Why it issues: An email-focused safety agency launched a weblog publish detailing a phishing assault concentrating on unsecured American Categorical and Snapchat websites. The recognized exploit makes use of a recognized open redirect vulnerability that enables risk actors to specify a redirect URL, driving site visitors to fraudulent websites designed to steal consumer info.
Maryland-based safety agency Inky Safety tracked assault exercise associated to the vulnerability from mid-Might via mid-July. The phishing assault depends on a recognized open redirect vulnerability (CWE-601) and fashionable model recognition to deceive and harvest credentials from unsuspecting Google Workspace and Microsoft 365 customers.
The assaults focused unsecured websites from Snapchat and American Categorical. Snapchat-based assaults resulted in additional than 6,800 assaults over a two-and-a-half-month interval. The American Categorical-based assaults had been way more efficient, affecting over 2,000 customers in simply two days.
Malicious actors have taken benefit of open-redirect vulnerabilities affecting AMEX & Snapchat domains to ship #phishing emails concentrating on Google Workspace and Microsoft 365 customers.” https://t.co/bTG2b7dLWY
— INKY (@InkyPhishFence) August 4, 2022
The Snapchat-based emails drove customers to fraudulent DocuSign, FedEx, and Microsoft websites to reap consumer credentials. Snapchat’s open redirect vulnerability was initially recognized by openbugbounty greater than a yr in the past. Sadly, the exploit nonetheless seems to be unaddressed.
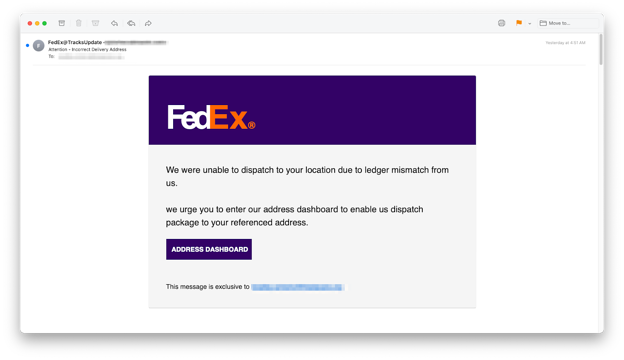
American Categorical seems to have remediated the vulnerability, which redirected customers to an O365 login web page much like the one which the Snapchat-based assaults used.
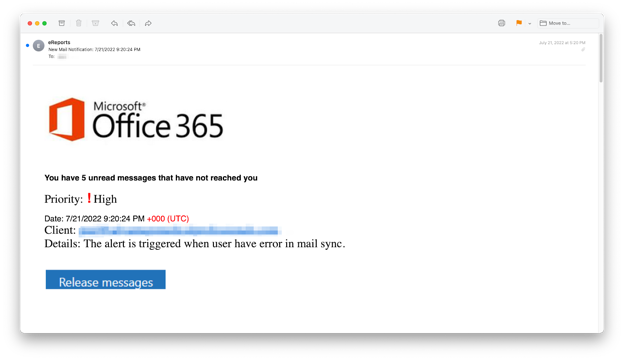
This particular phishing assault makes use of three main strategies: model impersonation, credential harvesting, and hijacked accounts. Model recognition depends on recognizable logos and emblems to create a way of belief with the potential sufferer resulting in the consumer’s credentials being entered into and harvested from the fraudulent web site. As soon as harvested, hackers can promote the stolen info to different criminals for revenue or use the knowledge to entry and procure the sufferer’s private and monetary info.
Open redirect vulnerabilities do not are inclined to get the identical degree of care and a focus as different recognized exploits. Moreover, most threat publicity is on the consumer relatively than the location proprietor. The weblog publish supplies extra background and steering to assist customers keep protected and hold their knowledge out of the improper palms. The following tips assist customers determine key phrases and characters which will point out if a redirect is happening from a trusted area.










