A brand new malware is bypassing an Android 13 safety measure that restricts permissions to apps downloaded out of the reliable Google Play Retailer.
A brand new report from ThreatFabric, a fraud safety firm, exposes SecuriDropper malware, which is able to bypassing Android 13 restricted settings. The malware makes Android contemplate the set up as coming from the Google Play Retailer, although in actuality it isn’t.
It’s extremely really useful for organizations to make use of Cell Machine Administration options and strategies to allow extra management on staff’ Android gadgets and to limit putting in apps on their gadgets by utilizing an inventory of permitted purposes and forbidding every other.
Bounce to:
What are Android 13’s restricted settings?
Android 13 launched a brand new safety function known as restricted settings. This new function prevents sideloaded purposes (i.e., downloaded out of the Google Play Retailer) from immediately requesting accessibility settings and notification listener entry — two options which are usually abused by malware based on ThreatFabric’s researchers.
On Android methods, purposes downloaded from the reliable Google Play Retailer aren’t topic to the identical course of as these not originating from it. The primary cause why is that purposes which have made it efficiently to the Google Play Retailer have supplied extra data and visibility and have handed totally different safety checks to make sure they don’t comprise malware functionalities. Due to this fact, purposes from the Google Play Retailer aren’t involved by the restricted settings function.
Functions downloaded from the Play Google Retailer use a particular set up methodology — a “session-based” bundle installer — that isn’t usually utilized by sideloaded purposes.
Meet SecuriDropper malware
The SecuriDropper malware makes use of the identical set up methodology as reliable software program from the reliable Google Play Retailer. After being executed by the unsuspecting person, the malware requests two key permissions: Learn & Write Exterior Storage and Set up & Delete Packages.
As soon as permissions are given, the malware checks if it already exists on the machine; if it does, the malware runs, and if it doesn’t, the malware reveals the person a message telling them one thing went mistaken and the person must click on a reinstall button. The message is totally different based mostly on the machine’s location and language configured.
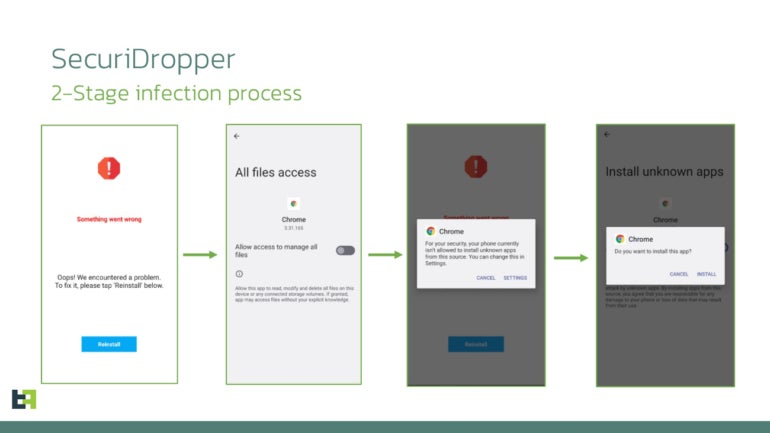
When carried out, the session-based set up begins, and the person is requested for permission to allow the Accessibility Service, which turns into potential because of the bypass of the restricted settings function (Determine A).
Determine A
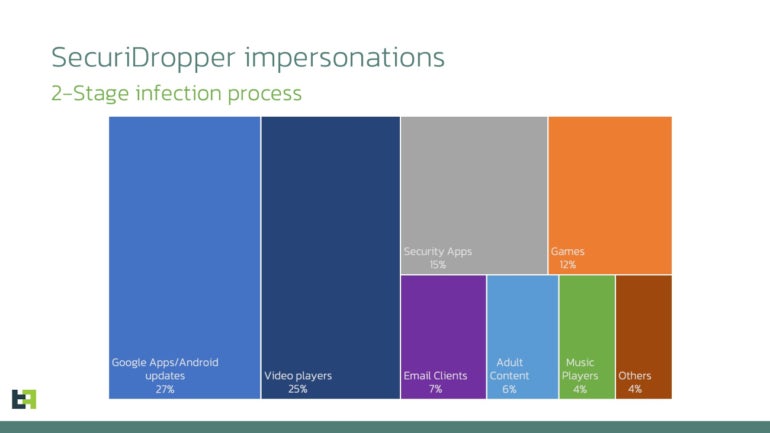
The malware has been noticed disguising itself as numerous Android purposes corresponding to Google Apps or Android updates (27%), video gamers (25%), safety purposes (15%) or video games (12%), adopted by e mail purchasers, grownup content material, music gamers and different apps (Determine B).
Determine B
SecuriDropper’s numerous last payloads
Any form of malicious code may very well be dropped and put in by SecuriDropper, because the malware’s last aim is to put in different malware on contaminated gadgets. ThreatFabric noticed two campaigns utilizing SecuriDropper.
The primary one is an assault marketing campaign delivering SpyNote, a malware with distant administration software options. The malicious payload was being distributed via phishing web sites and deployed by SecuriDropper. The SpyNote malware, which is ready to seize delicate data on the machine, in addition to steal SMS and name logs and take screenshots, completely wants permissions that may be unavailable attributable to Android’s restricted settings. Its set up by way of SecuriDropper allows the SpyNote malware to maintain infecting gadgets, even on Android 13, with no need to alter its code.
In one other assault marketing campaign, SecuriDropper was noticed putting in the ERMAC banking trojan. The malware was deployed by way of Discord, a communication software beforehand used primarily by avid gamers however more and more utilized by different communities, together with company entities.
Extra malware will use this system
Totally different malware households will use this system sooner or later. One service that’s already utilizing this system is Zombinder.
As reported by ThreatFabric, the DarkNet platform Zombinder began promoting for its new model that bypasses Android 13 restricted settings. The Zombinder service permits an attacker to efficiently bind a reliable software with malware. When the an infection is completed, the reliable software runs usually, whereas the malware is being executed within the background, unnoticed.
Zombinder additionally sells builders with the Android 13 restrictions bypass functionality. The builders from Zombinder are software program able to dropping malware on an contaminated system (aka dropper), offered at $1,000 USD.
As written by ThreatFabric, “the emergence of providers like Zombinder are indications of a booming market in cybercrime, providing builders and instruments for evading Android 13’s defenses. It’s a testomony to the resourcefulness of these searching for to use safety vulnerabilities for his or her achieve.”
Disclosure: I work for Pattern Micro, however the views expressed on this article are mine.










