Once I was forming the concept for the corporate that will turn into Veza, my co-founders and I interviewed dozens of chief data safety officers (CISOs) and chief data officers (CIOs). Regardless of the dimensions and maturity of their trendy tech-savvy firms, we heard one theme time and again: They may not see who had entry to their firm’s most delicate information. Each one in every of them subscribed to the precept of least privilege, however none of them might say how shut their firm got here to attaining it.
“Least privilege” is outlined by NIST’s Laptop Safety Useful resource Heart as “the precept {that a} safety structure must be designed so that every entity is granted the minimal system sources and authorizations that the entity must carry out its perform.” That sounds easy, however issues have modified. Knowledge is now unfold throughout a number of clouds, tons of of SaaS apps, and techniques previous and new. In consequence, all trendy firms accumulate “entry debt” — pointless permissions that had been both too broad within the first place or now not vital after a job change or termination.
A KPMG research discovered that 62% of US respondents skilled a breach or cyber incident in 2021 alone. If any worker falls prey to phishing, however they solely have entry to non-sensitive data, there could also be no financial impression in any respect. Least privilege mitigates the harm of an assault.
There are three obstacles to attaining least privilege: visibility, scale, and metrics.
Visibility Is the Basis
It is laborious to handle one thing you possibly can’t see, and entry permissions are unfold throughout numerous techniques within the enterprise. Many are managed regionally throughout the distinctive entry controls of a system (e.g., Salesforce admin permissions). Even when firms implement an identification supplier, comparable to Okta, Ping, or ForgeRock, this solely exhibits the tip of the iceberg. It can not present all of the permissions that sit beneath the waterline, together with native accounts and repair accounts.
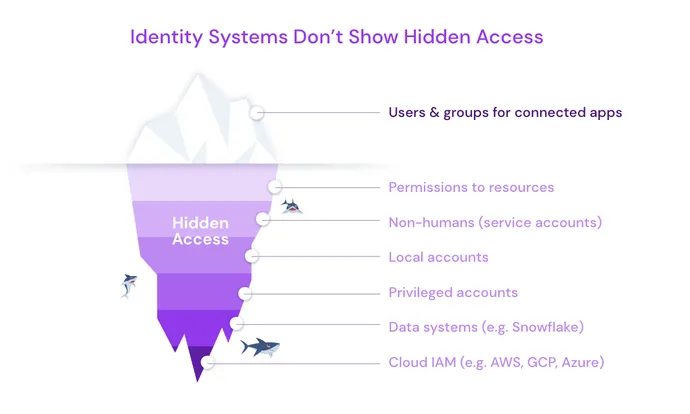
That is particularly related right now, with so many firms conducting layoffs. When terminating staff, employers revoke entry to the community and SSO (single sign-on), however this doesn’t propagate all the best way to the myriad techniques wherein the worker had entitlements. This turns into unseen entry debt.
For firms the place authorized compliance mandates periodic entry critiques, visibility is guide, tedious, and susceptible to omissions. Workers are dispatched to research particular person techniques by hand. Making sense of those experiences (typically, screenshots) is perhaps attainable for a small firm, however not for one with a contemporary information surroundings.
Scale
Any firm may need 1000’s of identities for workers, plus 1000’s extra for non-humans, like service accounts and bots. There could be tons of of “techniques,” together with cloud providers, SaaS apps, customized apps, and information techniques comparable to SQL Server and Snowflake. Every provides tens or tons of of attainable permissions on any variety of granular information sources. Since there’s an entry resolution to make for each attainable mixture of those, it is easy to think about the problem of checking 1,000,000 selections.
To make the most effective of a nasty state of affairs, firms take a shortcut and assign identities to roles and teams. This addresses the dimensions downside however worsens the visibility downside. The safety workforce would possibly have the ability to see who belongs to a bunch, and so they know the label on that group, however labels do not inform the entire story. The workforce cannot see entry on the degree of tables or columns. When identification entry administration (IAM) groups are receiving a unending stream of entry requests, it is tempting to rubber stamp approvals for the closest-fit group, even when that group confers broader entry than vital.
Firms cannot overcome the dimensions problem with out automation. One resolution is time-limited entry. For instance, if an worker was given entry to a bunch however does not use 90% of the permissions for 60 days, it is in all probability a good suggestion to trim that entry.
Metrics
If you cannot measure it, you possibly can’t handle it, and no person right now has the instruments to quantify how a lot “privilege” has been granted.
CISOs and their safety groups want a dashboard to handle least privilege. Simply as Salesforce gave gross sales groups the item mannequin and dashboards to handle income, new firms are creating the identical basis for managing entry.
How will groups quantify their entry? Will or not it’s known as “privilege factors”? Whole permission rating? A 2017 paper coined a metric for database publicity known as “breach danger magnitude.” No matter we name it, the rise of this metric shall be a watershed second in identity-first safety. Even when the metric is an imperfect one, it is going to shift an organization’s mindset towards managing least privilege like a enterprise course of.
Going Ahead
The panorama has modified, and it has turn into virtually not possible to realize least privilege utilizing guide strategies. Fixing this may require new applied sciences, processes, and mindsets. The CISOs and CIOs I work with consider least privilege is feasible, and so they’re making prudent investments to maneuver past the naked minimal of quarterly entry critiques. It will not be lengthy earlier than guide critiques are a factor of the previous, and automation tames the complexity of recent entry management.