Over the following 9 months, the most important web internet hosting service for software program growth and collaboration will make all code contributors add one other layer of digital proof to their accounts.

GitHub, utilized by the vast majority of main tech firms, has introduced that it’s rolling out 2FA. Acknowledging provide chain safety dangers, which have been on the rise, the corporate begins a nine-month rollout on Monday, March 13. All builders who contribute code on the platform will finally should undertake the safety protocol, the corporate introduced on Thursday.
SEE: Hiring package: Full stack developer (TechRepublic Premium)
The Microsoft-owned DevOps service mentioned the transfer aligns with the Nationwide Cybersecurity Technique, which, amongst different issues, places the onus and extra safety accountability on software program distributors.
Soar to:
Being a developer doesn’t make you invulnerable
Even builders make errors and might turn into victims of safety breaches. Mike Hanley, chief safety officer and senior vice chairman of engineering at GitHub, wrote in a Could 2022 weblog — which talked about the 2FA plan for the primary time — that compromised accounts can be utilized to steal non-public code or push malicious adjustments to that code.
“This locations not solely the people and organizations related to the compromised accounts in danger, but in addition any customers of the affected code,” he wrote. “The potential for downstream impression to the broader software program ecosystem and provide chain in consequence is substantial.”
SEE: How you can reduce safety dangers: Comply with these greatest practices for fulfillment (TechRepublic Premium)
Completely different 2FA decisions, however biometrics and passkeys trump SMS
GitHub can also be providing a most popular 2FA choice for account login with a sudo immediate, permitting customers to decide on between time-based one-time passwords, SMS, safety keys or GitHub Cellular. Nevertheless, the corporate is urging customers to go along with safety keys and TOTPs, noting that SMS-based 2FA is much less safe.
NIST, which now not recommends 2FA, identified that:
- An out-of-band secret despatched by way of SMS might be obtained by an attacker who has satisfied the cellular operator to redirect the sufferer’s cell phone to the attacker.
- A malicious app on the endpoint can learn an out-of-band secret despatched by way of SMS and the attacker can use the key to authenticate.
“The strongest strategies broadly out there are people who assist the WebAuthn safe authentication normal,” mentioned GitHub in its announcement. “These strategies embrace bodily safety keys in addition to private units that assist applied sciences corresponding to Home windows Hey or Face ID/Contact ID.”
SEE: 1Password is seeking to a password-free future. Right here’s why (TechRepublic)
GitHub mentioned additionally it is testing passkeys, the next-generation credential protocol, as a protection in opposition to exploits like phishing.
“As a result of passkeys are nonetheless a more moderen authentication technique, we’re working to check them internally earlier than we roll them out to prospects,” mentioned a spokesperson. “We imagine they’ll mix ease of use with sturdy and phishing-resistant authentication.”
Newest transfer follows cadence of GitHub safety packages
In a transfer towards closing loopholes to fight risk actors, GitHub expanded its secret scanning program final fall, permitting builders to trace any publicly uncovered secrets and techniques of their public GitHub repository.
And earlier this 12 months, GitHub launched a setup choice for code scanning referred to as “default setup” that lets customers robotically allow code scanning.
“Our 2FA initiative is a part of a platform-wide effort to safe software program growth by bettering account safety,” the corporate mentioned in a launch, noting that developer accounts are social engineering and account takeover targets.
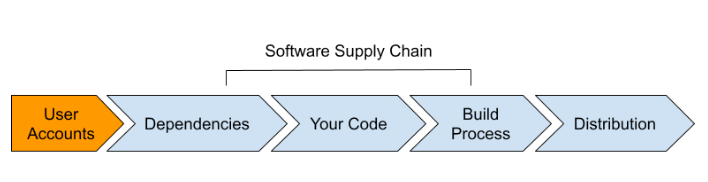
Months-long rollout to reduce disruption, optimize protocols
The method for disseminating the brand new protocols is supposed to reduce disruption to customers, with teams chosen based mostly on the actions they’ve taken or the code they’ve contributed to, in line with GitHub (Determine A).
Determine A
The corporate mentioned the gradual rollout would additionally make it simpler for GitHub to make changes as wanted earlier than scaling to bigger and bigger teams over the course of this 12 months.
A spokesperson for GitHub defined that, whereas the corporate gained’t supply specifics on how customers qualify for being a part of sure teams within the 2FA cadence, the particular person did say teams are decided, partially, based mostly on their impression on the safety of the broader ecosystem. Excessive-impact teams will embrace customers who:
- Revealed GitHub or OAuth apps, Actions or packages.
- Created a launch.
- Contributed code to repositories deemed vital by npm, OpenSSF, PyPI or RubyGems.
- Contributed code to any of the approximate prime 4 million private and non-private repositories.
- Act as enterprise and group directors.
For these with a proactive bent, the corporate is providing 2FA instantly at a devoted web site.
GitHub provides builders 2FA timeline
The method for GitHub contributors units a number of time markers for initiating 2FA round a gentle deadline (Determine B).
Determine B

Earlier than the deadline
GitHub contributors chosen for a pending 2FA group will get advance notification by electronic mail 45 days earlier than the deadline, informing them of the deadline and providing steering on learn how to allow 2FA.
As soon as the enablement deadline passes
These notified will probably be prompted to allow 2FA the primary time they entry GitHub.com every day. They will snooze this immediate as soon as a day for as much as one week, however after that, they are going to be unable to entry GitHub.com options till they permit 2FA.
28 days after 2FA is enabled
Customers will obtain a 2FA “check-up” whereas utilizing GitHub.com, which validates that their 2FA setup is working accurately. Beforehand signed-in customers will have the ability to reconfigure 2FA if they’ve misconfigured or misplaced second elements or restoration codes throughout onboarding.
E mail flexibility to keep away from lockout
Thankfully, the brand new protocols let customers unlink electronic mail from a 2FA-enabled GitHub account to keep away from the paradox of being locked out of the very factor — electronic mail — that permits them to confirm the account in the event that they’re unable to check in or recuperate it.
“For those who’re unable to seek out an SSH key, PAT, or a tool that’s been beforehand signed into GitHub to recuperate your account, it’s simple to start out contemporary with a brand new GitHub.com account and preserve that contribution graph rightfully inexperienced,” mentioned the corporate.