A cybersecurity framework supplies a proper and complete set of pointers to assist organizations outline their safety insurance policies, assess cybersecurity posture, and enhance resilience. Cybersecurity frameworks specify safety controls, threat evaluation strategies, and appropriate safeguards to guard info methods and information from cyberthreats. Although initially developed for presidency businesses and different massive organizations, cybersecurity frameworks can be a helpful supply of safety greatest practices for medium and small companies. With out getting too formal, let’s see what cybersecurity frameworks exist, why chances are you’ll need to use one, and the right way to hand-pick the cybersecurity processes and actions that apply to your particular net software safety program.
Why cybersecurity frameworks exist
Relying on the group, a profitable cyberattack can have severe social, financial, and even political penalties. Whether or not they end in a denial of service, an information breach, or a stealthy and chronic presence in focused methods, cyberattacks are actually a everlasting concern not just for enterprise and authorities however even for navy operations. Properly-defined cybersecurity packages are important for organizations of all sizes, however merely saying “safe all the pieces” isn’t ok, particularly given the complexity of at present’s interconnected info methods and provide chains. And with information safety and privateness excessive on the agenda, a scientific and formalized strategy is critical to establish particular safety controls that hold delicate info inaccessible to malicious actors.
With private and non-private organizations of all sizes dealing with related cybersecurity occasions and challenges, it turned clear {that a} frequent cybersecurity framework would profit everybody. By working to a typical set of best-practice insurance policies and suggestions, everybody would be capable of outline their very own cybersecurity practices and protecting applied sciences whereas sustaining a typical baseline for auditing and certification. And for organizations which will lack the sources or technical sources to design their very own insurance policies from scratch, having such a starter coverage equipment might be the one method to give you a fairly full and efficient cybersecurity coverage.
Generally used cybersecurity frameworks
You’ll be able to consider a cybersecurity framework as a typical field of elements for constructing cybersecurity insurance policies. Extra formally, a cybersecurity framework may be any doc that defines procedures and targets to information extra detailed insurance policies. Present paperwork that include such cybersecurity pointers embody:
- The NIST Cybersecurity Framework: Probably the most extensively used doc for cybersecurity coverage and planning, developed by the Nationwide Institute of Requirements and Expertise.
- ISO 27001 Data Safety Administration: Pointers for info safety administration methods (ISMS) ready by the Worldwide Group for Standardization.
- CIS Vital Safety Controls for Efficient Cyber Protection: A framework of actions to guard organizations from identified cyberthreats, ready by the Middle for Web Safety.
- Threat administration frameworks: Paperwork resembling NIST’s Threat Administration Framework (NIST SP 800-37 Rev. 2) and the ISO 27005:2018 normal for Data Safety Threat Administration deal with threat administration methods, together with cybersecurity threat administration.
- Trade-specific frameworks: Many industries have their very own safety requirements for these sectors, resembling PCI DSS for digital cost processing, HIPAA guidelines for healthcare, or COBIT for IT administration and governance.
A more in-depth have a look at the NIST cybersecurity framework
In 2013, a US presidential government order was issued calling for a standardized cybersecurity framework to explain and construction actions and methodologies associated to cybersecurity. In response to this, NIST developed its Framework for Bettering Vital Infrastructure Cybersecurity, generally known as the NIST Cybersecurity Framework (NIST CSF). It’s a detailed coverage doc created not solely to assist organizations handle and scale back their cybersecurity threat but additionally to create a typical language for speaking about cybersecurity actions. Whereas the framework was initially meant just for corporations managing vital infrastructure providers within the US personal sector, it’s now extensively utilized by private and non-private organizations of all sizes.
The NIST CSF is split into three most important parts:
- Framework core: The principle informational a part of the doc, defining frequent actions and outcomes associated to cybersecurity. All of the core info is organized into features, classes, and subcategories.
- Framework profile: A subset of core classes and subcategories {that a} particular group has chosen to use primarily based on its wants and threat assessments.
- Implementation tiers: A set of coverage implementation ranges, meant to assist organizations in defining and speaking their strategy and the recognized degree of threat for his or her particular enterprise atmosphere.
The framework core supplies a unified construction of cybersecurity administration processes, with the 5 most important features being Determine, Defend, Detect, Reply, and Get well. For every operate, a number of classes and subcategories are then outlined. That is the place organizations can choose and blend to place collectively a set of things for every operate that corresponds to their particular person dangers, necessities, and anticipated outcomes. For readability and brevity, every operate and class has a singular letter identifier, so for instance Asset Administration throughout the Determine operate is denoted as ID.AM, whereas Response Planning throughout the Response operate is RS.RP.
Every class contains subcategories that correspond to particular actions, and these subcategories get numerical identifiers. To provide one other instance, subcategory Detection processes are examined beneath the Detection Processes class and Detect operate is recognized as DE.DP-3. Subcategory definitions are accompanied by references to the related sections of requirements paperwork for fast entry to the normative pointers for every motion.
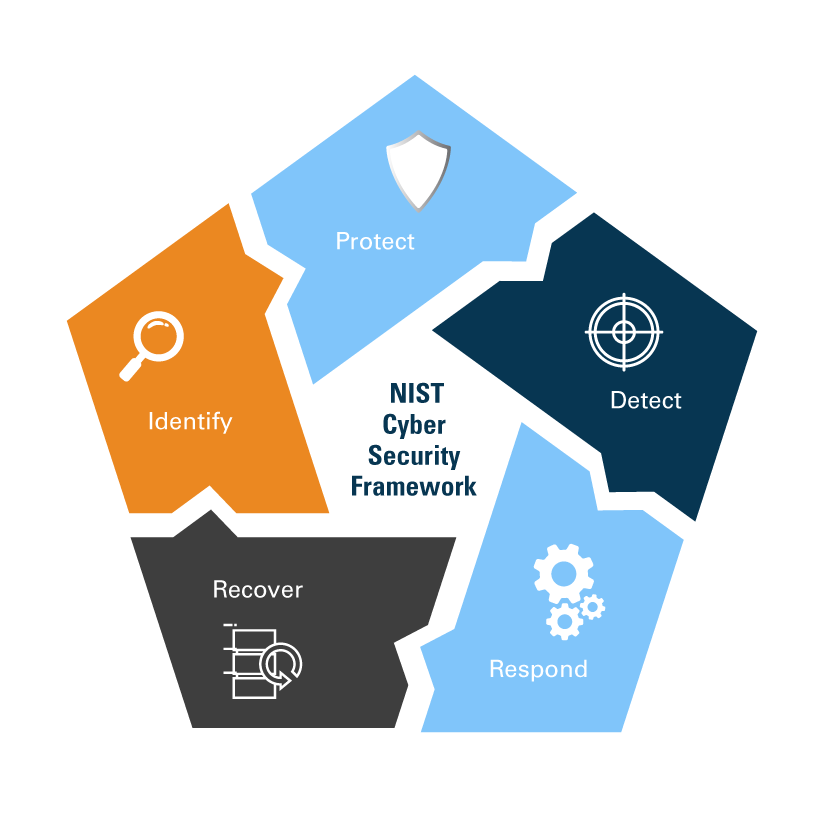
Making use of the NIST framework to software safety
By design, the NIST CSF has a particularly broad scope and covers way more actions than any particular group is prone to want. To use the framework to net software safety, you begin by analyzing every of the 5 features as they relate to your current and deliberate software safety actions and threat administration processes. Then, you choose the classes and subcategories related to your particular wants and use them because the spine of your individual safety coverage to make sure you cowl all of the dangers and actions you want. For normal net software safety, a skeleton cybersecurity coverage would want to incorporate not less than the next subcategories for every operate:
Determine:
- ID.AM-2: Software program platforms and purposes throughout the group are inventoried
- ID.RA-1: Asset vulnerabilities are recognized and documented
Defend:
- PR.AC-4: Entry permissions and authorizations are managed, incorporating the rules of least privilege and separation of duties
- PR.DS-2: Information-in-transit is protected
- PR.IP-10: Incident response and restoration plans are examined
Detect:
- DE.AE-2: Detected occasions are analyzed to grasp assault targets and strategies
- DE.CM-8: Vulnerability scans are carried out
Reply:
- RS.RP-1: Response plan is executed throughout or after an incident
- RS.AN-1: Notifications from detection methods are investigated
Get well:
- RC.RP-1: Restoration plan is executed throughout or after a cybersecurity incident
- RC.CO-3: Restoration actions are communicated to inner and exterior stakeholders in addition to government and administration groups
Abstract
Cybersecurity frameworks present a typical construction for planning, implementation, response, and mitigation. By choosing the related actions (subcategories) for every elementary operate, you possibly can construct customized cybersecurity insurance policies tailor-made to the enterprise and compliance necessities of your group. By combining standards-based insurance policies with enterprise net safety greatest practices and dependable net software safety options, you possibly can decrease threat and preserve a strong cybersecurity posture.










