The Nationwide Institute of Requirements and Know-how (NIST) zero-trust safety framework presents a brand new approach of fixing an age-old downside of securing networks and data, and organizations of all sizes are rethinking their safety structure, processes, and procedures to undertake zero-trust rules.
In keeping with the NIST, “Zero belief (ZT) is the time period for an evolving set of cybersecurity paradigms that transfer defenses from static, network-based perimeters to deal with customers, property, and assets. A zero belief structure (ZTA) makes use of zero belief rules to plan industrial and enterprise infrastructure and workflows. Zero belief assumes there is no such thing as a implicit belief granted to property or person accounts based mostly solely on their bodily or community location or based mostly on asset possession … Zero belief focuses on defending assets, not community segments, because the community location is not seen because the prime element to the safety posture of the useful resource.”
The ZT mannequin is definitely visualized as a set of pillars representing safety areas reminiscent of units, purposes, and customers. However beneath all these pillars are the foundational points of the zero-trust mannequin: visibility, analytics, automation, and governance.
 NETSCOUT
NETSCOUTZT adoption is an incremental and continuous strategy of enhancements and variations. As organizations start and refine their ZTA, their options enhance in reliance on complete visibility and monitoring, automated processes and techniques, and integrating extra totally throughout pillars, turning into extra dynamic of their coverage enforcement choices.
Implementing and growing ZTA takes time, and the structure itself will proceed to evolve as insurance policies, processes, and tooling are improved. However verification and ongoing auditing is essential to figuring out and demonstrating that your safety is certainly working.
In January 2022, the Government Workplace of the President issued Memorandum M-22-09 to offer course and impetus for implementing ZT rules to guard authorities assets. The methods set forth are equally relevant within the personal sector. The memo describes ZT tenets, pillars, and foundations and immediately calls out the necessity for complete visibility.
Necessities from the part on community visibility and assault floor embody the next:
- Monitoring: “Community monitoring towards the chance of weak or compromised community inspection units. Inspecting and analyzing logged community visitors is a crucial tenant of zero-trust structure.”
- Inspection: “Elsewhere, deep visitors inspection could also be extra precious and may create much less of a rise of the assault floor.”
- Evaluation: “Community visitors that isn’t decrypted can and may nonetheless be analyzed utilizing visibility or logged metadata, machine studying strategies, and different heuristics for detecting anomalous exercise.”
In conventional, non-ZT deployments, the monitoring and analytics basis is gathering packets on the community perimeters and sometimes at significantly particular or delicate areas of the interior community as properly.
Because the ZTA matures, perimeters blur or vanish altogether. East-west visitors now have to be seen and managed to detect and stop lateral or deeper compromise. Due to this fact, monitoring visibility have to be prolonged throughout your entire community, each bodily and digital. In a really mature stage of ZT, full visibility and superior analytics and intelligence validate the correctness and enforcement of safety insurance policies.
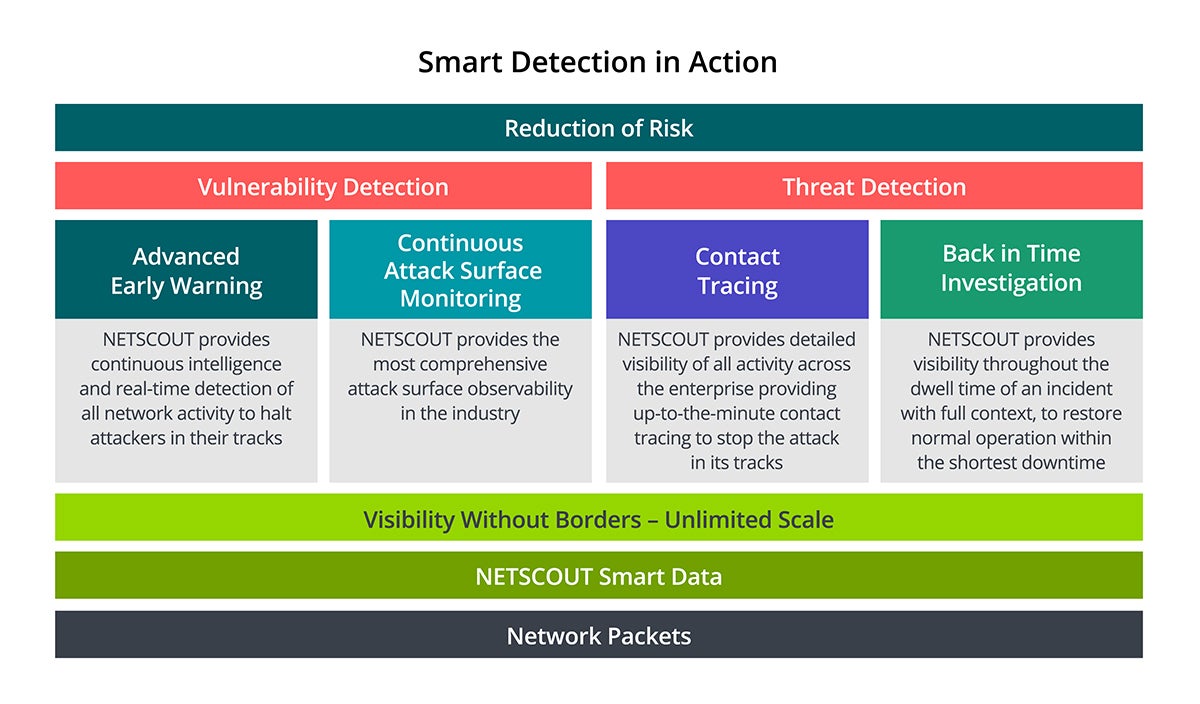
How does NETSCOUT assist with a ZTA? NETSCOUT supplies the great visibility basis with instrumentation specializing in threats and vulnerabilities, permitting for instant detection in addition to back-in-time investigations. Moreover, Omnis Cyber Intelligence (OCI) fills the visibility and information gaps left by different cybersecurity instruments (e.g., safety info and occasion administration and endpoint detection), making these instruments and present cybersecurity workers simpler and lowering the quantity and price of information breaches.
 NETSCOUT
NETSCOUTOCI achieves this by changing packets into Good Information at scale, enabling visibility throughout your entire community (together with hybrid/multicloud environments)—what we name Visibility With out Borders. OCI’s primary featured areas embody the next:
- Superior early warning
- Steady assault floor monitoring
- Contact tracing
- Again-in-time investigation
From bodily and digital community probes in personal and public clouds and enterprise information facilities to menace detection; packet aggregation; and superior packet-capturing options reminiscent of steady, real-time creation of layer 2–7 metadata, indexing, compression, and deduplication, no facet of visibility or menace detection is unseen.
Whether or not your ZT initiative remains to be within the planning section or already very mature, NETSCOUT has the expertise and tooling to offer all points of the safety visibility and analytics basis you want for the lifetime of your group.
Learn extra about methods to enhance safety through a zero-trust structure.
Copyright © 2022 IDG Communications, Inc.










