Passwords have all the time been a ache level in securing computing infrastructure. Complexity and size are key elements of a powerful password, however each make it inherently tough for a human to recollect. Moreover, passwords needs to be modified periodically, nice if you’re working with a handful of units, however when your community is distributed geographically with a whole bunch, or hundreds of computer systems issues get extra complicated. Luckily, Microsoft has had an answer to this drawback within the type of Native Administrator Password Answer (LAPS), although it’s definitely not marketed as closely as different Microsoft options. LAPS is a utility that allows native administrator passwords to be set programmatically primarily based on a supplied schedule utilizing the complexity parameters you outline.
How you can make the perfect use of LAPS preliminary set up
As any skilled Home windows administrator is aware of, most Home windows computer systems in a Microsoft Energetic Listing (AD) area retain accounts which might be native to that laptop to facilitate administrative entry to particular person units in instances the place the area is probably not accessible (community points and even lacking {hardware} drivers are frequent causes). Securing these native accounts turns into a bit difficult. Group Coverage supplies choices to rename the default administrator account on computer systems inside the coverage scope, however managing the password requires a bit extra effort.
At a high-level, putting in and configuring LAPS requires software program set up on a number of administration servers, minor customization of the AD schema, configuration of settings utilizing Group Coverage, and deployment of the add-on to member servers and workstations. We’ll dig into every of those elements a bit extra, and in addition determine a couple of points you may encounter alongside the best way.
Step one in deploying LAPS is putting in the utility on a server that has the Group Coverage administration instruments pre-installed. Moreover, as a part of the LAPS deployment course of includes modifications to the AD schema, I like to recommend you do that set up on a website controller, ideally the area controller which holds the schema grasp position. Throughout this set up you’ll need to set up the entire options underneath the Administration Instruments node (the Fats consumer UI, PowerShell Module, and GPO Editor templates).
The second step is to configure Energetic Listing to have the ability to retailer every laptop’s native administrator password and the expiration date for that password, which requires customizing the AD Schema so as to add these fields. Opening an administrative PowerShell window and executing the Import-Module AdmPwd.PS command adopted by Replace-AdmPwdADSchema ought to lead to an inventory of three actions carried out efficiently. If this step offers you any bother you may want to make sure that your consumer has the suitable Schema Administrator permissions, the Energetic Listing Schema snap-in is registered (regsvr32 schmmgmt.dll), and Energetic Listing replication is wholesome.
 Tim Ferrill
Tim FerrillEnergetic Listing attributes
Third, for computer systems to have the ability to set passwords for his or her native administrator when required and for admins to learn and reset these passwords, there are some permissions that should be configured on the AD organizational items (OUs) that include laptop accounts. Whereas this may very well be completed manually the LAPS set up provides PowerShell cmdlets to assist handle these permissions. The Set-AdmPwdComputerSelfPermission cmdlet can be utilized to configure the permissions on an OU to permit computer systems to retailer the native admin password and observe the date of the change. The Set-AdmPwdReadPasswordPermission and Set-AdmPwdResetPasswordPermission enable the designated teams the power to retrieve or reset the password respectively.
Lastly, Group Coverage settings associated to the LAPS configuration should be set. There are 4 completely different settings underneath Pc Configuration/Insurance policies/Administrative Templates/LAPS which might be simple to configure.
- First is Password Settings, which requires you to determine the varieties of characters that needs to be used for complexity, the size of the passwords to be generated, and the variety of days earlier than password resets happen mechanically.
- The second setting is used to determine the Native Administrator account to handle. This setting is barely used if the account to be managed isn’t the built-in Administrator account and shouldn’t be used to reference the built-in Administrator account even when it’s been renamed.
- Setting quantity three is used to make sure that the LAPS password expiration time doesn’t exceed that of the usual Energetic Listing Password Settings coverage.
- Lastly the Allow native admin password administration setting merely allows LAPS for computer systems inside the scope of the GPO.
 Tim Ferrill
Tim FerrillGPO password settings
LAPS safety ramifications
The largest factor to pay attention to when contemplating utilizing LAPS is the truth that Native Administrator passwords are saved in plain textual content in Energetic Listing. Within the grand scheme of issues this threat is mitigated with permissions to the important thing attributes being restricted. Moreover, the chance of a single Administrator account being compromised is extraordinarily low in comparison with having all of the accounts set to a single password that isn’t modified mechanically.
Energetic Listing forests, which have been round for some time, could have allowed computer systems to be joined to the area by non-administrative accounts. In that case, Pc accounts joined by non-admins could have the msds-CreatorSid attribute set, which grant the customers that created the account further permissions for these Pc objects in AD, together with the power to learn the ms-Mcs-AdmPwd attribute containing the password for the Native Administrator account.
Pc objects with the msds-CreatorSid needs to be recognized and dealt with accordingly, and greatest practices dictate that solely Directors needs to be allowed so as to add new computer systems to the area.
Retrieving and resetting passwords in LAPS
Typically, the one guide interplay admins may have with LAPS will probably be to retrieve an area administrator password for a single laptop. If the LAPS administration elements have been put in that is as straightforward as utilizing the LAPS UI, typing within the laptop identify, and retrieving the password. The LAPS administration elements additionally embrace the Get-AdmPwdPassword PowerShell cmdlet to retrieve passwords.
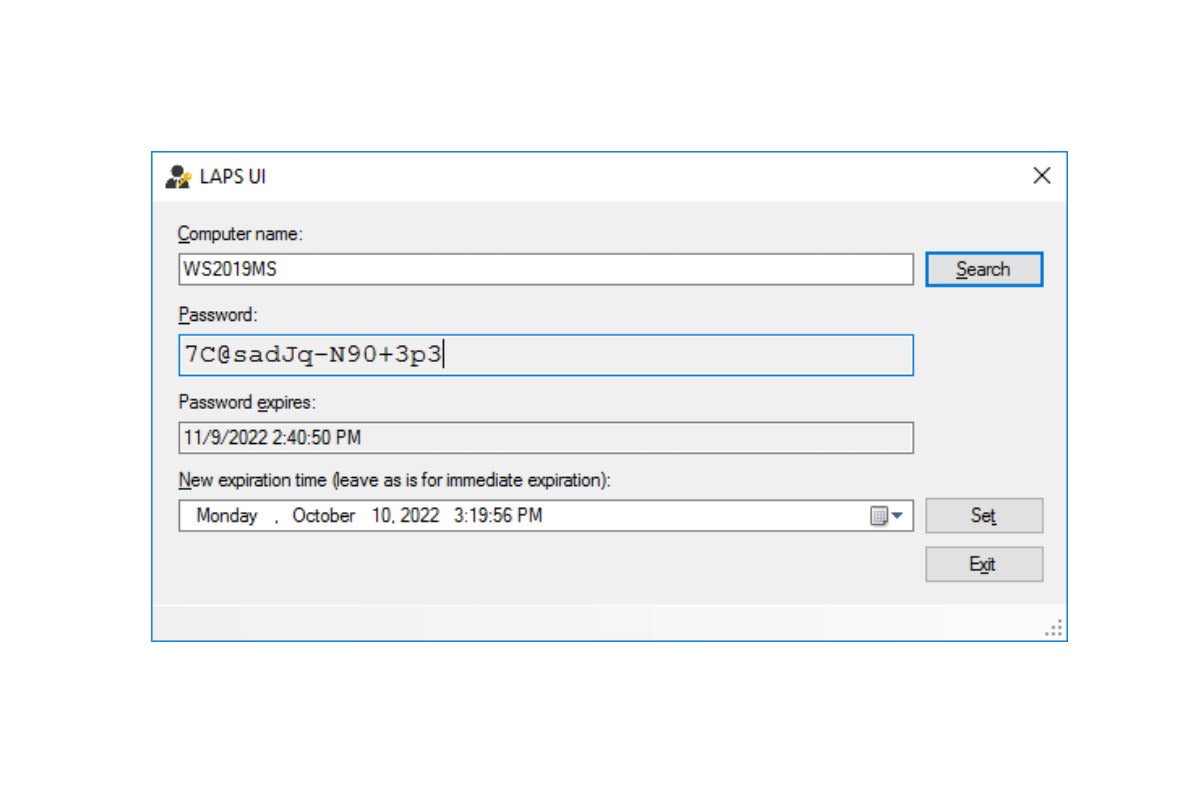 Tim Ferrill
Tim FerrillLAPS consumer interface
Alternatively, customary Energetic Listing administrator instruments comparable to AD customers and computer systems or the Get-ADUser PowerShell cmdlet can every learn the ms-Mcs-AdmPwd attribute, assuming the consumer has the right permissions.
Native administrator passwords for computer systems will be reset utilizing both the LAPS UI or the Reset-AdmPwdPassword cmdlet. These instruments merely set off the LAPS utility to re-generate a random password for the administrator account by updating the expiration to a time previously. The PowerShell utility is especially helpful for resetting administrator passwords in bulk, a perform that needs to be leveraged at any time when a privileged consumer leaves the workforce.
Microsoft additional invests in LAPS
LAPS isn’t a brand new resolution and it has its shortcomings. The excellent news is that Microsoft is actively investing in LAPS for his or her newest working programs as a way to treatment among the weaknesses in legacy LAPS and even leverage trendy applied sciences like Azure AD. Notice that at present trendy LAPS is barely supported on Home windows 11 Insider Preview Construct 25145 and later, and assist for integration with Azure AD is proscribed to pick out Home windows Insider customers, so in the meanwhile it’s not prepared for prime time.
The primary main characteristic trendy LAPS brings to the desk is the power to retailer native administrator passwords in both Energetic Listing or Azure AD. Microsoft can even assist storing encrypted passwords in your on-prem Energetic Listing (operating on the 2016 area practical stage or above), however not Azure AD. This closes a significant safety hole in legacy LAPS for these utilizing Energetic Listing. Fashionable LAPS additionally helps backing up AD’s Listing Providers Restore Mode (DSRM ) password, a key credential for performing catastrophe restoration on Energetic Listing, however one that’s hardly ever used and subsequently straightforward to neglect, significantly in enterprise environments.
Like legacy LAPS, a lot of the configuration of the trendy implementation on Energetic Listing includes administration of Group Coverage objects, however in fact with new options there are new settings. One new setting means that you can specify the consumer or group that may decrypt passwords. If this setting isn’t configured solely members of the area admins group in the identical area as the pc can view passwords. The Azure AD implementation is clearly fairly the paradigm shift, however likelihood is for those who’re going that route, you’ve seemingly already invested in Azure AD and the complexities of managing system insurance policies by means of the Microsoft cloud.
One final new characteristic is the power to configure LAPS to mechanically deal with a password reset after an area administrator account is used. This characteristic is meant to restrict the injury if an area administrator account turns into compromised and includes the configuration of two Group Coverage settings, although a malicious consumer that positive aspects administrative privileges can interrupt these actions.
The post-authentication actions setting means that you can set off a easy password reset, a password set and a pressured sign-out of the consumer, or a password reset and a reboot of the pc. Every of those choices have their place in numerous eventualities. The second setting means that you can configure a reset delay of as much as 24 hours (with a worth of 0 disabling the characteristic altogether).
Copyright © 2022 IDG Communications, Inc.










