Android infections are additionally prevalent on the darkish internet, in accordance with Kaspersky. Discover ways to preserve your workforce protected from these cellular and BYOD safety threats.

New analysis from Kaspersky focuses on the forms of malicious providers supplied by cybercriminals on the darkish internet, primarily based on the monitoring of pastebin websites and restricted underground on-line cybercrime boards.
The safety researchers discovered that Google Play threats and Android telephone infections are large enterprise. For instance, a Google Play developer account might be purchased for round $60-$200 USD relying on account traits such because the variety of developed apps or the variety of downloads. Bot improvement or hire ranges between $1,000 USD and $20,000 USD.
Soar to:
How might malware be on Google Play?
On Google Play, earlier than an Android app is obtainable to customers, it undergoes a evaluation course of to confirm that it meets sure requirements and adheres to the developer insurance policies, to make sure that it’s not dangerous or malicious.
Nevertheless, there are nonetheless methods for cybercriminals to distribute malicious content material through the platform. One of the vital frequent strategies is to have a benign app authorized on Google Play after which up to date with malicious content material or malware, which could compromise all customers of that software and probably their employers’ networks.
It’s not unusual for customers to convey a private cellular gadget to work, which could retailer company passwords or different info that might assist an attacker compromise the company community.
SEE: Learn the way BYOD and private apps could be a recipe for knowledge breaches.
Moreover, corporations that personal Google Play developer accounts might be focused for provide chain assaults by having a few of their code modified so as to add malware, similar to info stealers.
What are Google Play Loaders?
Google Play Loaders are items of code whose goal is to inject malicious code right into a Google Play software. They’re among the most typical provides on the darkish internet.
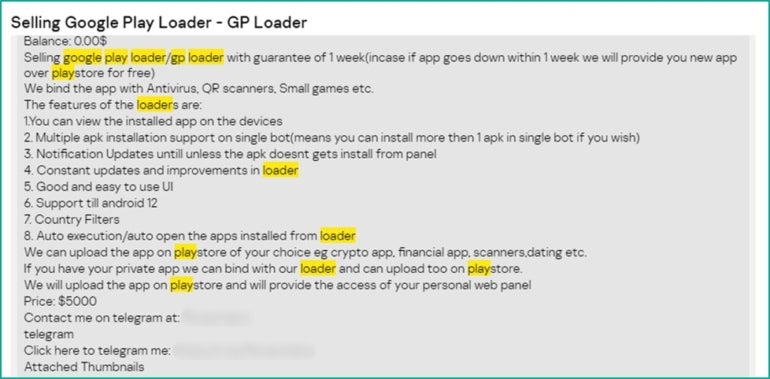
The injected code is then up to date on Google Play. When the sufferer downloads the malicious replace onto their gadget, they might obtain the ultimate payload or a notification asking them to permit set up of unknown apps after which set up it from an exterior supply.
Within the latter situation, the notification persists till the person agrees to put in the extra app. Upon set up, the person is prompted to grant entry to important knowledge similar to Accessibility Companies, the digital camera and microphone. Till these permissions are granted, the sufferer could not have the ability to use the unique legit app.
The sellers often point out the form of legit apps they’ll use for his or her loader and the variety of downloads of the app. These apps are sometimes cryptocurrency trackers, monetary apps, QR-code scanners or courting apps, in accordance with the researchers. Attackers have compromised legit standard apps utilized in company environments similar to a doc scanning app, or used purposes mimicking well-known ones similar to WhatsApp or Telegram.
Loader supply code is obtainable on the market. Kaspersky experiences a loader supply code being auctioned with a beginning worth of $1,500 USD, with bid increments of $200 USD and an prompt buy worth of $7,000 USD.
How does file binding obfuscate malware?
File binding is a method utilized by attackers to mix or merge malicious code with legit recordsdata on any working system, making it more durable for safety options to detect the malware. These recordsdata are sometimes not unfold in Google Play, however through social engineering or web sites distributing cracked video games or software program.
Because the distribution of such purposes is harder than for these supplied via Google Play, the costs are less expensive than for loaders, ranging between $50-$100 USD.
An identical service is the malware obfuscation service, the place the supplier obfuscates a given malware code to bypass safety techniques. This service might be paid on a subscription foundation or for a single file. A file would price round $30 USD, whereas a subscription for 50 recordsdata is about $440 USD.
Prices to extend the an infection fee fluctuate primarily based on nation
Some cybercriminals provide providers to extend an infection fee by growing the app visitors via Google advertisements. Utilizing that approach, the malware comes as the primary Google search end result and is downloaded by unsuspecting victims. Whereas SEO is legit and used to convey as many downloads as doable, it will also be used to unfold fraudulent content material in numerous nations. The prices to extend the an infection fee fluctuate in accordance with the nation, as some nations are extra attention-grabbing for cybercriminals than others.
These prices fluctuate from roughly $0.10 USD to $1 USD, with the U.S. being amongst the most costly at roughly $0.80 USD, together with Canada and Australia. That is adopted by European nations at roughly $0.50 USD and so-called Tier-3 nations at round $0.25 USD.
Android malware for any form of cybercrime
Malware on Android may be used for any form of fraud. All types of malware are offered and acquired on the darkish internet, together with banking trojans and cyberespionage malware.
Attackers fascinated with monetary fraud have a tendency to focus on as many Android gadgets as doable to be able to accumulate knowledge, similar to bank card info. It due to this fact is sensible for them to attempt to get their malware on Google Play to unfold it as a lot as doable.
Focused assaults are totally different as a result of they principally depend on social engineering tips to entice a focused person into putting in a malicious software. As a result of they strategy their victims via e-mail or prompt messaging apps, they want their malware to be extra discreet and infrequently don’t use Google Play for these assaults.
How one can shield from this safety menace
- Use multifactor authentication on your builders’ accounts on software platforms similar to Google Play.
- Monitor the darkish internet for credentials and entry leaks that may allow an attacker to compromise any software constructed by a developer out of your firm.
- Educate workers about cell phone threats. Advise them to by no means obtain any software from any non-official retailer, even when the set up hyperlink appears to originate from the corporate. In the event that they’re not sure an set up hyperlink is legitimate and bonafide, they need to contact IT.
- When putting in an software, customers ought to fastidiously verify the privileges that the applying requests. For instance, a QR Code scanner shouldn’t ask for permission to ship SMS.
- Remind workers to maintain the OS for his or her cellular gadgets updated and patched.
Disclosure: I work for Development Micro, however the views expressed on this article are mine.










