Phishing, misconfigurations and lacking patches are prime issues amongst safety leaders, however in addition they say their organizations are letting observability instruments collect rust.

Content material supply, safety and cloud providers firm Akamai, in partnership with U.S. cybersecurity coaching firm SANS Institute, launched on Tuesday the outcomes of a brand new examine inspecting essentially the most worrisome safety dangers associated to APIs. The 2023 SANS Survey on API Safety discovered that the highest danger is phishing assaults.
As well as, the 2023 world survey, which polled 231 utility safety professionals, discovered that fewer than 50% of respondents have API safety testing instruments in place and solely 29% have API discovery instruments. It additionally discovered that solely 29% of respondents use the API safety controls which are already included in DDoS and cargo balancing providers.
Soar to:
Prime six API safety dangers
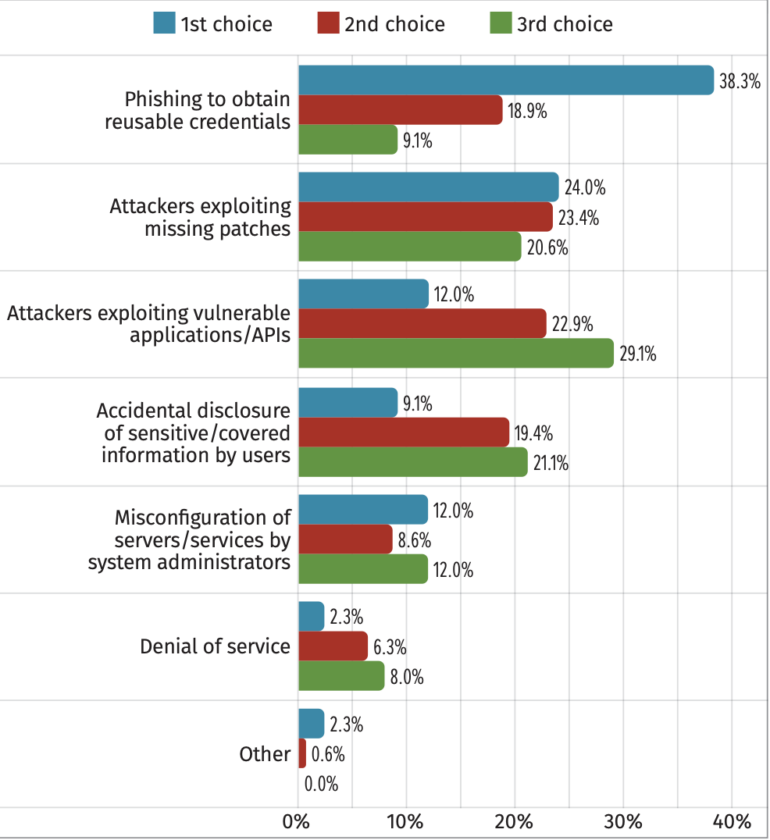
When requested what they perceived as the highest API safety danger, respondents most frequently stated:
- Phishing to acquire reusable credentials (38.3%).
- Attackers exploiting lacking patches (24%).
- Attackers exploiting weak purposes/APIs (12%).
- Misconfiguration of servers/providers by system directors (12%)
- Unintended disclosure of delicate/lined info by customers (9.1%).
- Denial of service (2.3%) (Determine A).
Determine A
API proliferation makes safety challenges extra complicated
Akamai reported earlier this 12 months that 2022 broke data for utility and utility programming interface assaults. A part of the issue is the sheer variety of APIs in use by organizations, which is a matter that matches properly into the “you don’t know what you don’t know” danger bucket.
John Pescatore, director of rising safety tendencies at SANS and writer of the 2023 examine, identified that the proliferation of APIs is emblematic of how complexity is the enemy of safety. He additionally defined how the very nature of distributed purposes will increase the menace floor for attackers and the probability of vulnerabilities being a part of manufacturing code.
Within the new examine, Akamai cites a report by 451 Analysis that states the common enterprise has greater than 15,000 APIs in use. To provide a way of the quantity of assaults, Akamai earlier this 12 months reported that on sooner or later, Oct. 8, 2022, there have been 161 million API assaults worldwide.
SEE: The C-suite considers API safety a prime concern (TechRepublic)
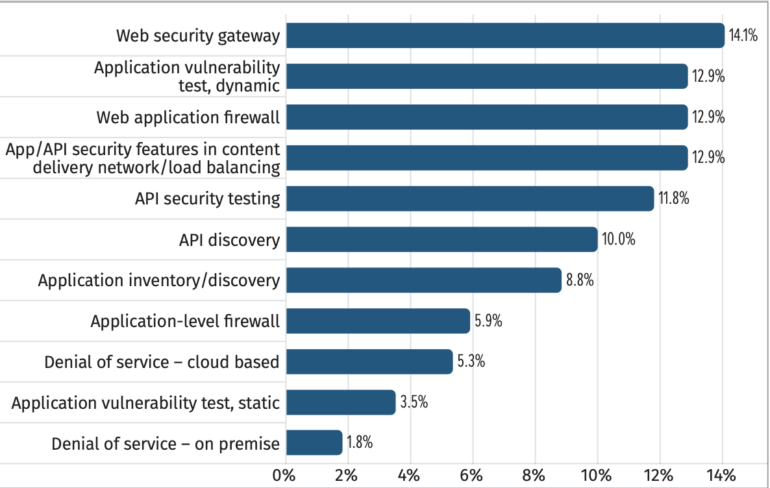
In response to the report, the survey’s respondents stated they deliberate to shut API safety gaps sooner or later with:
- Net safety gateways (14%).
- API safety features in content material supply community/load balancing (13%).
- Net utility firewalls (13%).
- Dynamic utility safety testing (13%) (Determine B).
Determine B
Zero-day dangers getting an excessive amount of credence, misconfiguration not sufficient
The Akamai examine means that respondents are giving too little weight to the chance of misconfigured purposes and an excessive amount of to zero-day dangers, based on Rupesh Chokshi, normal supervisor of utility safety at Akamai.
“A corporation’s API safety plan ought to embrace constructing safe APIs and configuring purposes appropriately. On the similar time, organizations ought to perceive zero-day dangers, comparable to how APIs turn into weak and prone to exploitation. The excellence is necessary as a result of it reveals that sturdy API safety wants to offer vital weight to each side of the API lifecycle; in any other case, vulnerabilities might be missed,” stated Chokshi.
Closing the door to utility layer misconfigurations
Ory Segal, chief expertise officer of Palo Alto Networks Prisma Cloud, concurred that misconfiguration in trendy, cloud-native purposes poses a considerable danger that’s incessantly underplayed by organizations.
“Sadly, many focus their consideration in the direction of zero-day dangers and recognized vulnerabilities in open supply software program packages (i.e., widespread vulnerabilities and exposures). Nevertheless, statistics and actuality present that attackers usually tend to exploit utility layer misconfigurations, exposing organizations to vital danger and potential information breaches — simply take a look at the variety of current breaches involving publicly open cloud storage buckets.”
Amongst Segal’s suggestions:
- For expediting configuration administration, infrastructure as code scanning can present consistency in configuration and scale back human error.
- Bettering API observability is important. This may be achieved by implementing sturdy logging and monitoring.
- Detailed logs, together with API calls, response instances and error messages, can provide invaluable insights into the efficiency and safety of APIs.
- Automated anomaly detection can help in figuring out uncommon actions indicative of a possible assault.
- For extra complete API safety, adopting the precept of least privilege is advisable, permitting every consumer solely the minimal ranges of entry essential to carry out their duties.
- Common audits and automatic testing for widespread safety points, comparable to injection-based assaults, may also help guarantee the continued safety of APIs.
Correct API hygiene: Inventories, patches, menace evaluation
Pescatore wrote that a company’s API safety plan ought to embody:
- Stock of APIs in use and processes that use these APIs.
- Vulnerability evaluation of APIs in use.
- Menace evaluation of energetic assaults exploiting these vulnerabilities.
- Danger-based mitigation of important API vulnerabilities.
Sixty-two p.c of respondents to the survey stated they use internet utility firewalls as a part of API danger mitigation, and 79% of survey takers reported coaching improvement employees on utility safety. Additionally, 57% of respondents reported API stock accuracy of between 25% and 75%.
SEE: Gigamon report shines mild on deep observability (TechRepublic)
“Safety hygiene controls like sturdy authentication, asset stock, vulnerability administration and alter management want to handle API safety points,” Pescatore wrote. “Prevention and detection must be upgraded to take care of API-centric assaults, and infrastructure providers (comparable to content material supply networks and denial of service filtering) must be put to work as properly.”










