
The professional-Russia hacker group NoName057(16) reportedly claimed it was behind Denial of Service (DoS) assaults in opposition to the Finnish parliament’s web site on Tuesday, the day the nation joined NATO. The nation’s Technical Analysis Centre of Finland was additionally hacked, in keeping with Finnish information web site, YLE. NoName057(16) is identical group that took accountability for a distributed denial of service assault, taking down the web site for the nation’s parliament final August, and who additionally attacked Ukraine, the U.S., Poland and different European nations.
In January, a number of retailers reported that GitHub had disabled NoName057(16)’s account after the group was linked to makes an attempt to hack the Czech presidential election candidates’ web sites.
Bounce to:
Israel hit by Killnet proxy
This week, Russia-aligned hacktivists additionally attacked one of many largest names in safety, Examine Level, together with universities and medical facilities in Israel, the Jerusalem Publish reported.
The group known as itself “Nameless Sudan,” however Nadir Izrael, CTO and co-founder of Israel-based asset visibility and safety agency Armis, mentioned the attacker is probably going aligned with pro-Russia hacktivist group Killnet.
“For probably the most half the best way safety corporations observe these teams relies on the sorts of messages they submit and similarities in textual content and instruments,” he mentioned. “The messages that come from these teams are principally in Russian and English. It’s a bit like how the FBI does profiling: they search for comparable MOs and instruments, and backtrack to sources. Within the case of DDoS assaults you’re looking at a lot of totally different units worldwide from totally different areas of the world which might be suddenly attempting to entry a sure website.”
He mentioned it’s possible that the following assault will happen on April 7, 2023, as a part of the annual OpIsrael, when hackers and hacktivists assault Israeli organizations, corporations and personalities.
“Even when the disruption itself doesn’t appear outstanding, a cyberattack on a authorities or a corporation can create an underlying concern of chaos amongst residents,” he mentioned, including that 33% of world organizations are usually not taking the specter of cyberwarfare critically or had been “detached.”
Killnet drives huge improve in assaults worldwide
Killnet ramped up assaults in opposition to U.S. entities this yr and final, in keeping with software efficiency administration agency NetScout. In a brand new examine, Unveiling the New Risk Panorama, NetScout mentioned that the U.S. nationwide safety sector skilled a 16,815% improve in DDoS assaults within the second half of 2022, many associated to Killnet. These included a spike in assaults after President Joe Biden’s public remarks on the G7 Summit in June 2022, and one other spike the day Biden and French President Emmanuel Macron introduced their continued help of Ukraine in December 2022.
The typical price of cyberattacks to well being care methods within the U.S. between March 2021 and March 2022 was $10 million. Final yr, the common information breach price worldwide was $4.35 million, Statista reported.
NetScout’s ATLAS sensor community, which it says covers over 400 terabytes per second of worldwide transit, collects DDoS assault statistics from a median of 93 nations day by day. This encompasses over 50% of the world’s web visitors, in keeping with the corporate. In its report, the corporate mentioned the height sum of DDoS alert visitors in sooner or later reached 436 petabits and greater than 75 trillion packets, within the second half of 2022.
The agency mentioned exploits in opposition to web sites by Killnet and different teams within the final six months of 2022 drove a lot of the 487% improve in HTTP/HTTPS application-layer DDoS assaults since 2019. This type of assault hobbles net servers and protocols that allow networks to speak, making it inconceivable for a web site to ship content material (Determine A).
Determine A
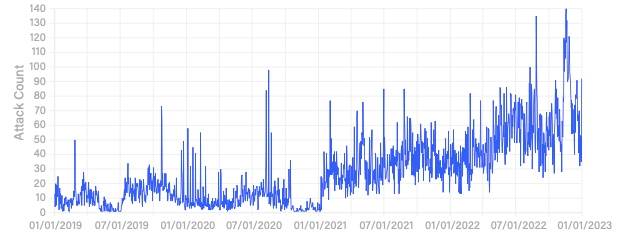
“DDoS assaults threaten organizations worldwide and problem their means to ship important providers,” mentioned Richard Hummel, risk intelligence lead of NetScout, in a press release. “With multi-terabit-per-second assaults now commonplace, and unhealthy actors’ arsenals persevering with to develop in sophistication and complexity, organizations want a method that may rapidly adapt to the dynamic nature of the DDoS risk panorama.”
The corporate mentioned direct-path assaults and conventional reflection/amplification assaults have elevated by 18% over the previous three years.
NetScout additionally discovered that:
- In 2022 some 1.35 million bots generated by such malware as Mirai, Meris and Dvinis drove some 350,000 security-related alerts, 60,000 of them issued by service suppliers.
- Carpet-bombing assaults, a way that concurrently targets total IP deal with ranges, elevated by 110% from the primary to the second half of 2022, with most assaults in opposition to web service supplier networks (Determine B).
Determine B
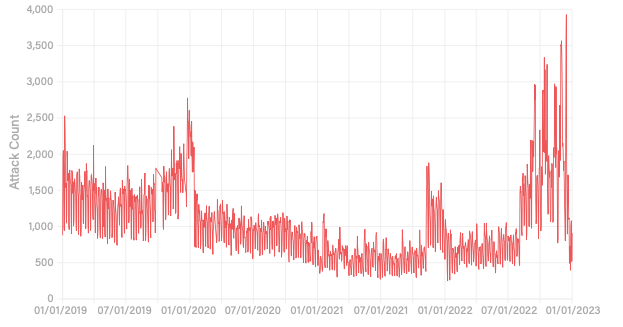
Europe, the Center East and Africa’s optical instrument and lens manufacturing sector skilled a 14,137% improve in DDoS assaults, primarily in opposition to one main distributor with greater than 6,000 assaults over the course of 4 months.
The telecommunications trade has skilled a 79% development in DDoS assaults since 2020 due to the rollout of 5G networks to the house.
NetScout’s analysis additionally discovered that DNS question flood assaults have greater than tripled since 2019, a 243% improve in adoption of this assault approach. The typical day by day assault depend for 2022 is roughly 850 assaults, a 67% improve from 2021.
Based on NetScout, these assaults focused nationwide safety and industrial banking sectors in North America, Europe, the Center East and Africa (Determine C).
Determine C
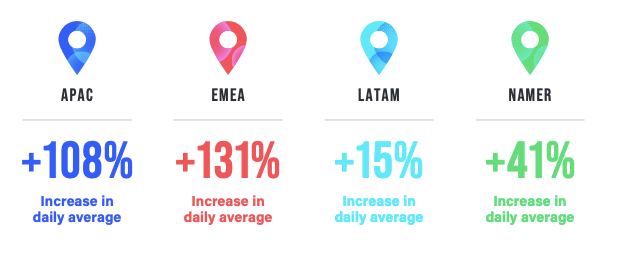
“There’s a excessive diploma of certainty that these assaults are nearly solely associated to the continued battle between Russia and Ukraine,” the agency mentioned.
With DDoS assaults rising, protection will depend on safety suppliers
There isn’t any simple repair for DDoS assaults as a result of they will exploit quite a few vulnerabilities. DDoS safety service suppliers may be wanted for bigger, extra advanced organizations. Relying on the amount of assaults, firewall options may additionally suffice.
Defensive measures embrace taking such actions as figuring out and patching working system and application-level vulnerabilities, closing ports, eradicating system entry and placing servers behind a proxy or a content material supply community. Specialised coaching in moral hacking and different defensive measures is invaluable, particularly given the shortfall in cybersecurity expertise.
To realize cybersecurity expertise and certification on your enterprise, be taught concerning the TechRepublic Academy Superior CyberSecurity Skilled Certification Bundle right here.










