through Funnull. The websites function a immediate for a Tether/USDT deposit program.
Reached for remark, Amazon referred this reporter to an announcement Silent Push included in a report launched at the moment. Amazon stated AWS was already conscious of the Funnull addresses tracked by Silent Push, and that it had suspended all recognized accounts linked to the exercise.
Amazon stated that opposite to implications within the Silent Push report, it has each motive to aggressively police its community towards infrastructure laundering, noting the accounts tied to Funnull used “fraudulent strategies to briefly purchase infrastructure, for which it by no means pays. Thus, AWS incurs damages on account of the abusive exercise.”
“When AWS’s automated or handbook techniques detect potential abuse, or after we obtain stories of potential abuse, we act shortly to research and take motion to cease any prohibited exercise,” Amazon’s assertion continues. “Within the occasion anybody suspects that AWS assets are getting used for abusive exercise, we encourage them to report it to AWS Belief & Security utilizing the report abuse type. On this case, the authors of the report by no means notified AWS of the findings of their analysis through our easy-to-find safety and abuse reporting channels. As a substitute, AWS first discovered of their analysis from a journalist to whom the researchers had supplied a draft.”
Microsoft likewise stated it takes such abuse critically, and inspired others to report suspicious exercise discovered on its community.
“We’re dedicated to defending our clients towards this type of exercise and actively implement acceptable use insurance policies when violations are detected,” Microsoft stated in a written assertion. “We encourage reporting suspicious exercise to Microsoft so we are able to examine and take applicable actions.”
Richard Hummel is menace intelligence lead at NETSCOUT. Hummel stated it was that “noisy” and ceaselessly disruptive malicious visitors — reminiscent of automated software layer assaults, and “brute pressure” efforts to crack passwords or discover vulnerabilities in web sites — got here principally from botnets, or giant collections of hacked gadgets.
However he stated the overwhelming majority of the infrastructure used to funnel this kind of visitors is now proxied by way of main cloud suppliers, which might make it tough for organizations to dam on the community stage.
“From a defenders perspective, you’ll be able to’t wholesale block cloud suppliers, as a result of a single IP can host hundreds or tens of hundreds of domains,” Hummel stated.
In Could 2024, KrebsOnSecurity revealed a deep dive on Stark Industries Options, an ISP that materialized at the beginning of Russia’s invasion of Ukraine and has been used as a worldwide proxy community that conceals the true supply of cyberattacks and disinformation campaigns towards enemies of Russia. Consultants stated a lot of the malicious visitors traversing Stark’s community (e.g. vulnerability scanning and password brute pressure assaults) was being bounced by way of U.S.-based cloud suppliers.
Stark’s community has been a favourite of the Russian hacktivist group known as NoName057(16), which ceaselessly launches large distributed denial-of-service (DDoS) assaults towards quite a lot of targets seen versus Moscow. Hummel stated NoName’s historical past suggests they’re adept at biking by way of new cloud supplier accounts, making anti-abuse efforts right into a sport of whac-a-mole.
“It virtually doesn’t matter if the cloud supplier is on level and takes it down as a result of the dangerous guys will simply spin up a brand new one,” he stated. “Even when they’re solely in a position to make use of it for an hour, they’ve already accomplished their injury. It’s a extremely tough downside.”
Edwards stated Amazon declined to specify whether or not the banned Funnull customers had been working utilizing compromised accounts or stolen fee card information, or one thing else.
“I’m shocked they needed to lean into ‘We’ve caught this 1,200+ occasions and have taken these down!’ and but didn’t join that every of these IPs was mapped to [the same] Chinese language CDN,” he stated. “We’re simply grateful Amazon confirmed that account mules are getting used for this and it isn’t some front-door relationship. We haven’t heard the identical factor from Microsoft but it surely’s very possible that the identical factor is occurring.”
Funnull wasn’t all the time a bulletproof internet hosting community for rip-off websites. Previous to 2022, the community was often known as Anjie CDN, based mostly within the Philippines. One among Anjie’s properties was a web site known as funnull[.]app. Loading that area reveals a pop-up message by the unique Anjie CDN proprietor, who stated their operations had been seized by an entity often known as Fangneng CDN and ACB Group, the guardian firm of Funnull.
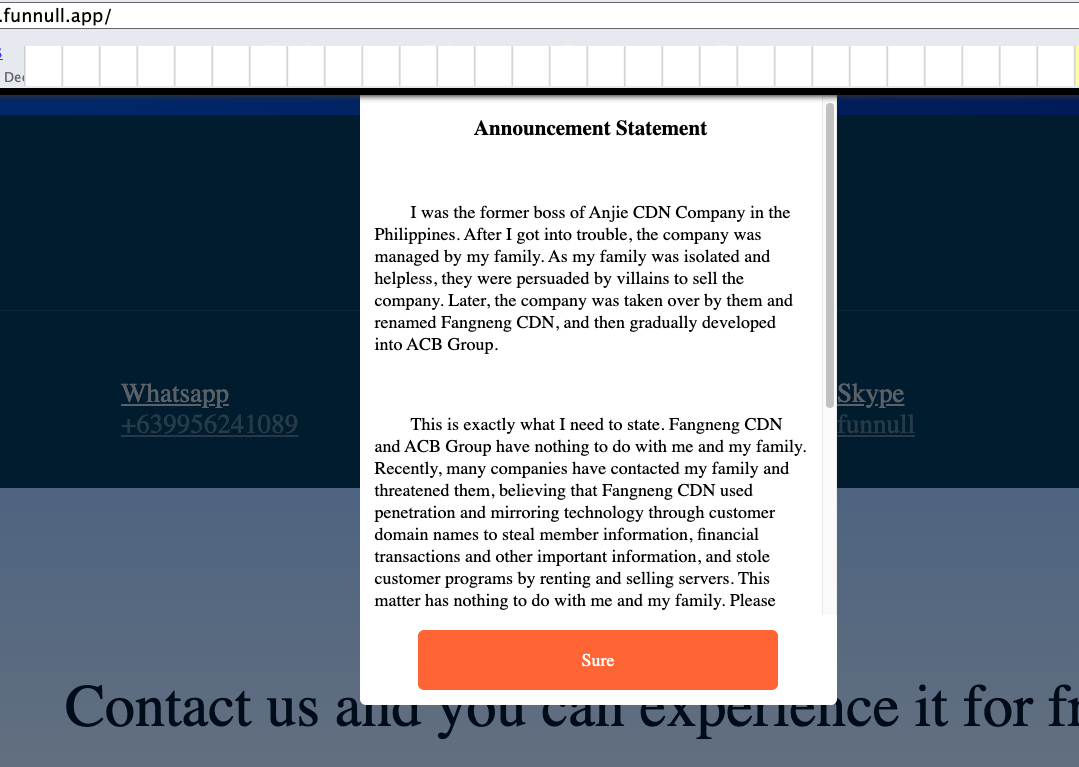
A machine-translated message from the previous proprietor of Anjie CDN, a Chinese language content material supply community that’s now Funnull.
“After I obtained into hassle, the corporate was managed by my household,” the message explains. “As a result of my household was remoted and helpless, they had been persuaded by villains to promote the corporate. Not too long ago, many firms have contacted my household and threatened them, believing that Fangneng CDN used penetration and mirroring expertise by way of buyer domains to steal member data and monetary transactions, and stole buyer applications by renting and promoting servers. This matter has nothing to do with me and my household. Please contact Fangneng CDN to resolve it.”
In January 2024, the U.S. Division of Commerce issued a proposed rule that may require cloud suppliers to create a “Buyer Identification Program” that features procedures to gather information enough to find out whether or not every potential buyer is a overseas or U.S. individual.
In response to the regulation agency Crowell & Moring LLP, the Commerce rule additionally would require “infrastructure as a service” (IaaS) suppliers to report information of any transactions with overseas individuals that may enable the overseas entity to coach a big AI mannequin with potential capabilities that might be utilized in malicious cyber-enabled exercise.
“The proposed rulemaking has garnered world consideration, as its cross-border information assortment necessities are unprecedented within the cloud computing house,” Crowell wrote. “To the extent the U.S. alone imposes these necessities, there’s concern that U.S. IaaS suppliers might face a aggressive drawback, as U.S. allies haven’t but introduced related overseas buyer identification necessities.”
It stays unclear if the brand new White Home administration will push ahead with the necessities. The Commerce motion was mandated as a part of an govt order President Trump issued a day earlier than leaving workplace in January 2021.