New proof reveals that Iran’s intelligence and army companies are related to cyber actions focusing on Western international locations via their community of contracting firms.
A string of multi-year leaks and doxxing efforts led by anti-Iranian authorities hacktivists and dissident networks has uncovered an intricate internet of entities related to the Islamic Revolutionary Guard Corps (IRGC) concerned in cyber-attacks and data manipulation campaigns.
Cyber risk intelligence supplier Recorded Future mentioned a few of the findings in a brand new report, revealed on January 25, 2024.
It has been discovered that not less than 4 intelligence and army organizations linked to the IRGC have interaction with the majority of cyber contracting events. These embody:
- IRGC’s Digital Warfare and Cyber Protection Group (IRGC-EWCD)
- IRGC’s Intelligence Group (IRGC-IO)
- IRGC’s Intelligence Safety Group (IRGC-IPO)
- RGC’s international operations group, aka the Quds Pressure (IRGC-QF)
“Every physique has had particular superior persistent risk (APT) teams intently related to them; for instance, in 2022, the Nemesis Kitten APT Cobalt Mirage, UNC2448, TunnelVision, and Mint Sandstorm (previously tracked as “DEV0270”) was linked by way of personas to the IRGC-IO by the anti-government group Lab Dookhtegan,” the report defined.
The leaks analyzed by Recorded Future present that these companies preserve a long-standing relationship with Iran-based cyber contractors. Public information additionally level to an ever-growing internet of entrance firms related by way of people identified to serve numerous branches of the IRGC.
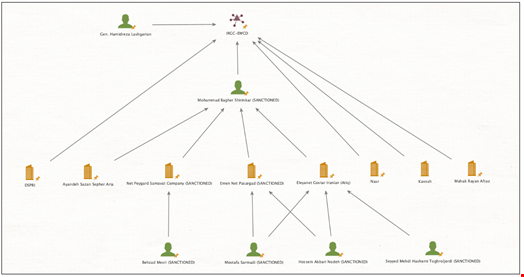
A few of these cyber operators concerned in offensive cyber actions embody “Ayandeh Sazan Sepehr Aria Firm,” “Sabrin Kish,” “Soroush Saman Firm” and different sanctioned entities like “Najee Expertise Hooshmand Fater LLC” and “Emen Internet Pasargad,” Recorded Future reported.
Nonetheless, researchers have seen fixed motion throughout the internet of Iran-based cyber contractors, with firms often disbanding and rebranding in an try to obfuscate their actions.
“We’ve noticed overlaps between personnel members, recurrently known as ‘board members,’ who share roles in numerous contracting firms. Among the information reveals names of high-ranking IRGC officers purportedly chargeable for main and coordinating Iran’s offensive cyber ecosystem,” Recorded Future researchers wrote.
Concerned within the 2020 US Presidential Election Manipulation Campaigns
Via their hyperlinks with these cyber contractors, the abovementioned Iranian authorities companies are related to, if circuitously complicit in, the focusing on of main US monetary establishments, industrial management techniques (ICS) within the US and around the globe, and ransomware assaults in opposition to numerous industries, together with healthcare suppliers like kids’s hospitals.
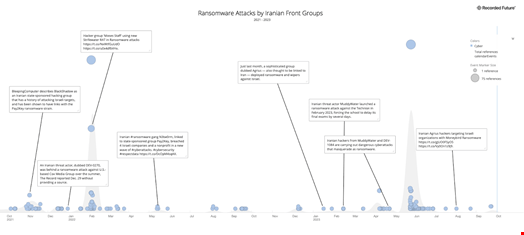
Additionally they mix info operations with cyber intrusions to foment instability in goal international locations. As an illustration, a few of these contractors had been concerned in focusing on the 2020 US presidential election.
Lastly, it has been proven that a few of these contractors export their applied sciences overseas, each for surveillance and offensive functions.
The leaks present that IRGC-related cyber offensive infrastructure has been used to deploy financially motivated assaults, for instance.
Lastly, based mostly on these leaks, Recorded Future researchers concluded that US authorities sanctions are probably proving to be an efficient authorized and diplomatic software, making it tougher for cyber firms underneath the IRGC umbrella to evade detection.
“It’s probably these efforts additionally adversely have an effect on contractors’ talents to overtly recruit new and expert labor,” reads the report.
Learn extra: Iranian Menace Group Hits 1000’s With Password Spray Marketing campaign

/cdn.vox-cdn.com/uploads/chorus_asset/file/24418649/STK114_Google_Chrome_02.jpg)








