Microsoft on Tuesday launched patches for 33 vulnerabilities, together with 24 for Home windows. 5 different product teams are additionally affected. Of the CVEs addressed, simply 4 are thought-about Crucial in severity – at the least by Microsoft. (Extra on that in a second.) Three of Microsoft’s Crucial-severity patches have an effect on Home windows, whereas the opposite one impacts each Azure and Microsoft Energy Platform Connector. (Connectors are proxies or wrappers round APIs that permit the underlying companies to attach to one another; Microsoft has a really massive ecosystem of those integration instruments.)
At patch time, not one of the points are recognized to be beneath exploit within the wild, and none have been publicly disclosed. Nonetheless, totally a 3rd of the addressed vulnerabilities in Home windows and Defender – 11 CVEs — are by the corporate’s estimation extra more likely to be exploited within the subsequent 30 days.
Along with these CVEs, Microsoft lists one official advisory, ADV990001, which covers their newest servicing stack updates. Nonetheless, Edge-related points, which aren’t tallied within the official rely, make a robust exhibiting this month with 9 CVEs. Seven of these, together with 5 coming to Edge by way of the Chromium challenge, had been launched on December 7. Of the opposite two launched immediately, one elevation-of-privilege vulnerability (CVE-2023-35618) has the peculiar high quality of being a mere moderate-severity difficulty in Microsoft’s estimation, however price a critical-class 9.6 CVSS base rating. The problem requires a sandbox escape to perform, and Microsoft assesses it as much less more likely to be exploited throughout the subsequent 30 days, however we do suggest holding Edge and different Chromium-based browsers updated.
We don’t embrace Edge points within the CVE counts and graphics beneath, however we’ll present data on every little thing in an appendix on the finish of the article. We’re as ordinary together with on the finish of this put up three different appendices itemizing all Microsoft’s patches, sorted by severity, by predicted exploitability, and by product household.
By the numbers
- Whole Microsoft CVEs: 33
- Whole Microsoft advisories transport in replace: 1
- Whole Edge / Chromium points lined in replace: 9
- Publicly disclosed: 0
- Exploited: 0
-
- Severity:
- Crucial: 4
- Necessary: 29
-
- Affect:
- Elevation of Privilege: 10
- Distant Code Execution: 8
- Denial of Service: 5
- Info Disclosure: 5
- Spoofing: 5
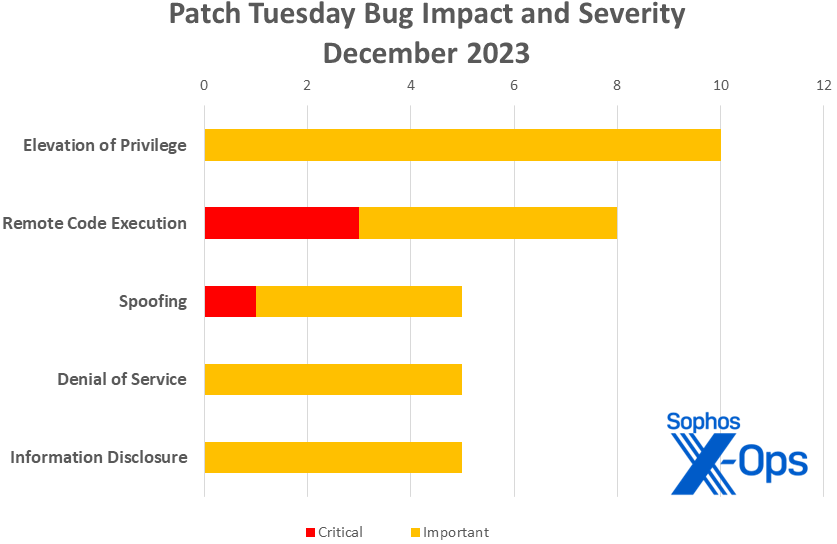
Determine 1: One thing you don’t see each month: A Crucial-class spoofing bug
Merchandise
- Home windows: 24
- Workplace: 3
- Azure: 3 (together with one shared with Energy Platform)
- Dynamics 365: 2
- Defender: 1
- Energy Platform: 1 (shared with Azure)
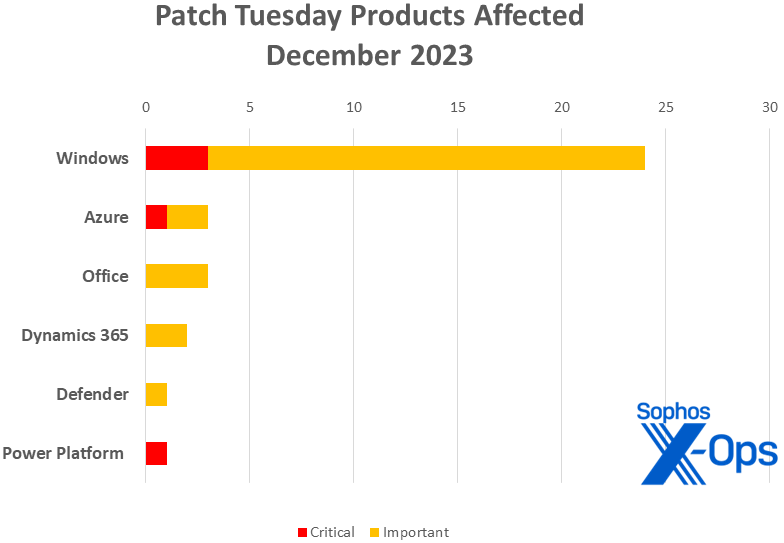
Determine 2: As ordinary, Home windows CVEs are the majority of the gathering in December. The Crucial-class vulnerability seen in each Azure and Energy Platform is identical CVE, affecting each product households
Notable December updates
Along with the problems mentioned above, just a few attention-grabbing gadgets current themselves.
CVE-2023-36019 — Microsoft Energy Platform Connector Spoofing Vulnerability
A Crucial-severity spoofing difficulty? Sure, and one in want of your immediate consideration – for those who haven’t already given it that. Connectors are essential behind-the-scenes performance for each Energy Platform and Azure, and this difficulty is critical sufficient that Microsoft has already notified affected clients about obligatory protecting actions beginning final month. (If this doesn’t ring a bell, you won’t have a world administrator position or a Message heart privateness reader position; for Logic Apps buyer, a notification was despatched by way of Service Well being within the Azure Portal beneath monitoring ID 3_SH-LTG.) To use this, an attacker would ship a malicious hyperlink, or they might manipulate a hyperlink, file, or utility to disguise it as a respectable and reliable one. Microsoft has additionally printed additional data on mitigations and upcoming adjustments to authentication for buyer connectors.
CVE-2023-35628 — Home windows MSHTML Platform Distant Code Execution Vulnerability
The dangerous information is that this Crucial-severity RCE may in some eventualities result in a drive-by exploit, executing on the sufferer’s machine earlier than the sufferer even views a malicious e-mail in Preview Pane, not to mention truly opens it. The excellent news is that in keeping with Microsoft, this vulnerability depends on some advanced memory-shaping methods to work. That stated, it impacts each client- and server-side working methods from Home windows 10 and Home windows Server 2012 R2 ahead, and Microsoft believes it’s one of many 11 extra more likely to be exploited throughout the subsequent 30 days. Finest to not delay.
CVE-2023-35619 — Microsoft Outlook for Mac Spoofing Vulnerability
CVE-2023-36009 — Microsoft Phrase Info Disclosure Vulnerability
Pleased holidays, Apple folks! Microsoft Workplace LTSC for Mac 2021 takes two Necessary-severity patches this month.
CVE-2023-35638 — DHCP Server Service Denial of Service Vulnerability
CVE-2023-35643 — DHCP Server Service Info Disclosure Vulnerability
CVE-2023-36012 — DHCP Server Service Info Disclosure Vulnerability
The 30-year-old Dynamic Host Configuration Protocol takes three Necessary-severity patches this month, none of which cowl the DHCP-centric PoolParty process-injection approach demonstrated at this month’s BlackHat EU.
System directors are reminded that it’s nonetheless, total, a gradual month after a busy yr of Trade patches. If potential, this can be a good time to compensate for your Trade patch state of affairs earlier than the 2024 cycle begins.
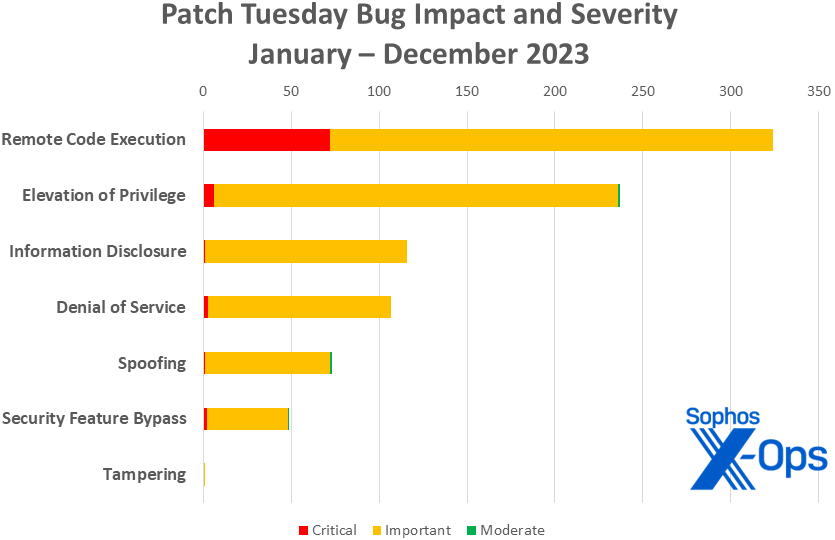
Determine 3: And because the yr rolls to an in depth, distant code execution points cement their place on the high of the 2023 charts
Sophos protections
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2023-35631 | Exp/2335631-A | Exp/2335631-A |
| CVE-2023-35632 | Exp/2335632-A | Exp/2335632-A |
| CVE-2023-35644 | Exp/2335644-A | Exp/2335644-A |
| CVE-2023-36005 | Exp/2336005-A | Exp/2336005-A |
| CVE-2023-36391 | Exp/2336391-A | Exp/2336391-A |
| CVE-2023-36696 | Exp/2336696-A | Exp/2336696-A |
As you possibly can each month, for those who don’t need to wait on your system to drag down Microsoft’s updates itself, you possibly can obtain them manually from the Home windows Replace Catalog web site. Run the winver.exe software to find out which construct of Home windows 10 or 11 you’re operating, then obtain the Cumulative Replace package deal on your particular system’s structure and construct quantity.
Appendix A: Vulnerability Affect and Severity
It is a listing of December’s patches sorted by impression, then sub-sorted by severity. Every listing is additional organized by CVE.
Elevation of Privilege (10 CVEs)
| Necessary severity | |
| CVE-2023-35624 | Azure Linked Machine Agent Elevation of Privilege Vulnerability |
| CVE-2023-35631 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-35632 | Home windows Ancillary Perform Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2023-35633 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-35644 | Home windows Sysmain Service Elevation of Privilege |
| CVE-2023-36003 | XAML Diagnostics Elevation of Privilege Vulnerability |
| CVE-2023-36005 | Home windows Telephony Server Elevation of Privilege Vulnerability |
| CVE-2023-36011 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-36391 | Native Safety Authority Subsystem Service Elevation of Privilege Vulnerability |
| CVE-2023-36696 | Home windows Cloud Recordsdata Mini Filter Driver Elevation of Privilege Vulnerability |
Distant Code Execution (8 CVEs)
| Crucial severity | |
| CVE-2023-35628 | Home windows MSHTML Platform Distant Code Execution Vulnerability |
| CVE-2023-35630 | Web Connection Sharing (ICS) Distant Code Execution Vulnerability |
| CVE-2023-35641 | Web Connection Sharing (ICS) Distant Code Execution Vulnerability |
| Necessary severity | |
| CVE-2023-21740 | Home windows Media Distant Code Execution Vulnerability |
| CVE-2023-35629 | Microsoft USBHUB 3.0 Machine Driver Distant Code Execution Vulnerability |
| CVE-2023-35634 | Home windows Bluetooth Driver Distant Code Execution Vulnerability |
| CVE-2023-35639 | Microsoft ODBC Driver Distant Code Execution Vulnerability |
| CVE-2023-36006 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
Spoofing (5 CVEs)
| Crucial severity | |
| CVE-2023-36019 | Microsoft Energy Platform Connector Spoofing Vulnerability |
| Necessary severity | |
| CVE-2023-35619 | Microsoft Outlook for Mac Spoofing Vulnerability |
| CVE-2023-35622 | Home windows DNS Spoofing Vulnerability |
| CVE-2023-36004 | Home windows DPAPI (Information Safety Software Programming Interface) Spoofing Vulnerability |
| CVE-2023-36020 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability |
Denial of Service (5 CVEs)
| Necessary severity | |
| CVE-2023-35621 | Microsoft Dynamics 365 Finance and Operations Denial of Service Vulnerability |
| CVE-2023-35635 | Home windows Kernel Denial of Service Vulnerability |
| CVE-2023-35638 | DHCP Server Service Denial of Service Vulnerability |
| CVE-2023-35642 | Web Connection Sharing (ICS) Denial of Service Vulnerability |
| CVE-2023-36010 | Microsoft Defender Denial of Service Vulnerability |
Info Disclosure (5 CVEs)
| Necessary severity | |
| CVE-2023-35625 | Azure Machine Studying Compute Occasion for SDK Customers Info Disclosure Vulnerability |
| CVE-2023-35636 | Microsoft Outlook Info Disclosure Vulnerability |
| CVE-2023-35643 | DHCP Server Service Info Disclosure Vulnerability |
| CVE-2023-36009 | Microsoft Phrase Info Disclosure Vulnerability |
| CVE-2023-36012 | DHCP Server Service Info Disclosure Vulnerability |
Appendix B: Exploitability
It is a listing of the December CVEs judged by Microsoft to be extra more likely to be exploited within the wild throughout the first 30 days post-release. Every listing is additional organized by CVE. No CVEs addressed within the December patch assortment are recognized to be beneath lively exploit within the wild but.
| Exploitation extra probably inside 30 days | |
| CVE-2023-35628 | Home windows MSHTML Platform Distant Code Execution Vulnerability |
| CVE-2023-35631 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-35632 | Home windows Ancillary Perform Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2023-35633 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-35641 | Web Connection Sharing (ICS) Distant Code Execution Vulnerability |
| CVE-2023-35644 | Home windows Sysmain Service Elevation of Privilege |
| CVE-2023-36005 | Home windows Telephony Server Elevation of Privilege Vulnerability |
| CVE-2023-36010 | Microsoft Defender Denial of Service Vulnerability |
| CVE-2023-36011 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-36391 | Native Safety Authority Subsystem Service Elevation of Privilege Vulnerability |
| CVE-2023-36696 | Home windows Cloud Recordsdata Mini Filter Driver Elevation of Privilege Vulnerability |
Appendix C: Merchandise Affected
It is a listing of December’s patches sorted by product household, then sub-sorted by severity. Every listing is additional organized by CVE. Patches which might be shared amongst a number of product households are listed a number of occasions, as soon as for every product household.
Home windows (24 CVEs)
| Crucial severity | |
| CVE-2023-35628 | Home windows MSHTML Platform Distant Code Execution Vulnerability |
| CVE-2023-35630 | Web Connection Sharing (ICS) Distant Code Execution Vulnerability |
| CVE-2023-35641 | Web Connection Sharing (ICS) Distant Code Execution Vulnerability |
| Necessary severity | |
| CVE-2023-21740 | Home windows Media Distant Code Execution Vulnerability |
| CVE-2023-35622 | Home windows DNS Spoofing Vulnerability |
| CVE-2023-35629 | Microsoft USBHUB 3.0 Machine Driver Distant Code Execution Vulnerability |
| CVE-2023-35631 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-35632 | Home windows Ancillary Perform Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2023-35633 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-35634 | Home windows Bluetooth Driver Distant Code Execution Vulnerability |
| CVE-2023-35635 | Home windows Kernel Denial of Service Vulnerability |
| CVE-2023-35638 | DHCP Server Service Denial of Service Vulnerability |
| CVE-2023-35639 | Microsoft ODBC Driver Distant Code Execution Vulnerability |
| CVE-2023-35642 | Web Connection Sharing (ICS) Denial of Service Vulnerability |
| CVE-2023-35643 | DHCP Server Service Info Disclosure Vulnerability |
| CVE-2023-35644 | Home windows Sysmain Service Elevation of Privilege |
| CVE-2023-36003 | XAML Diagnostics Elevation of Privilege Vulnerability |
| CVE-2023-36004 | Home windows DPAPI (Information Safety Software Programming Interface) Spoofing Vulnerability |
| CVE-2023-36005 | Home windows Telephony Server Elevation of Privilege Vulnerability |
| CVE-2023-36006 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2023-36011 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-36012 | DHCP Server Service Info Disclosure Vulnerability |
| CVE-2023-36391 | Native Safety Authority Subsystem Service Elevation of Privilege Vulnerability |
| CVE-2023-36696 | Home windows Cloud Recordsdata Mini Filter Driver Elevation of Privilege Vulnerability |
Azure (3 CVEs)
| Crucial severity | |
| CVE-2023-36019 | Microsoft Energy Platform Connector Spoofing Vulnerability |
| Necessary severity | |
| CVE-2023-35624 | Azure Linked Machine Agent Elevation of Privilege Vulnerability |
| CVE-2023-35625 | Azure Machine Studying Compute Occasion for SDK Customers Info Disclosure Vulnerability |
Workplace (3 CVEs)
| Necessary severity | |
| CVE-2023-35619 | Microsoft Outlook for Mac Spoofing Vulnerability |
| CVE-2023-35636 | Microsoft Outlook Info Disclosure Vulnerability |
| CVE-2023-36009 | Microsoft Phrase Info Disclosure Vulnerability |
Dynamics 365 (2 CVEs)
| Necessary severity | |
| CVE-2023-35621 | Microsoft Dynamics 365 Finance and Operations Denial of Service Vulnerability |
| CVE-2023-36020 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability |
Defender (1 CVE)
| Necessary severity | |
| CVE-2023-36010 | Microsoft Defender Denial of Service Vulnerability |
Energy Platform (1 CVE)
| Necessary severity | |
| CVE-2023-36019 | Microsoft Energy Platform Connector Spoofing Vulnerability |
Appendix D: Advisories and Different Merchandise
It is a listing of advisories and knowledge on different related CVEs within the December Microsoft launch, sorted by product.
Microsoft Servicing Stack Updates
| ADV990001 | Newest Servicing Stack Updates |
Related to Edge / Chromium (9 CVEs)
| CVE-2033-6508 | Chromium: CVE-2023-6508 Use after free in Media Stream |
| CVE-2023-6509 | Chromium: CVE-2023-6509 Use after free in Aspect Panel Search |
| CVE-2023-6510 | Chromium: CVE-2023-6510 Use after free in Media Seize |
| CVE-2023-6511 | Chromium: CVE-2023-6511 Inappropriate implementation in Autofill |
| CVE-2023-6512 | Chromium: CVE-2023-6512 Inappropriate implementation in Net Browser UI |
| CVE-2023-35618 | Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability |
| CVE-2023-35637 | Microsoft Edge (Chromium-based) Safety Function Bypass Vulnerability |
| CVE-2023-36880 | Microsoft Edge (Chromium-based) Info Disclosure Vulnerability |
| CVE-2023-38174 | Microsoft Edge (Chromium-based) Info Disclosure Vulnerability |










