Cyber Security
T-Mobile hit by data breaches from Lapsus$ extortion group
By means of a number of breaches, the Lapsus$ cybercriminal group was capable of steal supply code from T-Cellular, says...
Read moreDon’t let plain and simple messages catch you out! – Naked Security
We’re positive you’ve heard of the KISS precept: Hold It Easy and Easy. In cybersecurity, KISS cuts two methods. KISS...
Read moreHow phishing attacks are spoofing credit unions to steal money and account credentials
Attackers are impersonating native credit score unions to seize private data and extract cash, says Avanan. Picture: iStock/jauhari1 Phishing emails...
Read moreWhere cybersecurity frameworks meet web security
A cybersecurity framework is a set of tips for enterprise environments to handle safety successfully. Cybersecurity frameworks are adaptive and...
Read moreWawa Sues Mastercard Over Data Breach Penalties
Pennsylvania-based comfort retailer and fuel station chain Wawa is looking for the return of penalties it paid to Mastercard following a 2019 information breach...
Read moreInvicti named a Challenger in 2022 Gartner Magic Quadrant for Application Security Testing
Sonali Shah - Fri, 22 Apr 2022 - Invicti has been named a Challenger within the 2022 Gartner Magic Quadrant...
Read moreOAuth 2.0: What is it and how does it work?
The OAuth authentication framework offers customers with a protected method to entry on-line companies with out placing their credentials in...
Read moreCryptomining botnet targeting Docker on Linux systems
LemonDuck, a well known cryptomining botnet, is focusing on Docker on Linux methods to coin digital cash, CloudStrike reported Thursday.The...
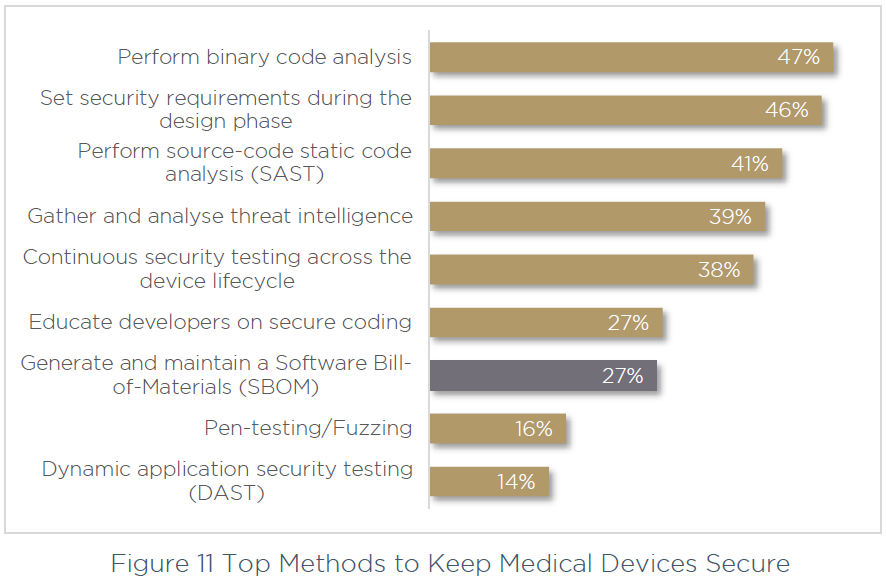
Read moreMany Medical Device Makers Skimp on Security Practices
The stakes for cybersecurity are actually life and dying within the medical system trade. Way back to 2013, then-US Vice...
Read moreQNAP warns of new bugs in its Network Attached Storage devices – Naked Security
QNAP, the makers of Networked Connected Storage (NAS) units which might be particularly widespread with dwelling and small enterprise customers,...
Read more