
New malware dubbed Meduza Stealer can steal info from a lot of browsers, password managers and cryptocurrency wallets, based on a report from cybersecurity firm Uptycs. The malware was developed to focus on Home windows working techniques.
Uptycs analysis signifies that “no particular assaults have been attributed thus far” although, most likely as a result of Meduza Stealer is new malware. It’s extremely suspected that Meduza Stealer is unfold by way of the standard strategies used for info stealers, corresponding to compromised web sites spreading the malware and phishing emails.
Study what occurs when Medusa Stealer is launched, how the malware is being promoted to cybercriminals and tips about defending your organization from this cybersecurity risk.
Bounce to:
What occurs when Meduza Stealer is launched?
As soon as Meduza Stealer is launched, the malware begins checking for its geolocation by utilizing the Home windows GetUserGeoID operate. This operate appears for a rustic worth primarily based on the system’s settings and never actual geolocation info. The malware stops working if the consequence signifies one in every of these 10 nations: Russia, Kazakhstan, Belarus, Georgia, Turkmenistan, Uzbekistan, Armenia, Kyrgyzstan, Moldova and Tajikistan.
The following step for the malware consists of checking if it may well attain the attacker’s server earlier than beginning to accumulate fundamental info on the contaminated system, corresponding to pc title, CPU/GPU/RAM/{Hardware} particulars, working system model’s exact construct particulars, time zone and present time, username, public IP tackle, execution path and display decision. Meduza Stealer additionally makes a screenshot. Then, the malware is prepared for its stealing operations (Determine A).
Determine A
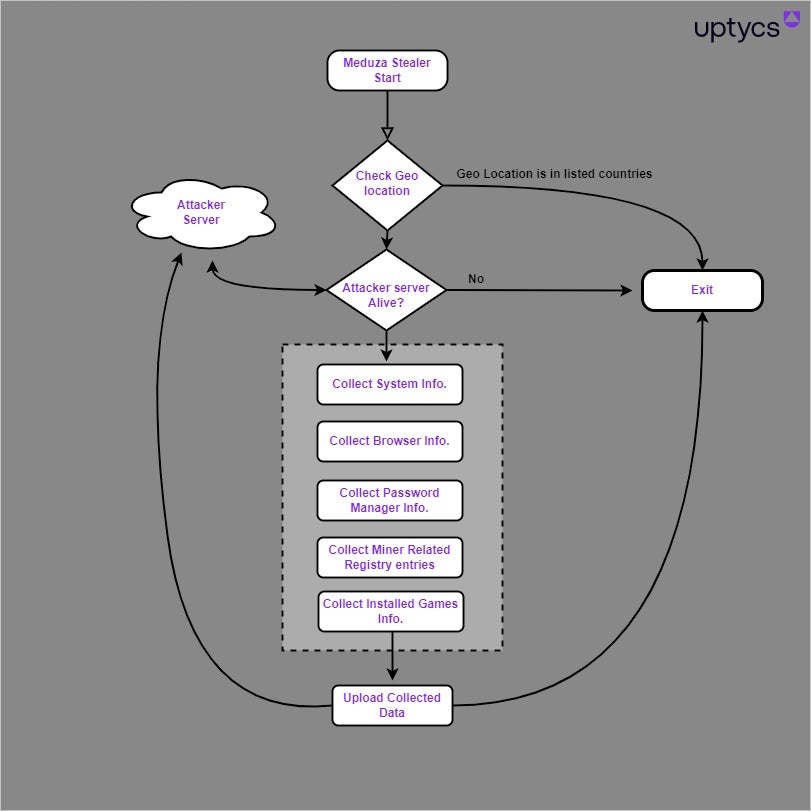
Meduza Stealer’s huge theft capabilities
Browsers
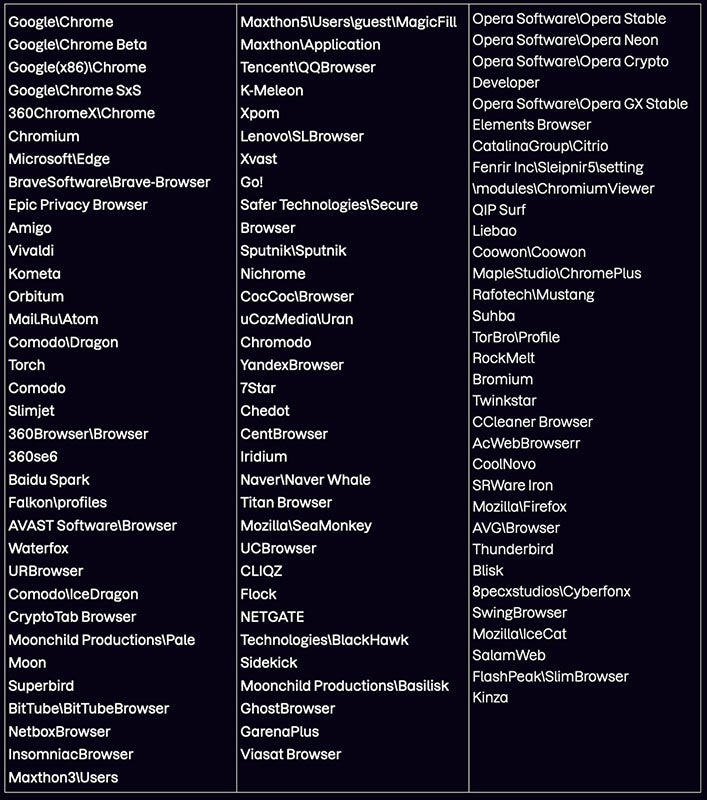
Meduza Stealer hunts for knowledge within the Consumer Information folder; it’s trying to find browser-related info such because the browser historical past, its cookies, login and internet knowledge. An inventory of 97 browser variants is embedded within the malware, exhibiting an enormous effort to not miss any knowledge from browsers (Determine B). Chrome, Firefox and Microsoft Edge are simply three of the browsers on the listing.
Determine B
Password managers
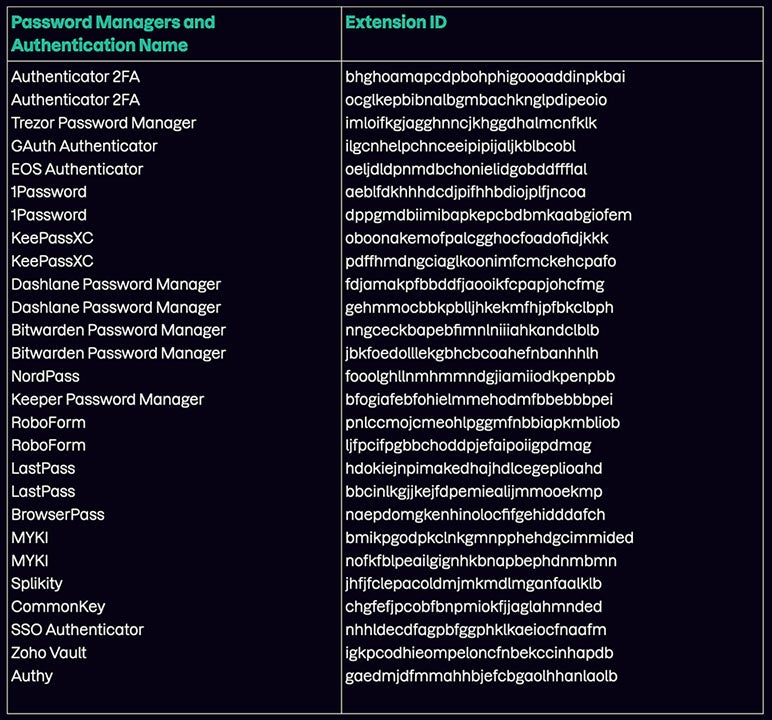
Nineteen password managers are focused by Meduza Stealer primarily based on their Extension ID (Determine C). LastPass, 1Password and Authy are simply three of the password managers listed.
Determine C
The malware particularly targets extensions related to two-factor authentication and password managers with the intention of extracting knowledge; these extensions possess vital info and will include vulnerabilities. By means of having access to 2FA codes or exploiting weaknesses in password supervisor extensions, the attacker may be capable to evade safety protocols and obtain unauthorized entry to consumer accounts.
Cryptocurrency wallets
There are 76 cryptocurrency wallets at the moment focused by Meduza Stealer.
From Uptycs Menace Analysis, “The malware makes an attempt to extract cryptocurrency pockets extensions from internet browsers by way of software program plugins or add-ons that allow customers to conveniently handle their cryptocurrency belongings instantly inside internet browsers like Chrome or Firefox. These extensions present performance for duties corresponding to monitoring account balances, conducting cryptocurrency transactions particulars.”
The malware will get configuration and associated knowledge from completely different Home windows Registry keys:
- HKCUSOFTWAREEtherdyneEtherwallgeth
- HKCUSOFTWAREmonero-projectmonero-core
- HKCUSOFTWAREDogecoinCoreDogecoinCore-Qt
- HKCUSOFTWAREBitcoinCoreBitcoinCore-Qt
- HKCUSOFTWARELitecoinCoreLitecoinCore-Qt
- HKCUSOFTWAREDashCoreDashCore-Qt
Extra functions focused
The Telegram Desktop software is being scanned by the malware, which appears for entries within the Home windows registry which might be particular to this software.
The malware additionally appears for the Steam gaming system software knowledge that could be saved within the Home windows registry. If Steam is put in on the pc, the info that may be fetched from it consists of login knowledge, session info, user-specific settings and different configuration knowledge.
Discord is one other software focused by the malware, which accesses the Discord folder and collects info corresponding to configuration and user-specific knowledge.
How Meduza Stealer is promoted to cybercriminals
In keeping with Uptycs researchers, the administrator of Meduza Stealer has been utilizing “refined advertising and marketing methods” to advertise the malware on a number of cybercriminal marketplaces and boards.
For starters, the actor doesn’t hesitate to supply display captures of a big portion of antivirus software program detection outcomes, exhibiting that just one antivirus answer (ESET) out of 26 detect it, whether or not that’s statically or dynamically.
To draw extra clients, entry to stolen knowledge is obtainable by means of an online panel (Determine D). Totally different subscription choices are proven to the potential buyer: one month for $199 USD, three months for $399 USD or a lifetime plan.
Determine D
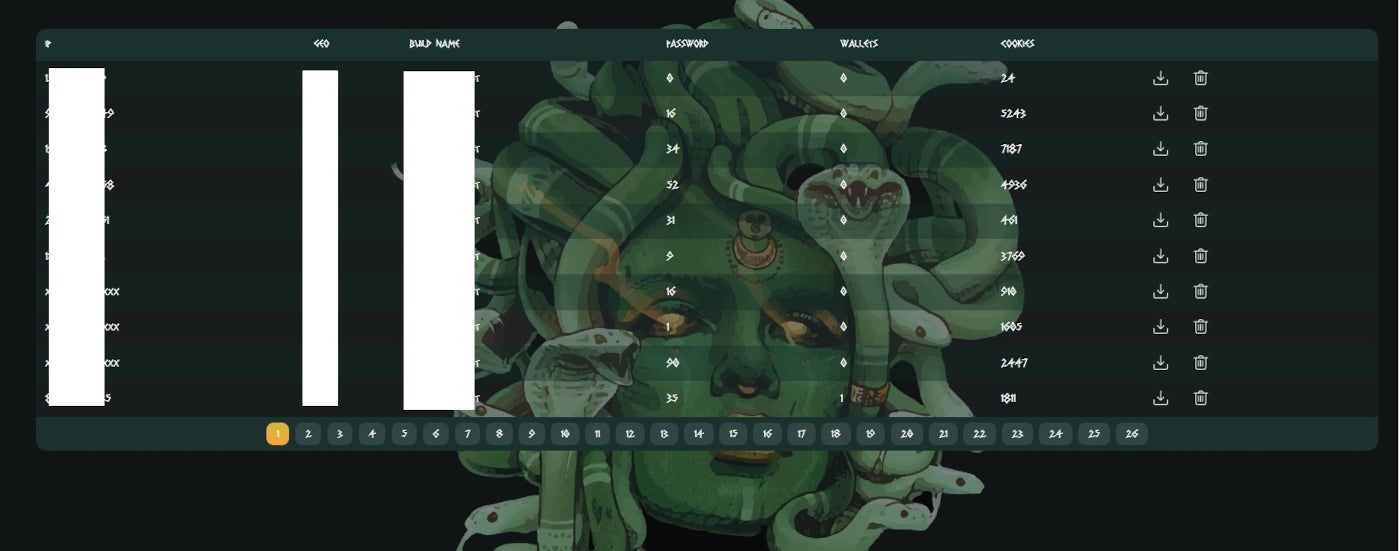
As soon as the consumer has subscribed, the particular person has full entry to the Meduza Stealer internet panel, which gives info corresponding to IP addresses, pc names, nation title, rely of saved passwords, wallets and cookies on contaminated computer systems. Then, the subscriber can obtain or delete the stolen knowledge instantly from the online panel. This unprecedented characteristic could be very helpful as a result of the info deletion ensures that no different subscriber will be capable to use that info as a result of it’s instantly taken off.
Easy methods to keep secure from this cybersecurity risk
It’s strongly suggested to have all working techniques and software program updated and patched to keep away from being compromised by a typical vulnerability. Browsers, particularly, have to be updated; additionally, run as few plugins as doable to cut back the assault floor.
It’s additionally suggested to deploy multifactor authentication the place doable so an attacker can’t acquire entry to company assets, even when they’re in possession of legitimate credentials.
Safety options have to be deployed on endpoints and servers, with monitoring capabilities to detect threats. It’s additionally suggested to run YARA detection guidelines on company endpoints, such because the one offered by Uptycs to detect the Meduza Stealer.
Disclosure: I work for Development Micro, however the views expressed on this article are mine.

/cdn.vox-cdn.com/uploads/chorus_asset/file/23985506/acastro_STK024_02.jpg)








