Microsoft has already seen hundreds of thousands of phishing emails despatched day-after-day by attackers utilizing this phishing equipment. Learn to shield what you are promoting from this AitM marketing campaign.

New analysis from Microsoft’s Risk Intelligence staff uncovered the actions of a menace actor named DEV-1101, which began promoting for an open-source phishing equipment to deploy an adversary-in-the-middle marketing campaign.
In accordance with Microsoft, the menace actor described the equipment as a phishing utility with “reverse-proxy capabilities, automated setup, detection evasion by an antibot database, administration of phishing exercise by Telegram bots, and a variety of ready-made phishing pages mimicking companies corresponding to Microsoft Workplace or Outlook.”
SEE: Phishing assaults: A information for IT professionals (free PDF) (TechRepublic)
Microsoft makes use of DEV adopted by a quantity as a brief title for an unknown, rising or growing cluster of menace exercise. After there may be sufficient knowledge and excessive confidence in regards to the origin or id of the menace actor, it’s given an actual menace actor title.
Bounce to:
What’s an adversary-in-the-middle phishing assault?
In an adversary-in-the-middle phishing assault, a nasty actor intercepts and modifies communications between two events, sometimes a person and a web site or service, to steal delicate or monetary data, corresponding to login credentials and bank card knowledge.
An AitM marketing campaign is harder to detect than different kinds of phishing assaults as a result of it doesn’t depend on a spoofed electronic mail or web site.
How these phishing kits are used
The phishing kits have been used with a number of approaches.
One method, defined by the researchers, is what was utilized by DEV-0928, one other menace actor tracked by Microsoft. DEV-0928 begins the assault by sending an electronic mail to the goal (Determine A).
Determine A
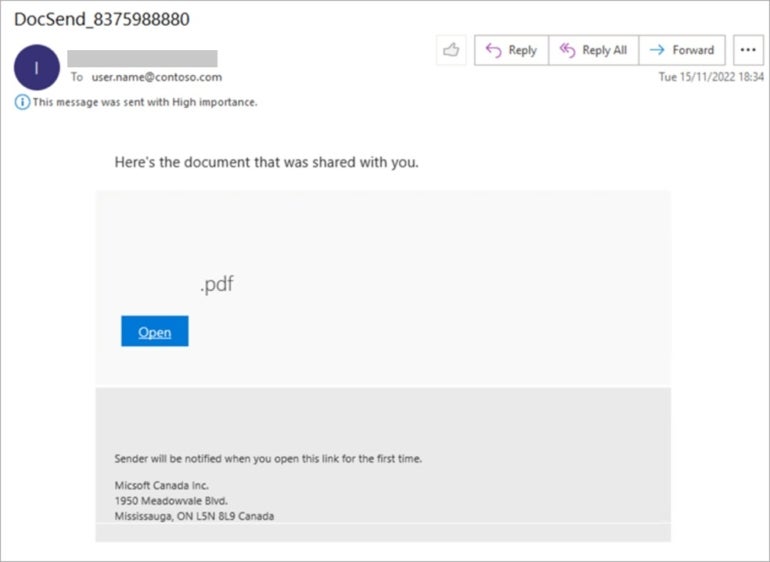
When the person clicks the Open button, the antibot functionalities of the phishing equipment come into motion. If a bot is detected, the phishing equipment would possibly present a redirection to any benign web page configured by the attacker — the default one is instance.com.
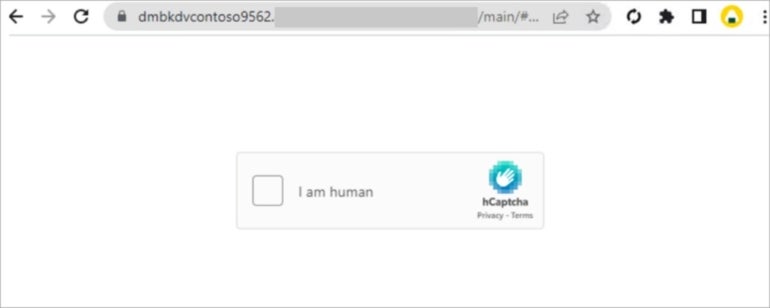
One other approach may be to launch a CAPTCHA request to evade detection and guarantee an actual person is behind the press (Determine B).
Determine B
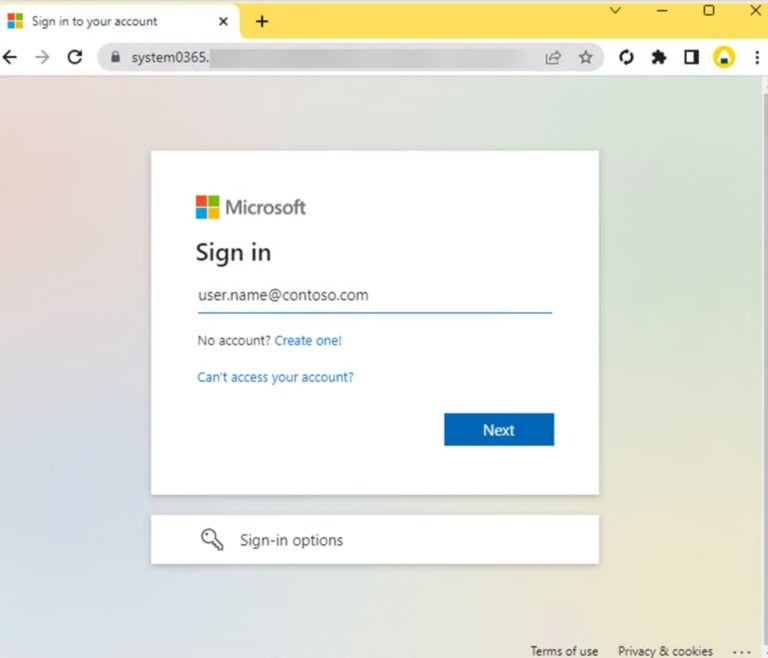
The person is proven a phishing web page hosted by an actor-controlled server (Determine C).
Determine C
How AiTM campaigns bypass multi-factor authentication
If the person has offered the phishing web page with their credentials and enabled multi-factor authentication to log in to their actual account, the phishing equipment stays in perform to activate its MFA bypass capabilities. The phishing equipment acts as a proxy between the person and the reliable service.
The phishing equipment logs in to the reliable service utilizing the stolen credentials, then forwards the MFA request to the person, who gives it. The phishing equipment proxies that data to the reliable web site, which returns a session cookie that can be utilized by the attacker to entry the reliable service because the person.
Potential impression of this phishing equipment
Microsoft has noticed hundreds of thousands of phishing emails despatched day-after-day by attackers utilizing this equipment, however its diffusion may be even bigger. The truth is, any attacker would possibly subscribe to the phishing equipment license and begin utilizing it. Whereas electronic mail might be the commonest methodology of reaching victims, attackers may also deploy it by way of prompt messaging, social networks or any channel they may goal.
Rising value of the phishing equipment
The menace actor began promoting the equipment on a cybercrime discussion board and on a Telegram channel round June 2022 and introduced a value of $100 USD for a month-to-month licensing payment. As a result of improve of attackers within the service, the value reached $300 USD in December 2022, with a VIP license supply for $1,000 USD.
How one can shield from this AitM menace
- All the time deploy and preserve MFA when doable: Whereas strategies such because the adversary-in-the-middle nonetheless permit bypassing MFA, it’s a good measure that makes it extra advanced to steal entry to person accounts or companies.
- Allow conditional entry and Azure AD safety defaults: Microsoft recommends utilizing safety defaults in Azure AD as a baseline set of insurance policies and enabling conditional entry insurance policies, which permit the analysis of sign-in requests based mostly on a number of components such because the IP location data, the system standing and extra.
- Deploy safety options on the community: This may assist detect phishing emails on electronic mail servers in addition to any malware or fraud try on all the opposite elements of the community.
- Hold software program and working methods updated: Protecting software program up-to-date and patched will assist to keep away from falling for frequent vulnerabilities. To assist with this step, contemplate downloading this patch administration coverage from TechRepublic Premium.
- Educate customers about laptop safety and cybercrime: Present worker coaching with a deal with phishing, as it’s the commonest approach to goal customers with malware and fraud. To assist with this step, contemplate downloading this safety consciousness and coaching coverage from TechRepublic Premium.
Learn subsequent: For credentials, these are the brand new Seven Commandments for zero belief (TechRepublic)
Disclosure: I work for Development Micro, however the views expressed on this article are mine.

/cdn.vox-cdn.com/uploads/chorus_asset/file/24531101/PasskeyAndroid_3x2_LQ.jpg)








