Reducing corners: Previous auto theft makes an attempt have concerned something from smashing home windows to relaying FOB code sequences. However a rash of bumper and headlight injury has led researchers to a brand new strategy that depends on the automobile’s controller space community (CAN) and utilizing what seems like nothing greater than a easy speaker to achieve entry. And to make issues worse, it takes about two minutes from begin to end.
Generally criminals inadvertently choose the mistaken goal when planning a criminal offense. On this case, automobile thieves leveraging a brand new tactic for keyless entry and stealing automobiles occurred to choose the Toyota SUV of a cybersecurity analyst who makes a speciality of automotive safety. And what he discovered was a tactic that went past each easy smash and seize and extra advanced sign hijacking strategies.
Ian Tabor, a cybersecurity and automobile hacking knowledgeable, recognized CVE-2023-29389, which says Toyota RAV4 automobiles are able to routinely trusting messages from different digital management models (ECUs). By pulling away the bumper to reveal the headlight connector, the thief can acquire entry to the CAN bus, permitting them to ship a solid key validation message. As soon as validated, the thief can begin the automobile and drive off with out concern.
After researching the info and communication habits throughout the RAV4’s CAN bus, Tabor found that different ECUs have been failing concurrently the CAN bus errors. The invention drove Tabor to conduct extra analysis through YouTube, the darkish internet, and different sources. Tabor’s analysis resulted in shopping for and analyzing an emergency begin system, which is meant to be used by house owners or locksmiths when a secret is misplaced, stolen, or in any other case unavailable. Working with one other automotive safety knowledgeable, Ken Tindell, Tabor efficiently reverse engineered the emergency begin system, creating an understanding of how the system communicated with the Toyota’s CAN bus.
Regardless of being marketed as an emergency begin system, the merchandise that Tabor bought and used was designed to seem like a easy JBL transportable speaker. In accordance with Tindell, a pretend play button on the speaker case is wired right into a PIC18F chip. When pressed, a CAN message burst instructs the door ECU to unlock the automobile’s doorways. As soon as unlocked, the thieves unhook the CAN Injector, get into the automobile, and drive away. Full particulars of the system, the way it works, and the way simply (and cheaply) it may be fabricated can be found on the Canis Automotive Labs web site.
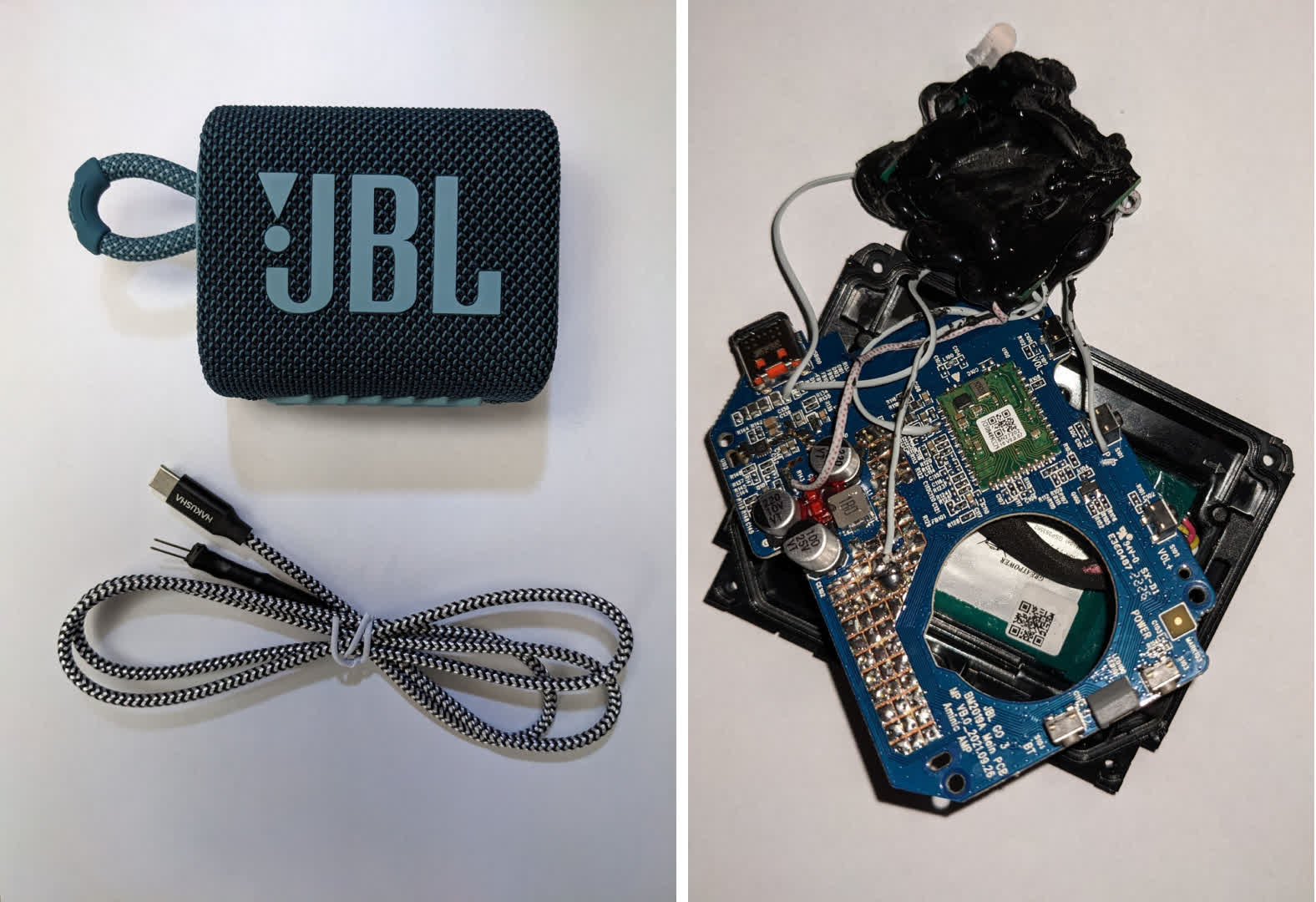
Whereas the assault was efficiently replicated on a Toyota RAV4, it is affordable to imagine {that a} related assault might happen on different automobiles utilizing the identical expertise and structure. Tabor and Tindell have alerted Toyota to the vulnerability in hopes that it may be hardened and not exploited. Sadly, they haven’t but acquired any acknowledgement or response.










