InfraGard, a program run by the U.S. Federal Bureau of Investigation (FBI) to construct cyber and bodily menace data sharing partnerships with the personal sector, this week noticed its database of contact data on greater than 80,000 members go up on the market on an English-language cybercrime discussion board. In the meantime, the hackers accountable are speaking instantly with members by means of the InfraGard portal on-line — utilizing a brand new account beneath the assumed identification of a monetary trade CEO that was vetted by the FBI itself.
On Dec. 10, 2022, the comparatively new cybercrime discussion board Breached featured a bombshell new gross sales thread: The person database for InfraGard, together with names and phone data for tens of 1000’s of InfraGard members.
The FBI’s InfraGard program is meant to be a vetted Who’s Who of key folks in personal sector roles involving each cyber and bodily safety at corporations that handle a lot of the nation’s essential infrastructures — together with ingesting water and energy utilities, communications and monetary companies companies, transportation and manufacturing corporations, healthcare suppliers, and nuclear vitality companies.
“InfraGard connects essential infrastructure homeowners, operators, and stakeholders with the FBI to supply training, networking, and information-sharing on safety threats and dangers,” the FBI’s InfraGard reality sheet reads.
KrebsOnSecurity contacted the vendor of the InfraGard database, a Breached discussion board member who makes use of the deal with “USDoD” and whose avatar is the seal of the U.S. Division of Protection.
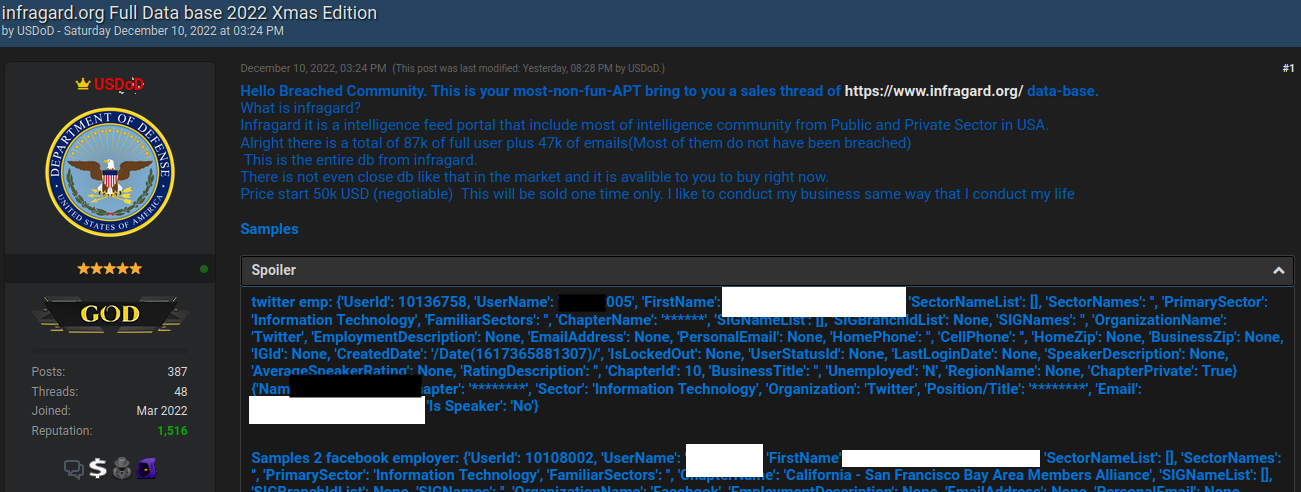
USDoD’s InfraGard gross sales thread on Breached.
USDoD stated they gained entry to the FBI’s InfraGard system by making use of for a brand new account utilizing the title, Social Safety Quantity, date of beginning and different private particulars of a chief govt officer at an organization that was extremely more likely to be granted InfraGard membership.
The CEO in query — at the moment the top of a significant U.S. monetary company that has a direct influence on the creditworthiness of most Individuals — didn’t reply to requests for remark.
USDoD advised KrebsOnSecurity their phony software was submitted in November within the CEO’s title, and that the applying included a contact electronic mail tackle that they managed — but in addition the CEO’s actual cell phone quantity.
“While you register they stated that to be accredited can take a minimum of three months,” USDoD stated. “I wasn’t anticipated to be approve[d].”
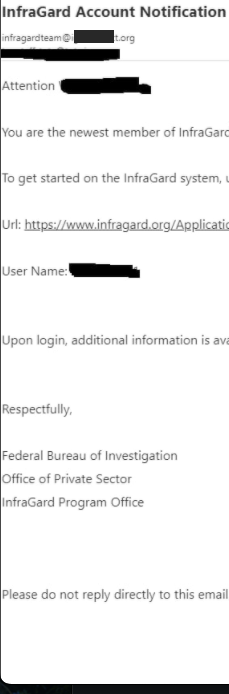 However USDoD stated that in early December, their electronic mail tackle within the title of the CEO obtained a reply saying the applying had been accredited (see redacted screenshot to the best). Whereas the FBI’s InfraGard system requires multi-factor authentication by default, customers can select between receiving a one-time code through SMS or electronic mail.
However USDoD stated that in early December, their electronic mail tackle within the title of the CEO obtained a reply saying the applying had been accredited (see redacted screenshot to the best). Whereas the FBI’s InfraGard system requires multi-factor authentication by default, customers can select between receiving a one-time code through SMS or electronic mail.
“If it was solely the cellphone I will likely be in [a] unhealthy scenario,” USDoD stated. “As a result of I used the particular person[‘s] cellphone that I’m impersonating.”
USDoD stated the InfraGard person knowledge was made simply obtainable through an Software Programming Interface (API) that’s constructed into a number of key elements of the web site that assist InfraGard members join and talk with one another.
USDoD stated after their InfraGard membership was accredited, they requested a buddy to code a script in Python to question that API and retrieve all obtainable InfraGard person knowledge.
“InfraGard is a social media intelligence hub for top profile individuals,” USDoD stated. “They even bought [a] discussion board to debate issues.”
KrebsOnSecurity shared with the FBI a number of screenshots and different knowledge that will assist isolate the imposter InfraGard account, however the company declined to remark for this story.
To show they nonetheless had entry to InfraGard as of publication time Tuesday night, USDoD despatched a direct word by means of InfraGard’s messaging system to an InfraGard member whose private particulars had been initially printed as a teaser on the database gross sales thread.
That InfraGard member, who’s head of safety at a significant U.S. know-how agency, confirmed receipt of USDoD’s message however requested to stay nameless for this story.
USDoD acknowledged that their $50,000 asking value for the InfraGard database could also be a tad excessive, on condition that it’s a pretty fundamental listing of people who find themselves already very security-conscious. Additionally, solely about half of the person accounts comprise an electronic mail tackle, and a lot of the different database fields — like Social Safety Quantity and Date of Beginning — are fully empty.
“I don’t suppose somebody can pay that value, however I’ve to [price it] a bit greater to [negotiate] the value that I need,” they defined.
Whereas the info uncovered by the infiltration at InfraGard could also be minimal, the person knowledge may not have been the true finish sport for the intruders.
USDoD stated they had been hoping the imposter account would final lengthy sufficient for them to complete sending direct messages because the CEO to different executives utilizing the InfraGuard messaging portal. USDoD shared the next redacted screenshot from what they claimed was one such message, though they offered no extra context about it.
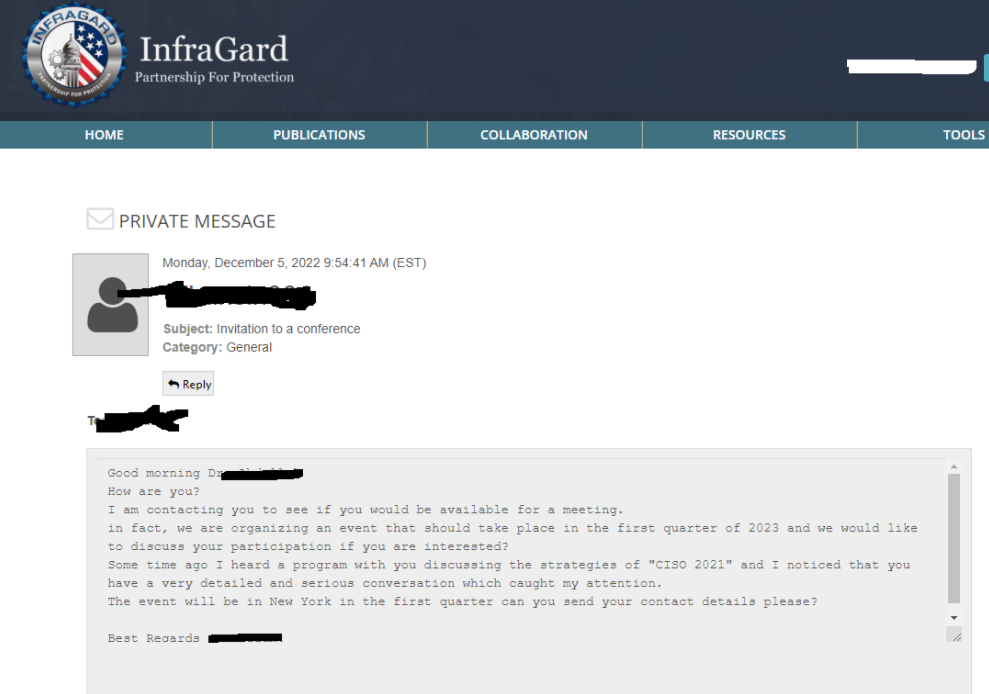
A screenshot shared by USDoD displaying a message thread within the FBI’s InfraGard system.
USDoD stated of their gross sales thread that the guarantor for the transaction can be Pompompurin, the administrator of the cybercrime discussion board Breached. By buying the database by means of the discussion board administrator’s escrow service, would-be consumers can theoretically keep away from getting ripped off and make sure the transaction will likely be consummated to the satisfaction of each events earlier than cash exchanges fingers.
Pompompurin has been a thorn within the aspect of the FBI for years. Their Breached discussion board is extensively thought of to be the second incarnation of RaidForums, a remarkably comparable English-language cybercrime discussion board shuttered by the U.S. Division of Justice in April. Previous to its infiltration by the FBI, RaidForums offered entry to greater than 10 billion client information stolen in among the world’s largest knowledge breaches.
In November 2021, KrebsOnSecurity detailed how Pompompurin abused a vulnerability in an FBI on-line portal designed to share data with state and native legislation enforcement authorities, and the way that entry was used to blast out 1000’s of hoax electronic mail messages — all despatched from an FBI electronic mail and Web tackle.
This can be a creating story. Updates will likely be famous right here with timestamps.