In a nutshell: Almost 1.3 million Android-based TV packing containers throughout 197 nations have reportedly been contaminated by a brand new malware often known as “Vo1d.” Though many of the affected units are working outdated variations of Android, some are powered by comparatively newer variations of the working system.
The malware embeds itself inside the system storage space, permitting it to obtain and set up third-party software program remotely when commanded by an attacker. The origin of the malware is at present unknown, however researchers suspect it might consequence from a previous compromise that exploits working system vulnerabilities to realize root privileges. It might even have originated from unofficial firmware with built-in root entry.
Affected units embrace the R4 TV Field working Android 7.1.2 (Construct NHG47K), the KJ-SMART4KVIP powered by Android 10.1 (Construct NHG47K), and TV Field fashions with Android 12.1 (Construct NHG47K).
In all these instances, the Android variations are outdated, probably containing unpatched safety flaws that make them susceptible to malware assaults. Android variations 7.1, 10.1, and 12.1 have been launched in 2016, 2019, and 2022, respectively.
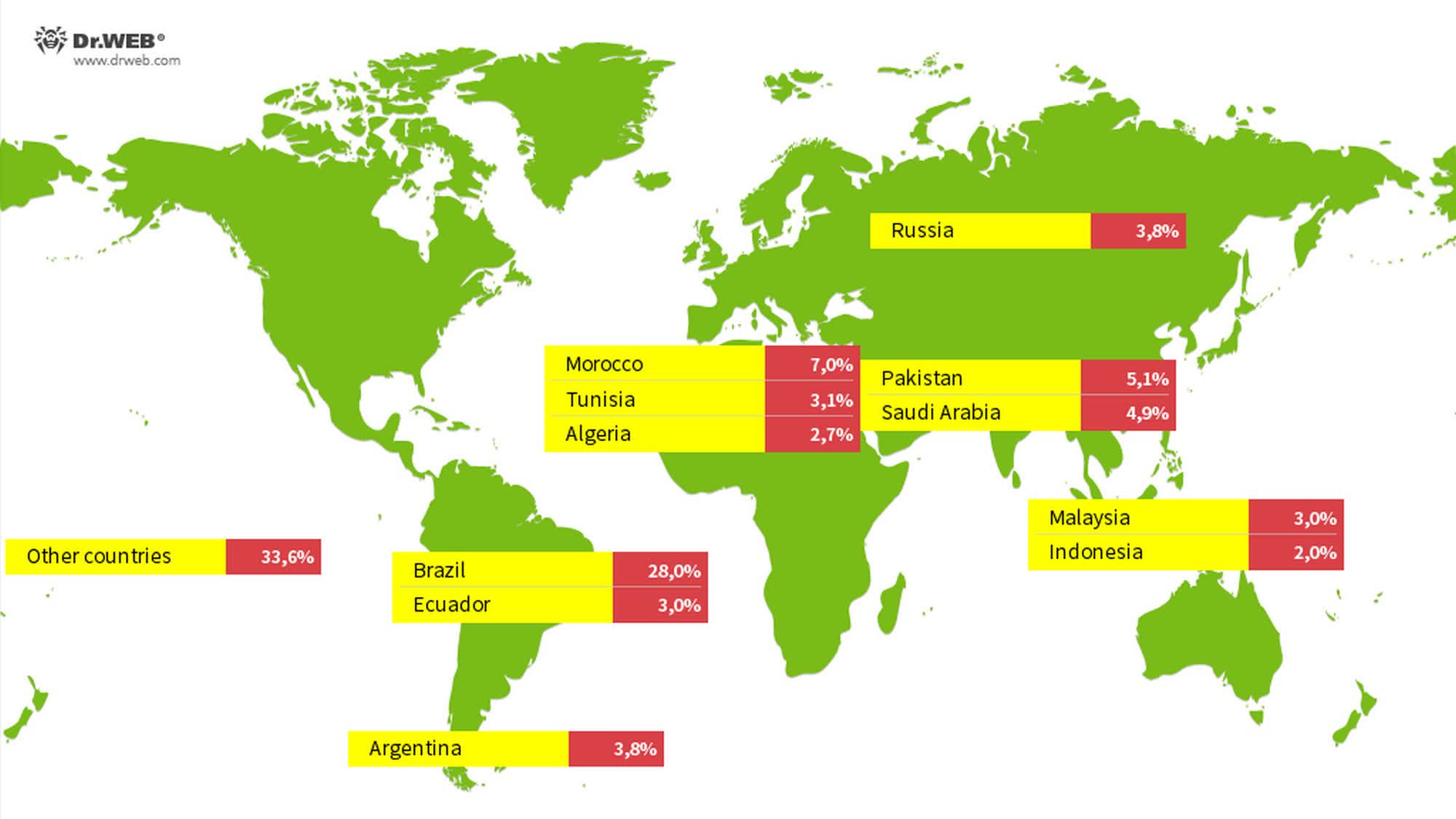
Whereas the Vo1d malware has been detected in almost each nation worldwide, the best variety of infections have been reported in Brazil, Morocco, Pakistan, Saudi Arabia, Russia, Argentina, Ecuador, Tunisia, Malaysia, Algeria, and Indonesia. Brazil is the toughest hit, with roughly 28 % of contaminated units believed to be in use within the nation.
Google clarified that Vo1d malware solely impacts units working the Android Open Supply Venture (AOSP) and never its proprietary Android TV software program. Google additionally identified that not one of the affected units are Play Defend-certified, which means they didn’t endure its in depth safety and compatibility assessments designed to make sure high quality and person security.
Play Defend is a Google service that performs security checks on apps earlier than they’re downloaded from the Play Retailer. It additionally scans units for potential malware from third-party app shops and sideloaded APKs. If dangerous apps are detected, Play Defend deactivates them and notifies the person. Moreover, it could stop the set up of unverified apps, particularly these requesting delicate machine permissions generally focused by scammers to commit fraud.










