What simply occurred? A authorities assessment of the assault on Microsoft’s Trade On-line hosted e mail service by a China-linked group has blasted the Redmond firm for permitting a “cascade of safety failures” that have been preventable and may by no means have occurred. The report describes Microsoft’s safety tradition as “insufficient” and requiring an overhaul.
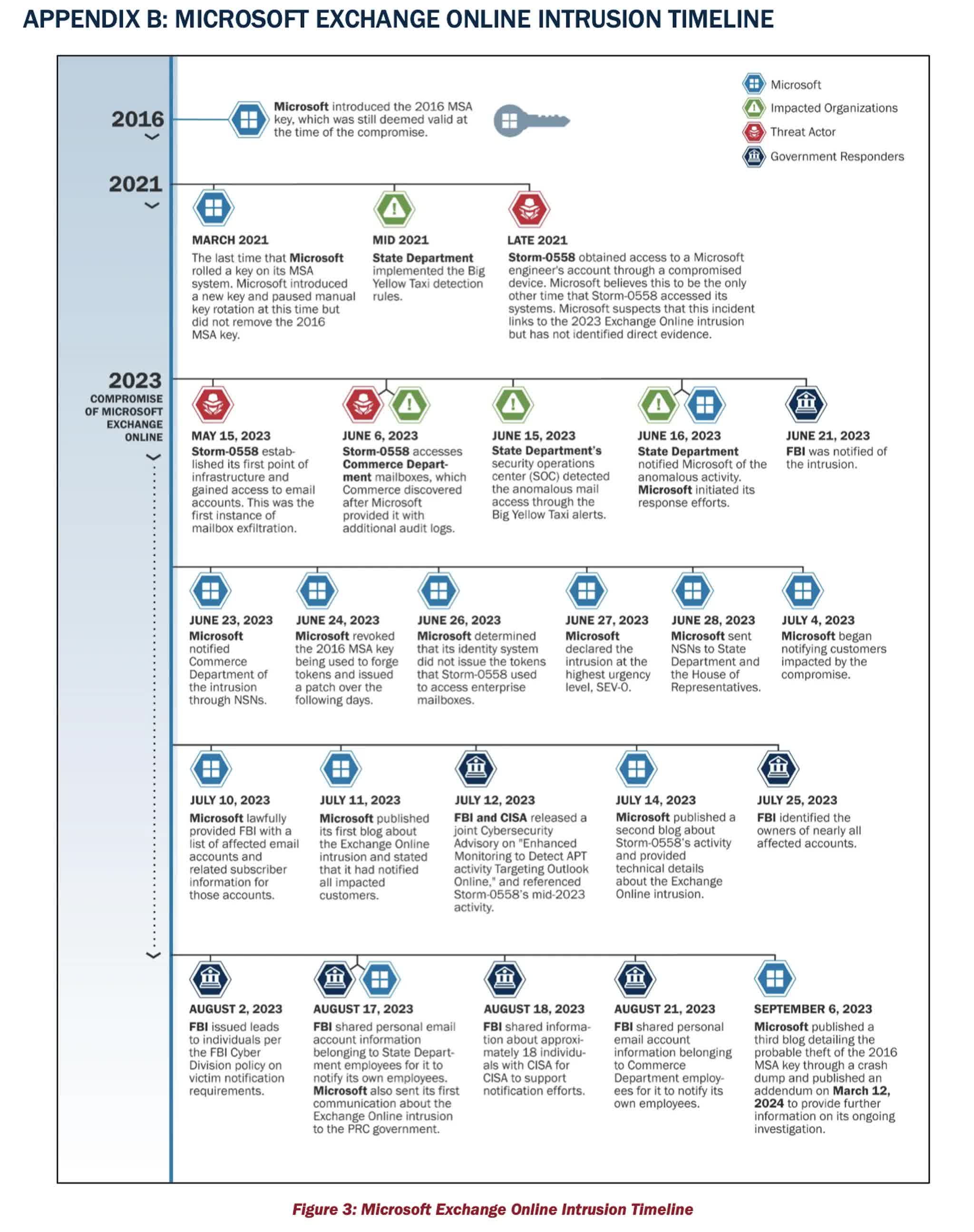
The Trade On-line hack that passed off final Could is believed to have been linked to a China-affiliated risk actor often called Storm-0558 stealing an Azure signing key in late 2021 from an engineer’s compromised laptop computer that got here into Microsoft’s possession after an acquisition.
The hack allowed these accountable entry to the net e mail inboxes of twenty-two organizations, affecting greater than 500 individuals, together with Commerce Secretary Gina Raimondo, US Ambassador to the Individuals’s Republic of China R. Nicholas Burns, Congressman Don Bacon, and Assistant Secretary of State for East Asian and Pacific Affairs Daniel Kritenbrink.
A assessment of the incident carried out by US authorities’s Cybersecurity and Infrastructure Safety Company’s Cyber Security Evaluation Board (CSRB) states that the hack was “preventable” and {that a} sequence of choices by Microsoft fostered “a company tradition that deprioritized enterprise safety investments and rigorous threat administration.”
The assessment provides that Microsoft’s safety tradition requires “an overhaul, significantly in mild of the corporate’s centrality within the know-how ecosystem and the extent of belief prospects place within the firm to guard their knowledge and operations.”
Different suggestions embrace Microsoft’s CEO and board of administrators instantly specializing in safety tradition, and growing and sharing a plan to make security-focused reforms throughout the enterprise. Moreover, firm management ought to take into account directing inside Microsoft groups to deprioritize function developments throughout the corporate’s cloud infrastructure and product suite till substantial safety enhancements have been made.
The report additionally states that there is not particular proof on how the hacker obtained the 2016 Microsoft Companies Account (MSA) signing key, which ought to have been revoked in March 2021.
The Home windows maker was additional criticized for the way lengthy it took to right its preliminary statements relating to the assault. Microsoft stated in September 2023 that the incident was attributable to a cryptographic key being current in a crash dump. Microsoft did not amend that put up till March 12, when it admitted no crash dump containing the important thing had been discovered.
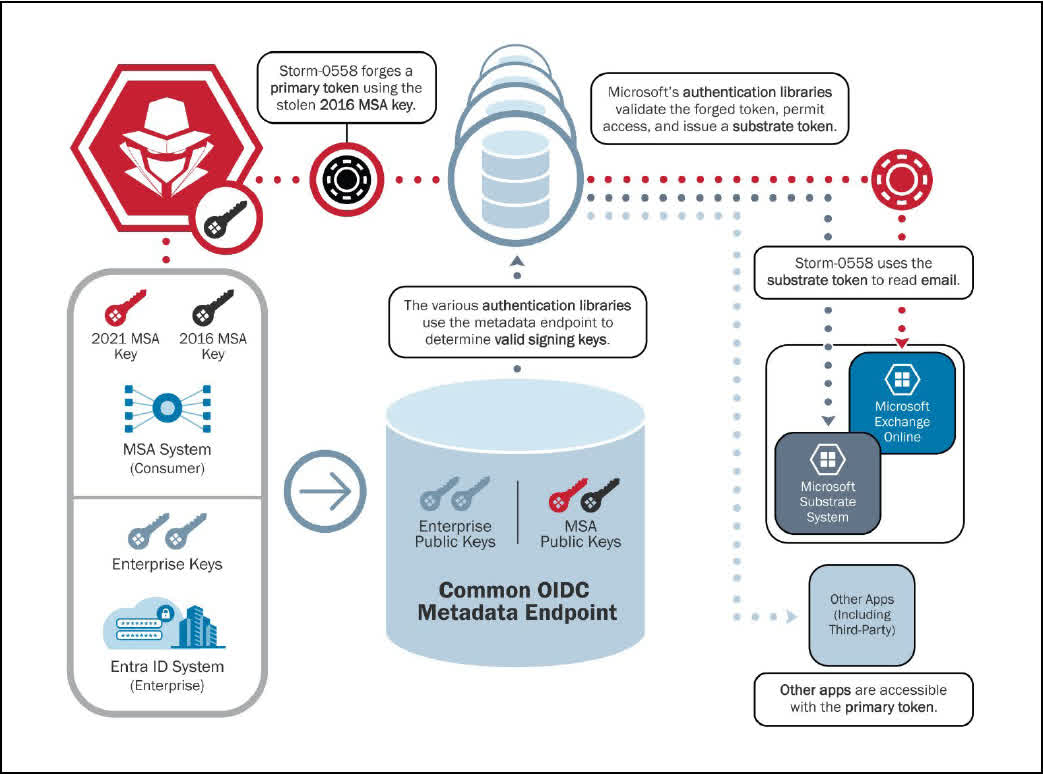
“Our main speculation stays that operational errors resulted in key materials leaving the safe token signing setting that was subsequently accessed in a debugging setting by way of a compromised engineering account,” Microsoft wrote in its up to date put up.
Microsoft has investigated 46 theories as to how the hack passed off, together with the hacker possessing a theoretical quantum computing functionality to interrupt public-key cryptography, and an insider who stole the important thing throughout its creation, none of which it has been capable of show.
Extra unhealthy information for Microsoft got here final week when The US Home of Representatives issued a strict ban on congressional staffers utilizing the corporate’s Copilot generative AI instrument over safety fears










