A 33-year-old Illinois man was sentenced to 2 years in jail right this moment following his conviction final yr for working companies that allowed paying clients to launch highly effective distributed denial-of-service (DDoS) assaults in opposition to lots of of hundreds of Web customers and web sites.
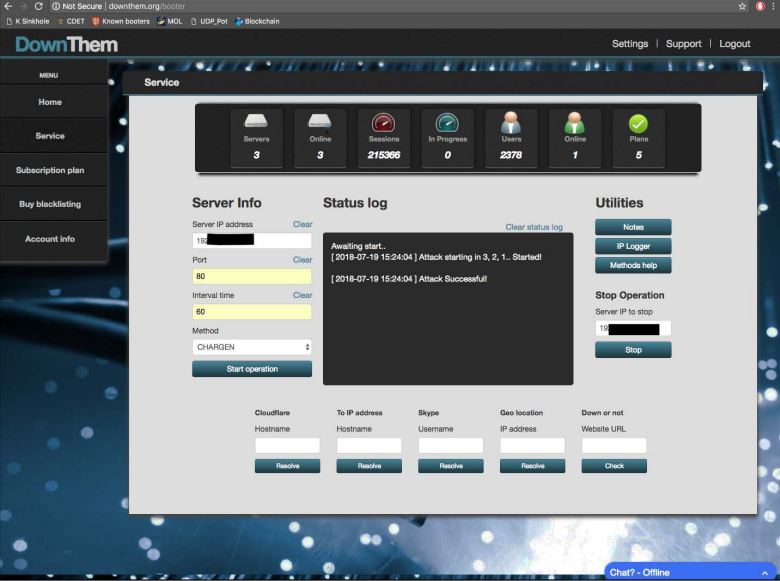
The person interface for Downthem[.]org.
Matthew Gatrel of St. Charles, Ailing. was discovered responsible for violations of the Pc Fraud and Abuse Act (CFAA) associated to his operation of downthem[.]org and ampnode[.]com, two DDoS-for-hire companies that had hundreds of consumers who paid to launch greater than 200,000 assaults.
Regardless of admitting to FBI brokers that he ran these so-called “booter” companies (and turning over loads of incriminating proof within the course of), Gatrel opted to take his case to trial, defended your entire time by public defenders. Gatrel’s co-defendant and accomplice within the enterprise, Juan “Severon” Martinez of Pasadena, Calif., pleaded responsible simply earlier than the trial.
After a nine-day trial within the Central District of California, Gatrel was convicted on all three counts, together with conspiracy to commit unauthorized impairment of a protected laptop, conspiracy to commit wire fraud, and unauthorized impairment of a protected laptop.
Prosecutors mentioned Downthem bought subscriptions permitting clients to launch DDoS assaults, whereas AmpNode offered “bulletproof” server internet hosting to clients — with an emphasis on “spoofing” servers that could possibly be pre-configured with DDoS assault scripts and lists of susceptible “assault amplifiers” used to launch simultaneous cyberattacks on victims.
Booter and stresser companies let clients decide from amongst quite a lot of assault strategies, however virtually universally essentially the most highly effective of those strategies includes what’s generally known as a “reflective amplification assault.” In such assaults, the perpetrators leverage unmanaged Area Identify Servers (DNS) or different gadgets on the Net to create enormous site visitors floods.
Ideally, DNS servers solely present companies to machines inside a trusted area — reminiscent of translating an Web tackle from a collection of numbers into a website title, like instance.com. However DNS reflection assaults depend on shopper and enterprise routers and different gadgets outfitted with DNS servers which might be (mis)configured to simply accept queries from anyplace on the Net.
Attackers can ship spoofed DNS queries to those DNS servers, forging the request in order that it seems to come back from the goal’s community. That means, when the DNS servers reply, they reply to the spoofed (goal) tackle.
The dangerous guys can also amplify a reflective assault by crafting DNS queries in order that the responses are a lot greater than the requests. For instance, an attacker may compose a DNS request of lower than 100 bytes, prompting a response that’s 60-70 occasions as massive. This “amplification” impact is very pronounced if the perpetrators question dozens of DNS servers with these spoofed requests concurrently.
The federal government charged that Gatrel and Martinez always scanned the Web for these misconfigured gadgets, after which bought lists of Web addresses tied to those gadgets to different booter service operators.
“Gatrel ran a legal enterprise designed round launching lots of of hundreds of cyber-attacks on behalf of lots of of consumers,” prosecutors wrote in a memorandum submitted prematurely of his sentencing. “He additionally offered infrastructure and assets for different cybercriminals to run their very own companies launching these identical sorts of assaults. These assaults victimized large swaths of American society and compromised computer systems around the globe.”
The U.S. and United Kingdom have been attempting to impress on would-be clients of those booter companies that hiring them for DDoS assaults is prohibited. The U.Ok. has even taken out Google adverts to remind U.Ok. residents after they search on-line for phrases frequent to booter companies.
The case in opposition to Gatrel and Martinez was introduced as a part of a widespread crackdown on booter companies in 2018, when the FBI joined legislation enforcement companions abroad to grab 15 completely different booter service domains.
These actions have prompted a flurry of prosecutions, with wildly various sentences when the booter service homeowners are invariably discovered responsible. Nevertheless, DDoS specialists say booter and stresser companies that stay in operation proceed to account for the overwhelming majority of DDoS assaults launched day by day across the globe.










