Cybercriminals unleashed a mean of 411,000 malicious recordsdata every single day in 2023, representing a 3% enhance from the earlier yr, in keeping with Kaspersky.
The agency’s Safety Bulletin: Statistics of the Yr Report, revealed on December 14, 2023, confirmed that specific varieties of threats additionally escalated.
One instance is using malicious desktop recordsdata (Microsoft Workplace, PDF…) to unfold malware. Out of the 125 million recordsdata detected by Kaspersky in 2023, 24,000 had been such paperwork – representing a 53% enhance from 2022.
“The expansion could also be linked to an increase in assaults using phishing PDF recordsdata, designed to pilfer information from potential victims,” the report reads.

Uptick in Backdoor Use
Microsoft Home windows remained the first goal for cyber-attacks, accounting for 88% of all malware-filled information detected day by day. Nevertheless, the agency noticed a couple of attention-grabbing samples of macOS malware, particularly in France, China and Italy.
Most of the malicious recordsdata focusing on macOS techniques had been disguised as adware.
Essentially the most widespread kind of malware continues to be Trojans, with a notable uptick in using backdoors, registering a development from 15,000 detected recordsdata per day in 2022 to 40,000 in 2023.
“Backdoors stand out as one of the crucial hazardous varieties of Trojans, offering attackers with distant management over a sufferer’s system to hold out duties equivalent to sending, receiving, executing, and deleting recordsdata, in addition to harvesting confidential information and logging laptop exercise,” Kaspersky researchers wrote.
Magniber, WannaCry and Cease/Djvu had been among the many ten Trojan households most detected by Kaspersky.
Bangladesh, Yemen, and Taiwan had been the highest three nations most focused by ransomware Trojans.
Microsoft Workplace Vulnerabilities Favored
Cybercriminals significantly favored Microsoft Workplace providers’ vulnerabilities. They represented 69.10% of all exploited vulnerabilities.
“The reporting interval was remembered for quite a few harmful vulnerabilities in enterprise purposes, like CVE-2023-34362, CVE-2023-35036 and CVE-2023-35708 in MOVEit Switch or CVE-2023-23397 in Microsoft Outlook,” famous the researchers.
Learn extra: MOVEit Exploitation Fallout Drives File Ransomware Assaults
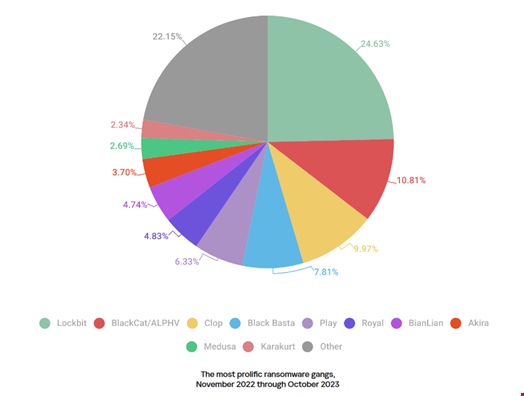
LockBit, BlackCat and Clop Most Prolific
In accordance with Kaspersky’s telemetry, essentially the most prolific ransomware group was LockBit, which claimed a 24.63% share within the whole variety of victims revealed on all of the teams’ information leak websites.
LockBit was adopted by ALPHV/BlackCat (10.81%) and Clop (9.97%).
Learn extra: ALPHV Second Most Distinguished Ransomware Pressure Earlier than Reported Downtime
Vladimir Kuskov, Head of Anti-Malware Analysis at Kaspersky, commented: “Adversaries proceed to develop new malware, methods and strategies to assault organizations and people. The variety of vulnerabilities reported can be rising yearly, and menace actors, together with ransomware gangs, use them with out hesitating.”
“Moreover, the entry barrier into cybercrime is now being lowered because of the proliferation of AI, which attackers use, for instance, to create phishing messages with extra convincing texts. In these instances, it’s important each for big organizations and for each common consumer to embrace dependable safety options.”
All figures within the report, which covers the interval from November 2022 by way of October 2023, come from the Kaspersky Safety Community (KSN) international cloud service. Knowledge was obtained from customers who had consented to it being despatched to KSN.