The U.S. Drug Enforcement Administration (DEA) says it’s investigating reviews that hackers gained unauthorized entry to an company portal that faucets into 16 completely different federal regulation enforcement databases. KrebsOnSecurity has discovered the alleged compromise is tied to a cybercrime and on-line harassment group that routinely impersonates police and authorities officers to reap private info on their targets.
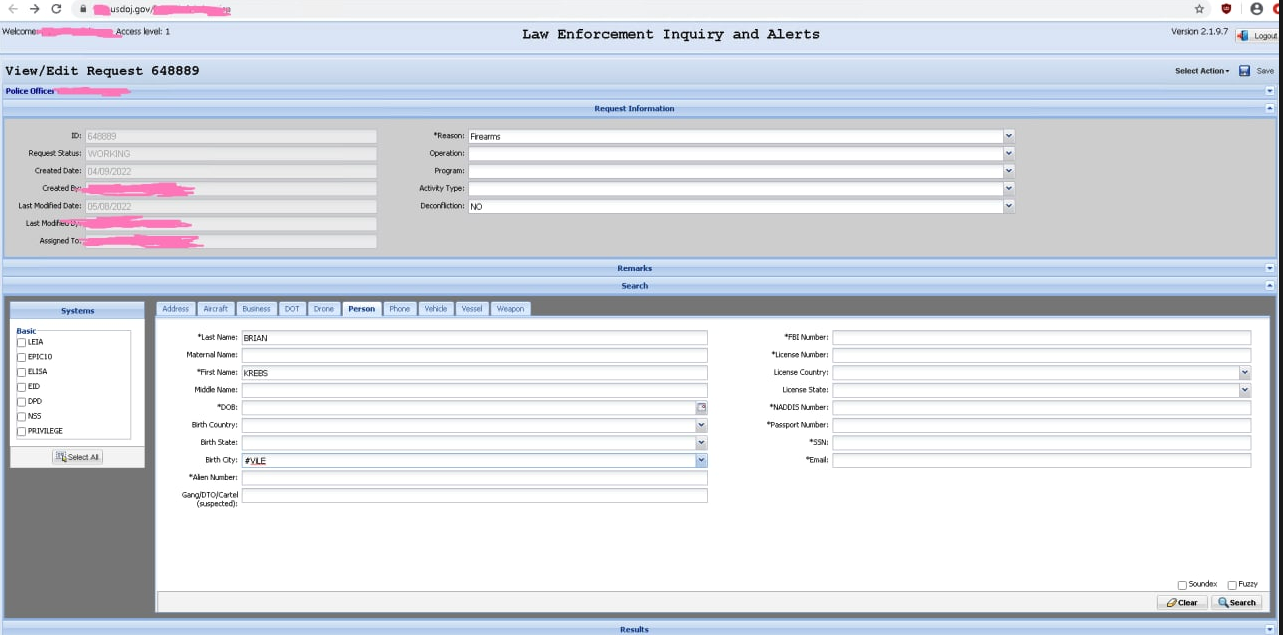
Unidentified hackers shared this screenshot of alleged entry to the Drug Enforcement Administration’s intelligence sharing portal.
On Might 8, KrebsOnSecurity obtained a tip that hackers obtained a username and password for a certified person of esp.usdoj.gov, which is the Regulation Enforcement Inquiry and Alerts (LEIA) system managed by the DEA.
KrebsOnSecurity shared details about the allegedly hijacked account with the DEA, the Federal Bureau of Investigation (FBI), and the Division of Justice, which homes each businesses. The DEA declined to touch upon the validity of the claims, issuing solely a short assertion in response.
“DEA takes cyber safety and data of intrusions significantly and investigates all such reviews to the fullest extent,” the company stated in a press release shared through e mail.
In accordance with this web page on the Justice Division web site, LEIA “offers federated search capabilities for each EPIC and exterior database repositories,” together with information categorised as “regulation enforcement delicate” and “mission delicate” to the DEA.
A doc revealed by the Obama administration in Might 2016 (PDF) says the DEA’s El Paso Intelligence Middle (EPIC) programs in Texas can be found to be used by federal, state, native and tribal regulation enforcement, in addition to the Division of Protection and intelligence group.
EPIC and LEIA even have entry to the DEA’s Nationwide Seizure System (NSS), which the DEA makes use of to determine property thought to have been bought with the proceeds of legal exercise (assume fancy automobiles, boats and houses seized from drug kingpins).
“The EPIC System Portal (ESP) permits vetted customers to remotely and securely share intelligence, entry the Nationwide Seizure System, conduct information analytics, and procure info in assist of legal investigations or regulation enforcement operations,” the 2016 White Home doc reads. “Regulation Enforcement Inquiry and Alerts (LEIA) permits for a federated search of 16 Federal regulation enforcement databases.”
The screenshots shared with this creator point out the hackers might use EPIC to lookup quite a lot of information, together with these for motor autos, boats, firearms, plane, and even drones.
Claims in regards to the purloined DEA entry had been shared with this creator by “KT,” the present administrator of the Doxbin — a extremely poisonous on-line group that gives a discussion board for digging up private info on folks and posting it publicly.
As KrebsOnSecurity reported earlier this 12 months, the earlier proprietor of the Doxbin has been recognized because the chief of LAPSUS$, a knowledge extortion group that hacked into a few of the world’s largest tech firms this 12 months — together with Microsoft, NVIDIA, Okta, Samsung and T-Cellular.
That reporting additionally confirmed how the core members of LAPSUS$ had been concerned in promoting a service providing fraudulent Emergency Information Requests (EDRs), whereby the hackers use compromised police and authorities e mail accounts to file warrantless information requests with social media corporations, cell telephony suppliers and different expertise corporations, testifying that the knowledge being requested can’t await a warrant as a result of it pertains to an pressing matter of life and loss of life.
From the standpoint of people concerned in submitting these phony EDRs, entry to databases and person accounts throughout the Division of Justice could be a significant coup. However the information in EPIC would in all probability be much more worthwhile to organized crime rings or drug cartels, stated Nicholas Weaver, a researcher for the Worldwide Pc Science Institute at College of California, Berkeley.
Weaver stated it’s clear from the screenshots shared by the hackers that they may use their entry not solely to view delicate info, but additionally submit false information to regulation enforcement and intelligence company databases.
“I don’t assume these [people] notice what they obtained, how a lot cash the cartels would pay for entry to this,” Weaver stated. “Particularly as a result of as a cartel you don’t seek for your self you seek for your enemies, in order that even when it’s found there isn’t any loss to you of placing issues ONTO the DEA’s radar.”
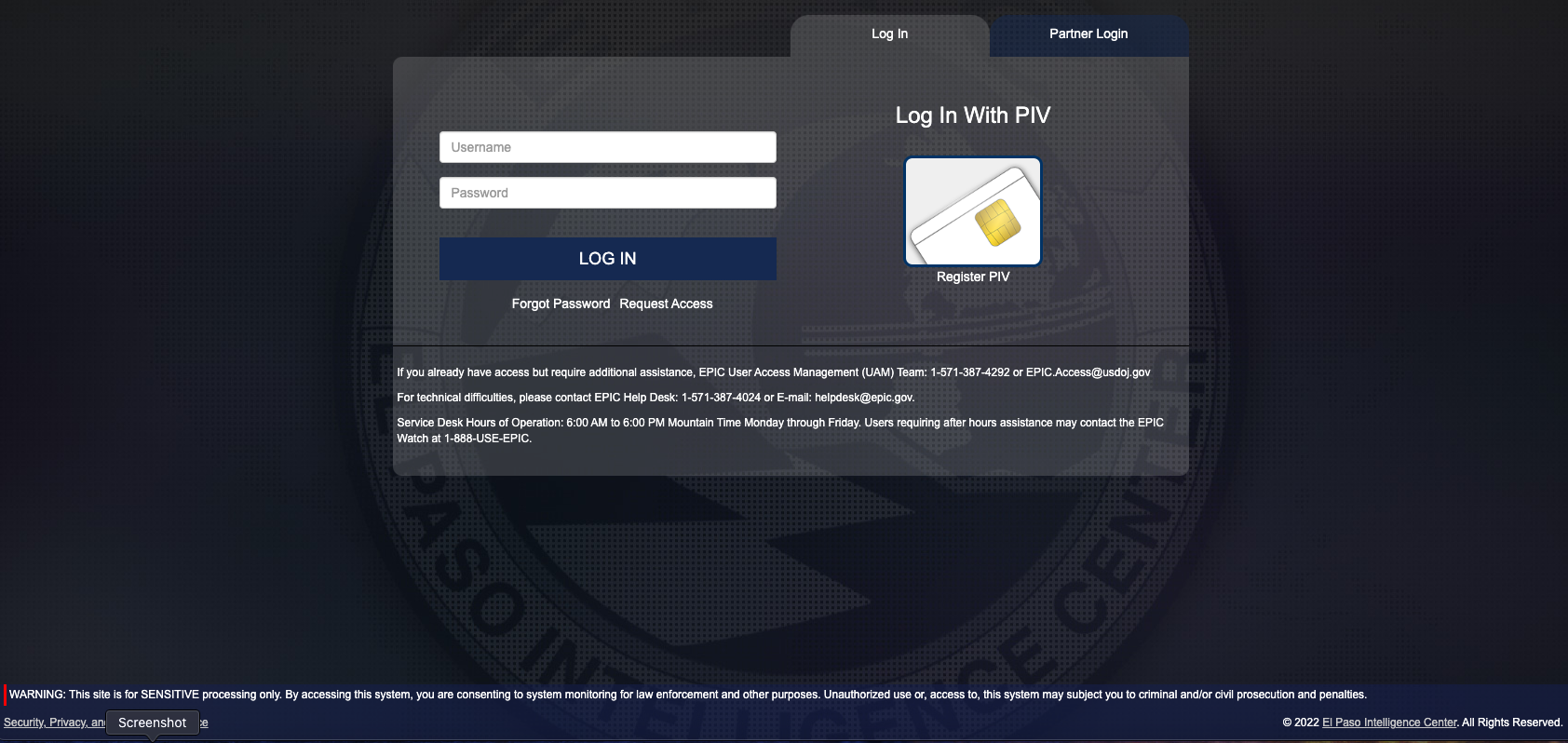
The DEA’s EPIC portal login web page.
ANALYSIS
The login web page for esp.usdoj.gov (above) means that approved customers can entry the positioning utilizing a “Private Id Verification” or PIV card, which is a reasonably sturdy type of authentication used government-wide to manage entry to federal services and data programs at every person’s acceptable safety stage.
Nonetheless, the EPIC portal additionally seems to just accept only a username and password, which would appear to radically diminish the safety worth of requiring customers to current (or show possession of) a certified PIV card. Certainly, KT stated the hacker who obtained this illicit entry was in a position to log in utilizing the stolen credentials alone, and that at no time did the portal immediate for a second authentication issue.
It’s not clear why there are nonetheless delicate authorities databases being protected by nothing greater than a username and password, however I’m keen to wager huge cash that this DEA portal just isn’t solely offender right here. The DEA portal esp.usdoj.gov is listed on Web page 87 of a Justice Division “information stock,” which catalogs the entire information repositories that correspond to DOJ businesses.
There are 3,330 outcomes. Granted, solely a few of these outcomes are login portals, however that’s simply throughout the Division of Justice.
If we assume for the second that state-sponsored overseas hacking teams can acquire entry to delicate authorities intelligence in the identical method as teenage hacker teams like LAPSUS$, then it’s long gone time for the U.S. federal authorities to carry out a top-to-bottom overview of authentication necessities tied to any authorities portals that visitors in delicate or privileged info.
I’ll say it as a result of it must be stated: The USA authorities is in pressing want of management on cybersecurity on the government department stage — ideally somebody who has the authority and political will to ultimately disconnect any federal authorities company information portals that fail to implement sturdy, multi-factor authentication.
I notice this can be much more complicated than it sounds, notably in relation to authenticating regulation enforcement personnel who entry these programs with out the good thing about a PIV card or government-issued gadget (state and native authorities, for instance). It’s not going to be so simple as simply turning on multi-factor authentication for each person, thanks partially to a broad range of applied sciences getting used throughout the regulation enforcement panorama.
However when hackers can plunder 16 regulation enforcement databases, arbitrarily ship out regulation enforcement alerts for particular folks or autos, or doubtlessly disrupt ongoing regulation enforcement operations — all as a result of somebody stole, discovered or purchased a username and password — it’s time for drastic measures.










