This assault despatched roughly 120,000 phishing emails to organizations worldwide with the purpose to steal Microsoft 365 credentials.

New analysis from Proofpoint exposes a brand new large credential phishing assault marketing campaign geared toward top-level executives in additional than 100 organizations worldwide. This cybersecurity assault leverages the EvilProxy phishing package and bypasses two-factor authentication.
We break down the specifics of EvilProxy, together with which accounts have been focused, and supply tips about defending your small business from this menace.
Soar to:
What’s EvilProxy?
EvilProxy is a phishing-as-a-service package that was first uncovered by cybersecurity firm Resecurity in September 2022. This package has the power to run phishing assaults with reverse proxy capabilities that allow it to steal credentials and bypass 2FA by deploying adversary-in-the-middle methods (Determine A).
Determine A
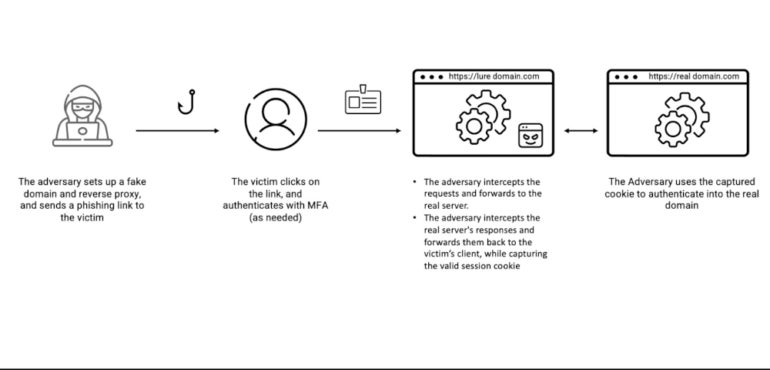
Any cybercriminal can purchase EvilProxy and begin utilizing it by way of a easy interface that permits the creation of phishing campaigns with customizable choices. The service units up a phishing web site in response to the chosen choices and is then able to go. When an unsuspecting person visits the phishing web page, they supply their credentials. The phishing web page then asks for the 2FA code for authentication to the service. As soon as offered, the code is straight away utilized by the package to get entry to the person’s account by opening a session.
Daniel Blackford, menace researcher at Proofpoint, informed TechRepublic that EvilProxy is bought in underground boards and Telegram channels, and added that “The essential model of EvilProxy prices a couple of hundred {dollars}, but it surely depends upon many parameters like: characteristic set, variety of focused customers, and so forth.”
EvilProxy assault chain
The assault marketing campaign begins with emails pretending to return from recognized and trusted companies or manufacturers resembling DocuSign, Adobe or Concur. The emails comprise a malicious hyperlink main the person to an open redirection at a official web site resembling YouTube or Slickdeals (Determine B) in an try and keep away from detections on the electronic mail degree.
Determine B

A sequence of redirecting web sites (Determine C) comply with in an unpredictable method, aiming to decrease the possibilities of discovery. The person lands on the EvilProxy phishing web site, which on this marketing campaign is a Microsoft login web page functioning as a reverse proxy.
Determine C
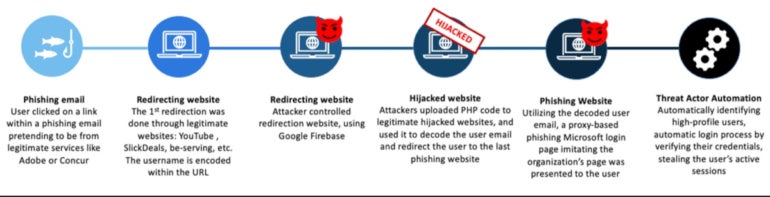
To cover the e-mail tackle of the sufferer whereas doing the redirections and keep away from automated scanning instruments detections, the attackers use a particular encoding and solely use compromised official web sites to add their PHP code to decode the e-mail tackle earlier than touchdown on the EvilProxy phishing web page.
1000’s of high-value Microsoft cloud accounts focused
This assault marketing campaign despatched roughly 120,000 phishing emails to a whole bunch of focused organizations worldwide between March and June 2023, with the purpose to steal customers’ Microsoft 365 cloud credentials.
In keeping with Proofpoint, the checklist of focused customers contains many high-value targets resembling vice presidents and C-level executives from main corporations. The attackers ignored workers in decrease positions. As acknowledged by the researchers, it appears cheap to suppose the menace actor used organizational data acquired from public sources to kind out who could be fascinating.
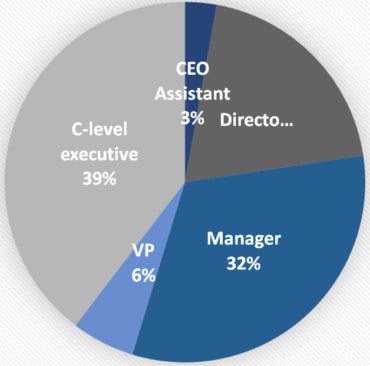
Statistics amongst a whole bunch of compromised customers reveal that 39% have been C-level executives, of which 17% have been chief monetary officers and 9% have been presidents and chief govt officers. Managers have been 32% of the compromised customers (Determine D).
Determine D
Oddly, customers with a Turkish IP tackle have been redirected to the official net web page, which suggests the menace actor would possibly come from that nation or is actively ignoring any Turkish person account. Quite a few digital personal community IP addresses have been additionally redirected to the official web site as a substitute of the EvilProxy web page.
Whereas the purpose of this assault marketing campaign stays unknown, this sort of assault usually results in monetary fraud or delicate information exfiltration. The menace actor may also promote entry to those high-value mailboxes to different cybercriminals.
Sustaining fraudulent entry to the mailboxes
As soon as an energetic session is established on a compromised account, the menace actor provides its personal multifactor authentication technique within the Microsoft 365 parameters, including Authenticator App to it (Determine E).
Determine E
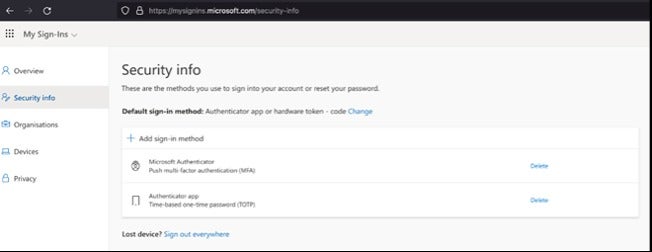
Afterward, the menace actor now not wants EvilProxy’s reverse proxy characteristic to log in to the compromised account and easily logs in with the credentials and a code offered on their very own Authenticator utility.
How you can defend from this safety menace
Listed here are 4 ideas for safeguarding in opposition to the EvilProxy menace.
- Use electronic mail safety options to dam malicious emails despatched to workers.
- Practice workers to detect such phishing assaults.
- Deploy community safety options to attempt to detect phishing, malware or different threats.
- Run phishing assault simulations to assist IT increase consciousness amongst workers.
It’s additionally suggested to make use of FIDO2-based bodily keys when doable as a result of that type of {hardware} securely shops a personal key that isn’t usually accessible to the attacker, even when the particular person is intercepting all communications between the person’s gadget and the net service.
Disclosure: I work for Pattern Micro, however the views expressed on this article are mine.










